The use of macOS devices in enterprise environments has grown significantly in recent years. As more businesses rely on Macs, they become an attractive target for cybercriminals. Recent cybersecurity reports from 2023 and 2024 highlight that macOS is not immune to cyber threats and it’s no longer enough to rely on Apple’s built-in security features alone.
A stark example is the discovery of Atomic Stealer (AMOS) malware in 2024, designed to extract sensitive data such as keychain passwords, browser credentials, and cryptocurrency wallets. This highlights the increasing risks for macOS users, as hackers create malware and exploits specifically designed to target them.
The stakes are high — IBM’s Cost of a Data Breach Report 2024 reveals that the global average cost of a data breach reached $4.88 million, a 10% increase from last year. To resist evolving threats, organizations must adopt a multi-layered security strategy.
In this article, we’ll explore the best practices and essential tools for securing macOS endpoints, helping you take a proactive step toward comprehensive protection.
Why macOS endpoints are under increasing threat
Traditionally seen as more secure than other operating systems, macOS is now facing a growing wave of sophisticated threats. Below are key factors contributing to the increasing risks for macOS endpoints.
1. Increased adoption — A bigger target for cybercriminals
With more companies embracing a CYOD (choose your own device) or BYOD (bring your own device) policy, Macs are becoming an essential part of the modern workplace. More employees prefer using a Mac for work for its performance, security, and smooth user experience.
As Macs become more popular in business environments, they are also becoming a bigger target for malware developers. A larger user base means greater potential rewards for attackers who successfully compromise macOS systems.
2. Malware-as-a-Service (MaaS): Lowering the barrier for attackers
The rise of Malware-as-a-Service (MaaS) has made it easier than ever for cybercriminals to create and distribute macOS-specific malware. Attackers don’t need advanced technical expertise as they can now purchase malicious tools on dark web marketplaces. These platforms offer customizable malware, phishing kits, and exploit frameworks designed specifically to target macOS, making attacks more accessible to a wider range of bad actors.
3. Diverse malware threats
Many cyber threats have evolved to bypass traditional security measures, making macOS endpoints increasingly vulnerable:
- Ransomware: Once considered rare on macOS, ransomware attacks are becoming increasingly sophisticated and targeted. Attackers deploy malware that encrypts user data, making files inaccessible until a ransom is paid — often in cryptocurrency.
- Phishing attacks: Cybercriminals use deceptive emails, fake login pages, and social engineering tactics to steal credentials and compromise systems.
- Data-stealing malware: Advanced malware, such as Atomic Stealer (AMOS) we mentioned above, is specifically designed to extract sensitive information, including keychain passwords, browser credentials, and cryptocurrency wallets.
- Zero-day exploits: Previously unknown vulnerabilities in macOS are highly valuable to hackers, allowing them to bypass security measures before fixes are released.
Best practices for securing macOS endpoints
Securing macOS endpoints is critical to protect sensitive data, ensure compliance, and mitigate cyber threats. Follow these best practices to establish a robust security framework for your organization.

1. Automate system and software updates
Keeping macOS and installed applications updated is fundamental in preventing security breaches. Enable automatic updates to make sure that all security patches are applied as soon as they are released. Through Apple’s Mobile Device Management (MDM) solutions, you can configure update policies to enforce compliance across all endpoints, preventing users from delaying critical updates. Also, regularly audit devices to confirm they are running the latest versions.
2. Implement strong authentication mechanisms
- Require complex passwords with defined expiration policies.
- Implement two-factor authentication (2FA) for all critical accounts.
- Configure biometric authentication (Touch ID, Face ID) where applicable for an additional security layer.
3. Utilize Mobile Device Management (MDM) for configuration enforcement
Make use of Apple’s Mobile Device Management (MDM) tools that allow it to enforce security policies and configure devices remotely:
- Restrict unauthorized applications.
- Enforce encryption and password policies.
- Manage system settings to align with security best practices.
4. Strengthen network security
Securing network connections prevents cyber threats from exploiting vulnerabilities. Key recommendations include:
- Use DNS protection services to block malicious sites and phishing attempts.
- Deploy VPN solutions for secure remote access to corporate resources.
- Enforce firewall rules to filter unauthorized traffic.
5. Deploy Endpoint Detection and Response (EDR) solutions
EDR solutions analyze unusual behavior, identify potential security breaches, and generate alerts to help IT teams respond quickly. Therefore, by implementing EDR, you can detect and mitigate security incidents before they escalate.
