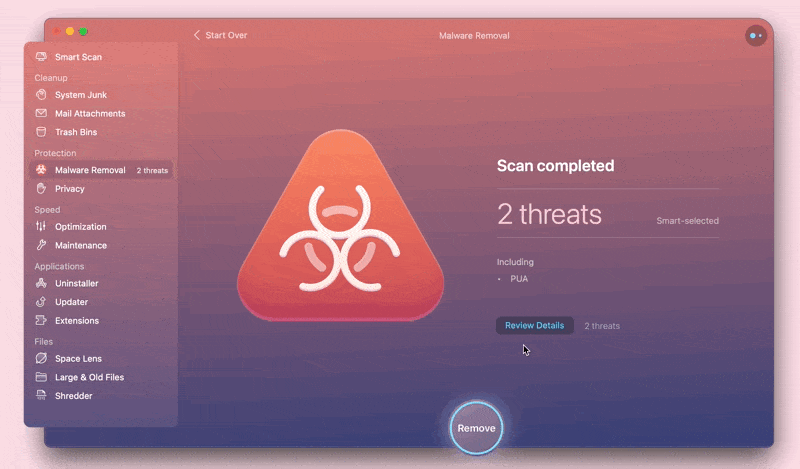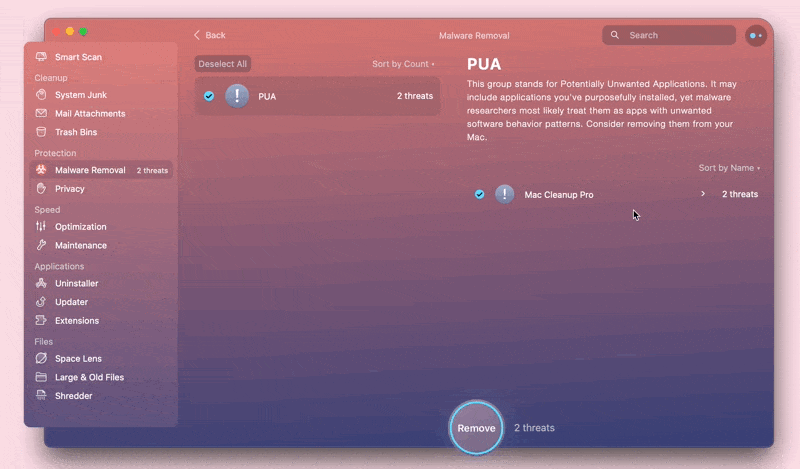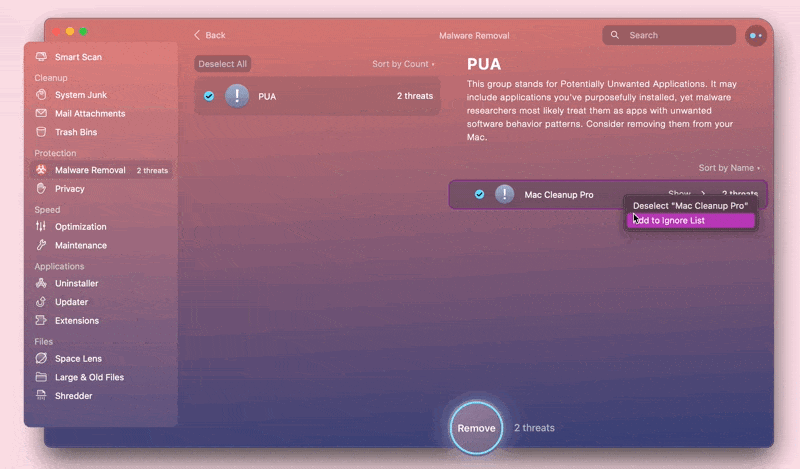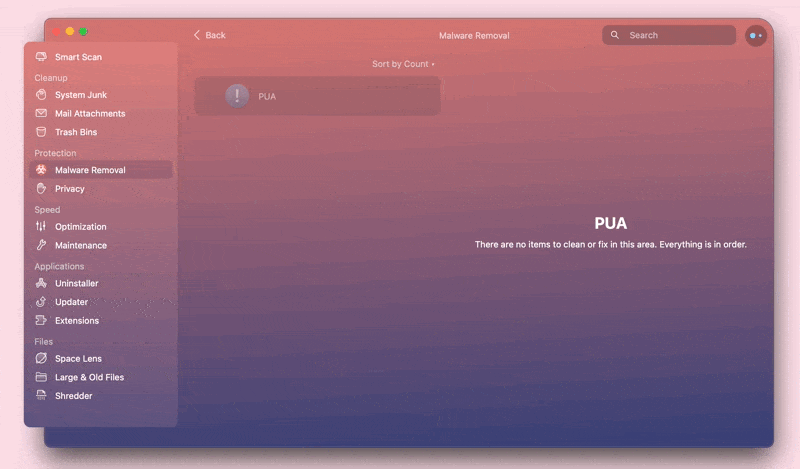
CleanMyMac goes far beyond detecting malware and reveals potential cybersecurity threats too. Our researchers pay special attention to apps that are widely known as “potentially unwanted.”
