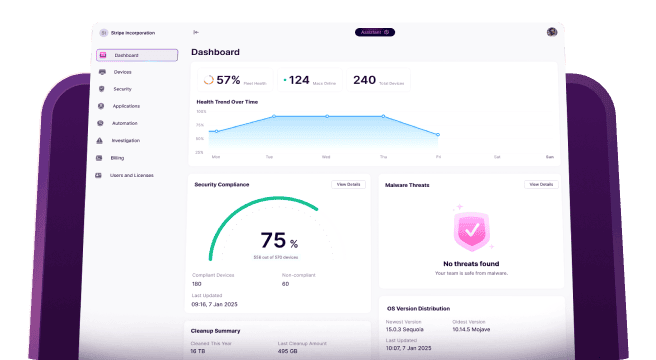
No one shows up to work with the intention of getting hacked. But, unfortunately for small businesses, they are usually easier targets for scammers. Knowing they don’t have the resources or manpower dedicated to keeping their digital records safe. That’s why it’s so critical for every person on your team to be thinking about digital security.
Not sure where to start with all of this? You might be asking, “What is data protection?” Well, you’re in the right place. This article will answer that question and show you why data protection for small business is so important. As a bonus, it will describe some of the best ways to protect business data on Macs.
What is data protection?
Any business operating today is collecting data of some type. Sometimes, it’s from customers, and other times, it’s from employees.
Data protection is exactly what it sounds like. It’s the software and policies you put into place to protect that information. It is about taking steps to safeguard information from unauthorized access to it — either it is corruption or loss — as well as ensuring the capability to restore it in case of necessity.
As a business owner, the last thing you want to be liable for is a data or privacy leak. Having strict policies in place protect you, your company, and, in the long run, everyone who interacts with your business.
Why you need data protection for small business
Let’s start with the easy answer. Depending on where your business is based, you might be required to protect data by law. Many countries are trying to protect their citizens’ privacy by holding companies responsible for the information it collects.
Now, you might be thinking, “I don’t really collect any information from customers.” And that might be true. But even with a service-based company like landscapers or movers, you’re still collecting sensitive information about your employees. You’re getting personal, identifying information, usually for payroll and tax purposes.
So, the question turns into the following one: what data protection solutions are you currently using today and which ones should you put in place?
4 principles for managing business data protection
If you’re not the most technical person or even if you are your company’s technology lead, there are four principles that can help you figure out where you need to start.
1. Analyze workflows
The best place to start is with an understanding of your company’s workflows. Do an audit of every process your teams are doing. Whether it’s hiring and onboarding new employees or how you process credit card transactions. Document where and how you’re collecting data and see how those systems can be better secured.
2. Only keep what you need
You never know when you might need a particular document. But always keeping everything is counter to making sure things are secure. You need to trim the fat, so to speak. Only hang onto the documents that are absolutely critical.
This goes for processes, systems, and especially software, too. Keeping any one of these things around is just one more potential vulnerability. Another way for your company’s data to be compromised.
3. Secure it
The most secure way to store data is to not store any at all. But that’s not a reality. Even if you keep only the most critical data, you do need to keep some pieces of information around to run your business. In fact, it is extremely important if you keep vital information only. So, then it just becomes a question of what steps you can take to make sure it’s secured as much as possible.
Can you set up multi-factor authentication to allow for access? Is there a way to encrypt the data you collect? Does it need to be stored online?
All of these questions are great things to ask yourself as you’re looking at the data. Another point-of-view you should have is to ask where things can escape. Understanding potential vulnerabilities will help you see them before they happen. This way, you can patch up those holes and prevent data breaches.
4. Plan your response
As perfect and air-tight as you try to have your company, something is bound to happen. Similarly to understanding your vulnerabilities, you also need to think through what you’ll do when and if there is a security breach with your business. Being prepared with a response plan will only help you act faster to keep your data secured.
Top data protection solutions
Alright, now that you’ve got a basic understanding of data protection, how do you start implementing those in real life?
Well, there is more than your fair share of data protection software available. I’ll break them down by category for you and help point you in the right direction for each. These are meant to serve as more of a guide as you look at software solutions and decide which one would be best for your company.
Encryption
All data and information has to be stored somewhere. Typically, on computers, it’s stored on a hard drive. That means, in theory, anyone can compromise that data if they have access to that hard drive.
What encryption does is it converts that data into a code. So, if someone were to plug a hard drive with sensitive data into their machine, they wouldn’t be able to see the data without the encryption keys.
That, of course, is an overly simplified explanation for how encryption works. It’s not just about storing your files but sending them, too. If you’re sharing files across workstations or even various office locations, then you’ll likely want to consider a transfer tool that encrypts data in transit, as well.
Encrypting hard drives and file transfers can help protect your company’s information if a computer is ever lost or stolen. It can also come in handy if a hacker gains access to one of your computers.
Data Erasure
If you’ve ever accidentally deleted an important file, then you probably know that files are rarely gone forever. Even when you empty the trash, the files are still in a temporary space on your hard drive. Meaning they can still be recovered with special tools.
This is why even when you delete sensitive data, you have to take extra precautions to make sure it’s really removed. Simply dragging a file to your Trash doesn't ensure that it’s safely being removed.
Look into specialized software and methods to reformat drives, so none of your information can be recovered. You might even want to go as far as destroying old hard drives when you’re finished using them or the computer they lived in.
Access Management
This could be an entire article in itself. Access management is such a wide-spreading topic to go over and consider. Obviously, it is about access to different types of information your organization collects and stores. I would definitely recommend taking some time to search out this topic in greater detail. But, for the sake of this article, I’ll keep it to just two facets for you to consider.
As you’re observing workflows and processes, also keep in mind who really needs access to each of them. It’s a smart idea to limit each system or workstation to just the people that need to use them. This cuts down on how many vulnerabilities you’ll have within your network. Especially, for higher ranking employees who might have more administrator-level access to things.
Another aspect of access management you’ll want to think about is made up of your password policies and multi-factor authentication. Enforcing each of these in various ways can help tighten your security and prevent a phishing attack in the future.
Endpoint Security
This sounds a bit more complex than it actually is, but in reality, this is the one you’ve most likely heard about. Endpoint security is simply about the security policies and software you have on your individual devices. However, it is important to note that it should cover all devices your employees use that can potentially collect and store sensitive information. These may include computers, laptops, smartphones, and tablets.
Every piece of hardware in your company should have some form of antivirus software, encryption, and password management on it. This will keep things locked down and periodically scan for new threats.
Data security is incredibly important. Whether you’re storing personal information from your employees or receiving credit card data from your customers, it’s your responsibility to keep it safe.
Data protection doesn’t have to be scary though. I hope after reading this article you feel like you have a better understanding of where to start with it all. And remember to check with any local laws to see what your responsibilities may include when it comes to keeping sensitive data private.