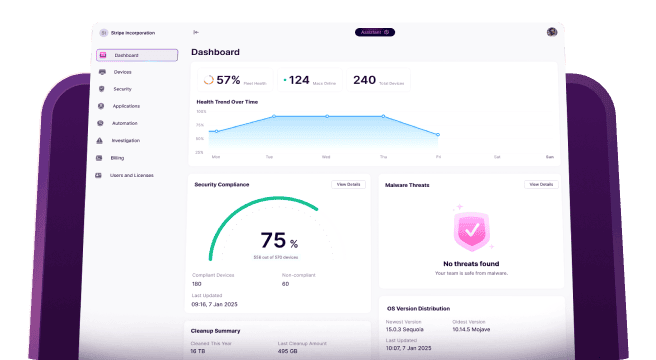
The sheer number of mobile devices that can be connected to networks means that the potential for compromising the security of a network using an endpoint is much greater than it’s ever been. IT managers responsible for security need to be aware of all the possible mobile security threats and how to deal with them. In this article, we’ll explain how to do that.
What are mobile security threats?
A mobile security threat is anything that might compromise the security of a mobile device and the data on it and, therefore, the security of any network it connects to. It could be malware on the device, an unsecured Wi-Fi network it’s connected to, or even a phishing email sent to the device.
Some of the most common mobile security threats are:
- Data leaks
- Malicious apps
- Phishing
- Out-of-date software
- Poor authentication
- Unsecured Wi-Fi
- Poor physical security
Let’s discuss them in more detail.

Data leaks
Data leaks can occur in lots of different ways. Those that get the most publicity typically involve servers owned by large organizations or cloud storage services. However, individual mobile devices can also be a source of data leakage, thanks to the permissions many apps seek when you install them. Apps often request access to the device’s microphone and camera as well as folders like Desktop and Documents on a MacBook. In addition, many apps will, by default, attempt to track you across apps and as you move from one website to another in a web browser. To mitigate the chance of a data leak, devices should be configured so that only permissions that are absolutely necessary to carry out the tasks required are granted.
Malicious apps
This should be less of a problem on Apple devices, thanks to careful regulation of apps on the App Store. But other mobile platforms may be vulnerable to malicious apps that set out to spy on users and steal data. An organization can mitigate this threat by using a mobile device management solution (MDM) that sandboxes apps and data used for work and restricts the apps that can be installed on company-owned devices.
Phishing
Phishing is a mobile security threat as well as a wider threat to the security of an organization’s network. Phishing emails or messages sent to an app on a device can present a significant threat to the device and any network it is connected to if the link within them is clicked. The solution is to train and educate users on how to spot a phishing email or message and how to report it if they find one. This should be supported by regular drills, where fake phishing emails are sent by IT administrators to test the effectiveness of training and identify where more training is required.
Out-of-date software
Old apps that are no longer updated but remain installed on a device can be a vector for malware if they are hijacked and used by hackers to distribute malicious code. And an operating system that is out of date can be a security threat because it won’t have the latest security patches installed, so it won’t have protection against the latest mobile security threats. This risk can be minimized if an organization’s policies require devices and apps to be updated as soon as an update becomes available. Updates can be pushed to devices by an MDM solution.
Poor authentication
The days of a username and password being enough to log onto a secure network are long gone. Multifactor authentication should be a minimum to protect networks and data. Using a single-sign-on system for company networks, apps, and other services is convenient, but it also needs to be secure. Policies should enforce strong passwords and authentication using a mobile app on a different device.
Unsecured Wi-Fi
Any network is only as secure as its weakest point, and a mobile device connected to an unsecured Wi-Fi network is that point. Unsecured Wi-Fi networks can be used by hackers to intercept traffic and steal data. So-called man-in-the-middle attacks, where the attacker positions themself between the device and the server it’s connected to, use exactly this method. Using an MDM to sandbox apps and data used for work offers some protection against this type of attack. And so does using a VPN or ZTNA (zero-trust network access) to encrypt traffic.
Poor physical security
Mobile devices these days are usually locked with a passcode and can be wiped if they are lost or stolen. However, a device that is not sufficiently protected and whose owner doesn’t take steps to keep safe is vulnerable. And if a device that is not properly secured is stolen, the data on it is vulnerable.
Why is mobile security important?
Many — in some cases, most — of the computers that access an organization’s network are mobile devices, such as laptops, tablets, and smartphones. Mobile security is essential to prevent unauthorized access to an organization’s network and the data loss that may result. In addition to data loss, malicious actors accessing a network can cause damage to servers, systems, and applications. And that will result in financial loss as well as the loss of reputation and potential penalties from regulatory authorities. Recovering from the kind of losses that could result from a major security breach could take years.
How to prevent mobile security threats
There are several things that can be done to combat mobile security threats:
- Keep apps and operating systems on devices up to date
- Use a VPN or ZTNA
- Use multifactor authentication
- Provide permissions to apps only where they are needed
- Carry out training on how to spot phishing emails
- Manage devices using a good mobile device management tool
Mobile security threats are many and varied. It’s essential for device users and network managers to be aware of them and how to deal with them. By reading the advice above, you’ll be better equipped to do that.