What is a “potentially unwanted application”?
Unlike malware, “potentially unwanted applications” (PUA), also known as “potentially unwanted programs,” are usually downloaded willingly, can look good, and do some useful stuff. However, they can do harm with their hidden maleficent functionality intended to track online and offline activities, hijack a browser, alter search results, and so on.
How does CleanMyMac identify PUA?
While analyzing a particular application, our malware researchers compare it with unwanted software behavior patterns. If the application works in a “tricky” manner or has some unsafe functionality, it can be identified as a threat.
CleanMyMac considers the following patterns as unwanted:
- Showing undesired, intrusive, and offensive advertisements
- Collecting or sharing private data
- Undesired operations beyond the expected app's functionality
- Improper installation and uninstallation practices
For more information, see "Detailed criteria of identifying PUA."
To be more precise in the analysis and detection of cyber threats, CleanMyMac researchers improve and extend these criteria. However, we realize that there’s always a chance to make false conclusions. So if you have another opinion and solid facts on some apps that CleanMyMac marks as unwanted or malicious, please let us know.
Add apps to the ignore list
If CleanMyMac offers to remove an app you trust, you can add it to the ignore list:
- Control-click the application you want to keep and choose Add to Ignore List.
CleanMyMac won’t show you this app in the scan results anymore.
Detailed criteria of identifying PUA
CleanMyMac considers an application unwanted if it fits any of the following criteria.
1. Advertisement
1.1. Displaying advertisements that interrupt work and cause annoyance (if shown without consent). The ads may display in separate windows, pop-ups, overlays, system alerts and dialogs, or other forms.
1.2. Users can't close an advertisement, or even more ads are shown after dismissing one of them.
1.3. Information in an advertisement exaggerates the software capabilities or doesn't match the declared functionality of the app.
1.4. Advertisement content is obnoxious, deceptive, or abusive.
2. Privacy
2.1. Collecting or transmitting personal data without consent or with violations of the international data protection laws. Personal data may include personally identifiable information (such as name, address, phone number, city of residence, etc.) or other privacy-sensitive data (like credentials, biometrics, credit card number, etc.).
2.2. Requiring additional user information before installation.
3. Unwanted behavior
3.1. Using or modifying third-party apps or processes on users' computers: downloading, installing, launching, hiding, disabling, changing settings, etc.
3.2. Requiring system permissions, unrelated to the app's functionality.
3.3. Modifying the system, user, or security settings on users' computers; changing settings in security software and other unrelated applications.
3.4. Causing negative effect the system performance and reliability, network performance, and user experience.
3.5. Modifying browser settings: changing default search provider or home page, installing plugins, add-ons, toolbars, or helpers without consent, etc.
3.6. Practicing aggressive or deceptive distribution and high-pressure selling.
3.7. Intending to scare or threaten users by using text or visual contents.
3.8. Failing to meet users' expectations regarding the app's functionality.
3.9. Application updates have different functionality than expected from the app or stated during installation.
4. Installation and uninstallation
4.1. Licensing documents are missing or not stated clearly. These documents may include license agreements or policies (software license, EULA), information about brand ownership, etc.
4.2. Installing to an unexpected location.
4.3. Installing other applications (bundled software) without consent.
4.4. Installing functional components that users can't uninstall or remove.
While we bring potentially unwanted software to your attention, it is up to you to decide what to do with such apps. Given the fact that new forms of PUA are constantly emerging and developing, the list above is not exhaustive. We reserve the right to change or update our criteria at any time and without notice; we'll do our best to keep the list above up-to-date.
Stay safe and contact us if you need assistance.