6. Enforce disk encryption and data protection
To safeguard sensitive data, follow these steps:
- Enable FileVault to encrypt macOS storage drives.
- Use secure cloud backups with end-to-end encryption.
- Implement data loss prevention (DLP) strategies to prevent unauthorized data transfers.
7. Limit administrative privileges
Restrict administrative privileges to reduce the risk of accidental system modifications. Best practices include:
- Assigning standard user accounts for daily operations.
- Using privileged access management (PAM) solutions for elevated access when necessary.
- Monitoring administrative activities for potential security risks.
8. Conduct regular security audits and user training
Well-informed users are one of the strongest defenses against cyber threats.
- Perform periodic security assessments to identify vulnerabilities.
- Provide cybersecurity awareness training to educate users about phishing and malware.
- Encourage employees to report suspicious activities promptly.
By implementing these best practices, you can keep your macOS endpoints secure, minimize cyber threats, and create a reliable IT environment that supports your organization's operations.
Top tools for macOS endpoint security
There are dozens of tools available to help with endpoint security. They range from comprehensive solutions designed to take care of the bulk, if not all, of an organization’s security needs to specialist apps that focus on one aspect, such as passwords. The best solution for you will depend on the size of your organization, the number of endpoints that need to be managed, and the budget. We’ve listed tools below that cover different aspects.
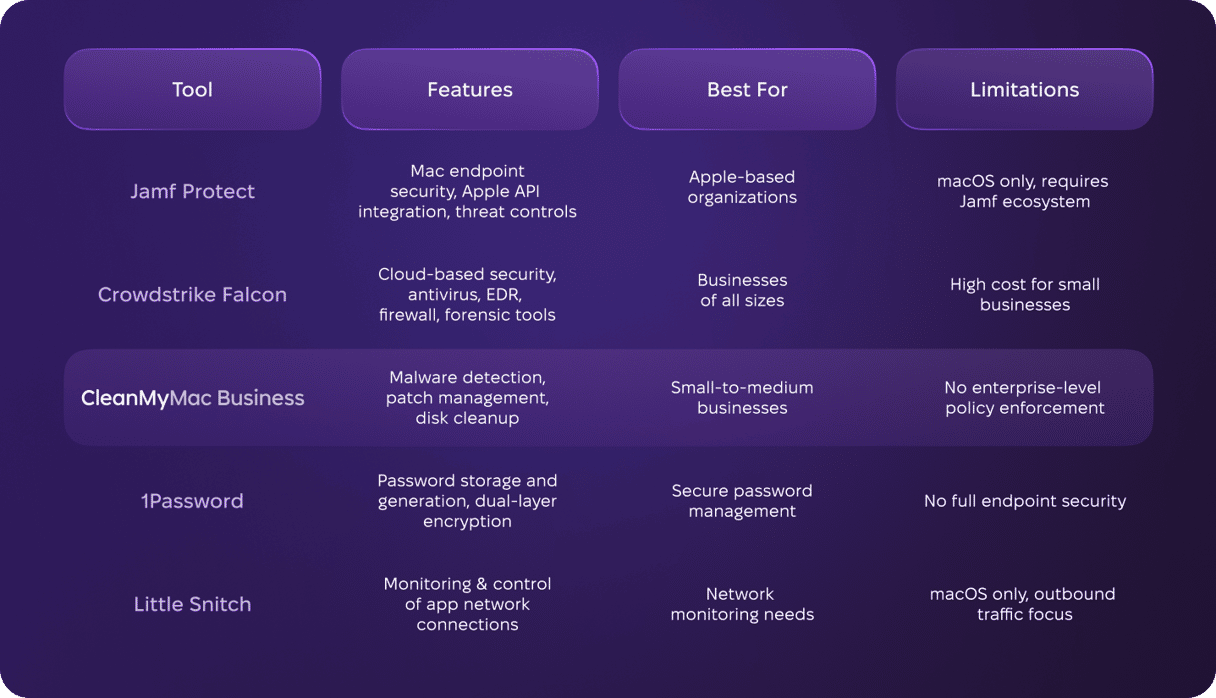
1. Jamf Protect
Protect is the endpoint security tool from Jamf, one of the most well-known names in mobile device management. It’s designed specifically for Mac and integrates with Apple’s endpoint security API. That means that OS updates are available on day one and can be rolled out immediately. It has advanced threat controls that block unsafe activity, such as plugging in external storage, and it notifies administrators when a device is no longer compliant.
- Pricing: Custom pricing based on organization size and needs.
