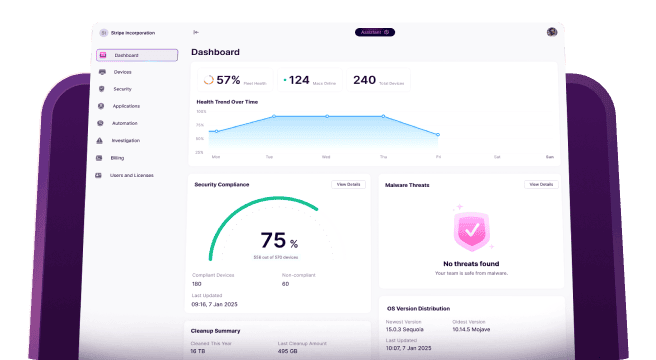
More and more organizations and companies are incorporating Macs and mobile devices into their operations, usually by distributing MacBooks, iPhones, and iPads to employees to allow them to work both in the office and remotely. As such, ensuring that Macs and mobile devices are secure, adhere to the organization’s security policies, and are compliant is essential for a number of reasons. In this article, we’ll explain what security compliance for Macs and mobile devices is and explain why it is so important.

What is security compliance?
Security, as it relates to Macs and mobile devices, encompasses both digital security that is the safety and integrity of the data on the devices and the networks to which it connects and physical security. It helps in making sure the device itself is protected from theft, damage, or anything else that could cause the organization, its clients, or partners loss or damage.
Compliance means adhering to local and national laws, industry standards, the organization’s own policies, the policies laid out in any codes of practice, or principles to which it has signed up. Compliance is usually managed by auditing both policies and practices, a process that can be carried out internally or by a third party. Security compliance incorporates data security compliance and cyber security compliance.
Benefits of security compliance
There are a number of benefits of security compliance, many of which are not obvious. Here are just a few:
- Avoiding sanctions. At the most fundamental level, complying with laws is essential to avoid penalties that could include fines and other financial penalties or even criminal action taken against officers of the organization. If an organization has signed up to a code of practice or industry body, those may also have sanctions for failure to comply, such as a loss of membership.
- Protection of reputation. For most companies, reputation is hugely important. This is even more important if the business of the company involves handling data or financial information. By adhering to strict security compliance principles, companies can demonstrate that they are serious about protecting client and partner data and can be trusted with sensitive information.
- Mitigation of security risks. Security compliance isn’t just about optics. By implementing the policies required to be compliant, organizations enhance and improve their own security. This leaves them less vulnerable to security breaches, which could have a significant effect on their ability to operate, as well as result in data loss or damage to network infrastructure.
- Improved customer confidence. One reason many organizations sign up to codes of practice or principles of third-party industry groups is to inspire confidence in customers that they can be trusted. Adhering to security compliance and being able to demonstrate that will further enhance that confidence.
- Best practice data management. Prior to the implementation of General Data Protection Regulation (GDPR) in the EU, many organizations had a somewhat scattergun approach to collecting and managing personal data. Since its implementation and the introduction of similar laws in other parts of the world, companies now have much better policies with regard to the data they collect, how they use it, and how and when it is disposed of. That benefits the organizations as it leaves them less vulnerable to accusations of data misuse and means their customers’ data is at less risk of being stolen or otherwise compromised.
- Better relationships with customers, partners, and staff. It’s pretty clear that if business partners and customers know that an organization has effective security compliance, they are more likely to trust it. For one thing, if an organization takes security seriously, it’s more likely to take other aspects of business seriously, too. And while employees may not be best pleased with the additional burden placed on them, such as attending training, because of security compliance, they will also understand that their own data is more secure and the customers are happier.
Risks of lacking security compliance
- Financial and other penalties. Failing to comply with laws or the policies of professional associations of which an organization is a member is likely to result in sanctions, which could include financial penalties or membership suspension.
- Damage to reputation. If an organization’s failure to adhere to security compliance becomes known, it is likely to damage its reputation. This damage will be particularly severe if the organization operates in an area such as financial services, where data security is paramount. That reputational damage is likely to result in a loss of revenue and customers turning to competitors.
- Falling behind competitors. The result of reputational damage is usually that organizations fall behind competitors. Time and resources must be spent restoring that reputation and ensuring that security compliance is adhered to in the future. This can have significant impacts on the organization, including loss of revenue, a fall in value, and the need to cut spending in other areas.
How to implement security compliance
There are several steps to implementing security compliance.
- Conduct a security audit. Conducting an internal audit will tell you what you are currently doing well as an organization and where you need to improve in terms of security compliance. As part of the audit, organizations should look at the software and systems they are currently using and whether they are up to date.
- Create a cross-department compliance plan. The result of the internal audit should form the basis of the plan to improve security compliance. The plan needs to span the entire organization and communicate that compliance is everyone’s responsibility. As part of the plan, it’s a good idea to consider whether current software and systems used to manage networks and assets are fit for purpose or whether there are better options available.
- Identify and mitigate risks. The audit should have highlighted where the organization is most at risk in terms of security of systems and data. More work should be done to detail the risks and then mitigate them.
- Document everything. The result of the internal audit, actions taken and still to be taken, new policies, and evidence of communication with staff should be documented. This will make it easier to gather evidence for external audits and will also provide a record of what has been done and what still needs to be actioned.
- Monitor everything. Keeping up to date with the latest security threats, as well as developments in cybercrime and industry best practices for mitigating risk, is an essential part of a security compliance plan.
Security compliance best practices
As part of the creation of a plan for security compliance, there are several elements that can be thought of as best practices:
- Configure systems using the principle of least privilege and functionality. Allowing staff to only access the systems, applications and parts of the networks is key to best-practice security compliance. It requires striking a balance between allowing staff access to the tools they need to carry out their responsibilities while minimizing what they have access to. This will allow them to do their job while minimizing the risk that widespread access to secure areas brings.
- Enforce regular software updates. Keeping software up to date is an essential component of security in any organization because updates often include patches to fix security vulnerabilities or deal with new threats. And the best way to ensure that software on users’ machines and devices is kept up to date is to enforce updates. This could be immediate or by allowing a fixed number of deferrals before an update is imposed. Most endpoint management tools allow for operating system and application updates to be distributed in this way.
- Create and implement a risk management plan. If the worst were to happen and your organization succumbed to a cyberattack or data breach, what would the response be? That’s a question you shouldn’t have to think about. It should be laid out clearly in a risk management plan. That plan should assess and describe the risks to the organization, responsibilities for mitigating that risk, and actions to be taken in the event of a breach. Once the plan has been finalized and communicated, it should be tested to determine its resilience.
- Use automated tools. Planning for and implementing security compliance manually is a time-consuming job, and there’s always a chance that something will be missed, no matter how many people are involved. Using automation tools designed for the job will reduce the amount of manual labor involved and minimize the risk of missing something. There are several available. Research and choose the best one for you.
As you can see, security compliance is essential for any organization that wants to keep customers happy and keep up with competitors. Fundamental to security compliance is the creation of a plan, implementation of best practices, and regular monitoring, testing, and auditing to ensure compliance is maintained.