- Ease of use: Requires some IT expertise but integrates well with Apple systems.
2. Crowdstrike Falcon
Falcon is Crowdstrike’s cloud-based cyber security platform and it incorporates several different products aimed at different sizes of organizations. Among those are Falcon Prevent, its antivirus tool; Falcon Insight, an EDR tool; and tools for USB device control, firewall management, and forensic data analysis.
- Pricing: Depends on the bundle and your needs.
- Ease of use: User-friendly interface but requires security expertise for advanced features.
3. CleanMyMac Business
CleanMyMac Business is a comprehensive Mac monitoring and maintenance tool that provides effective malware detection and removal, patch management, and disk cleaning tools that can be used to maintain multiple Macs in an organization. It’s aimed at small-to-medium-sized businesses. Larger businesses can use it alongside an existing MDM.
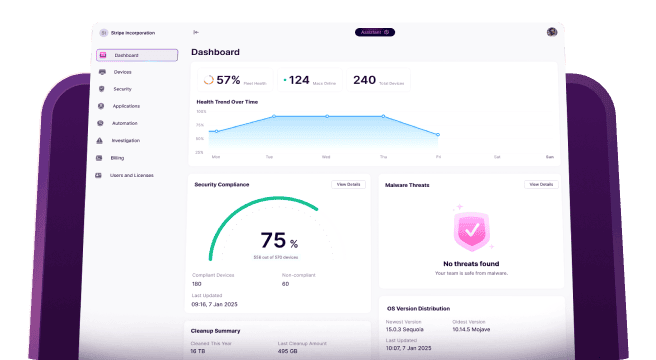
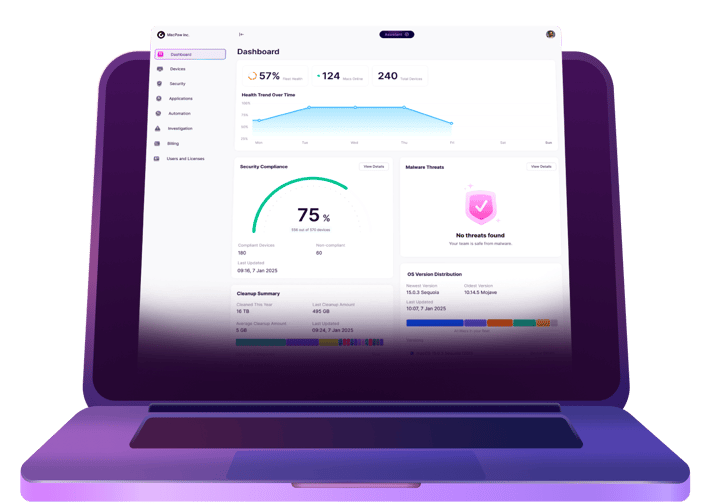
It can be set up in a few minutes and its dashboard interface makes it very easy to monitor data points like malware threats and compliance. In addition to malware detection and disk cleaning, CleanMyMac Business can be used to update all your organization’s Macs quickly and easily. It can be installed manually or via an MDM like Jamf.
- Pricing: Depends on the organization size, starting at $2 per month for one device.
- Ease of use: Very easy to set up and use, no advanced IT knowledge required.
4. 1Password
Using secure passwords and managing them securely is a critical part of endpoint security. And while Apple’s Passwords tool is useful in that respect, it doesn’t contain many of the tools seen in commercial password managers like 1Password. In addition to generating, storing and auto-filling robust passwords, 1Password can be used to save financial data like credit card numbers, secure notes, and software license keys. Everything is encrypted using a dual-layer encryption system.
- Pricing: Starts at $2.99 per user per month for individuals; business plans available.
- Ease of use: Extremely user-friendly with cross-platform compatibility.
5. Little Snitch
Applications that contact remote servers, or ‘phone home’ can be a security threat because they may be sending private data. Little Snitch’s role is to tell you when an application phone is home. In fact, it will tell you whenever any application on a Mac connects to the internet. You can choose how you are notified and whether specific applications can connect to the internet at all. And you can view reports of the details of servers to which applications are connecting, including their address and geographical location.
- Pricing: One-time purchase of $59 per license.
- Ease of use: Requires initial setup but is intuitive once configured.
Robust endpoint security is a must-have for any business that doesn’t want to leave itself open to malware threats, data theft, or significant loss of money and reputation. Apply the best practices and tools described in the article to enhance your organization’s security and protect your Mac fleet.