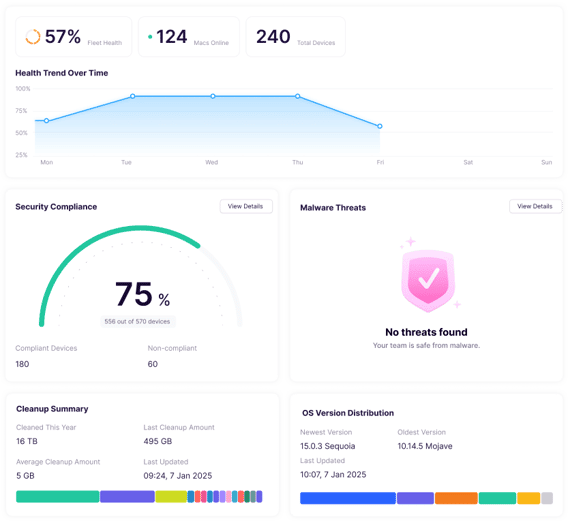
Struggling to keep track of your Apple devices in a growing organization? You’re not alone. The rise of Macs in businesses and remote work has created new security challenges for organizations. How do you distribute MacBooks to staff while ensuring network security and compliance with company policies? Mobile device management (MDM) is the solution for many.
To make using MDM tools as straightforward as possible, Apple developed MDM Server, a platform designed to be used with third-party MDM solutions. It allows users to install OS updates, change device settings, monitor compliance, and remotely wipe machines. In this article, we take a closer look at Apple MDM Server.
Understanding Apple MDM Server
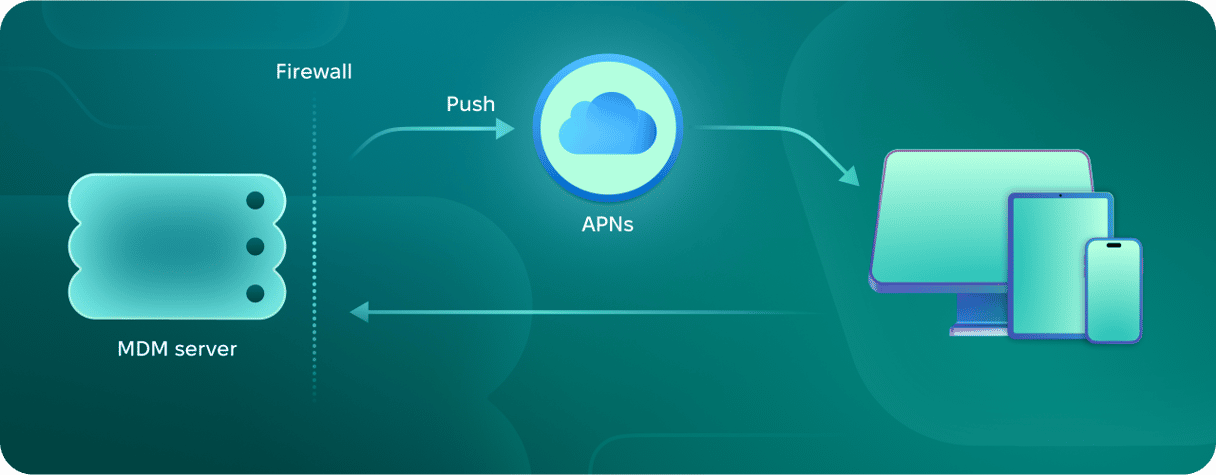
How it works
Apple MDM Server must be used in conjunction with a third-party MDM tool. That tool installs a profile on the Mac that allows it to enroll with the Apple MDM Server. It can also be used in conjunction with Apple Business Manager or Apple School Manager to enable automatic enrollment.
Apple MDM features
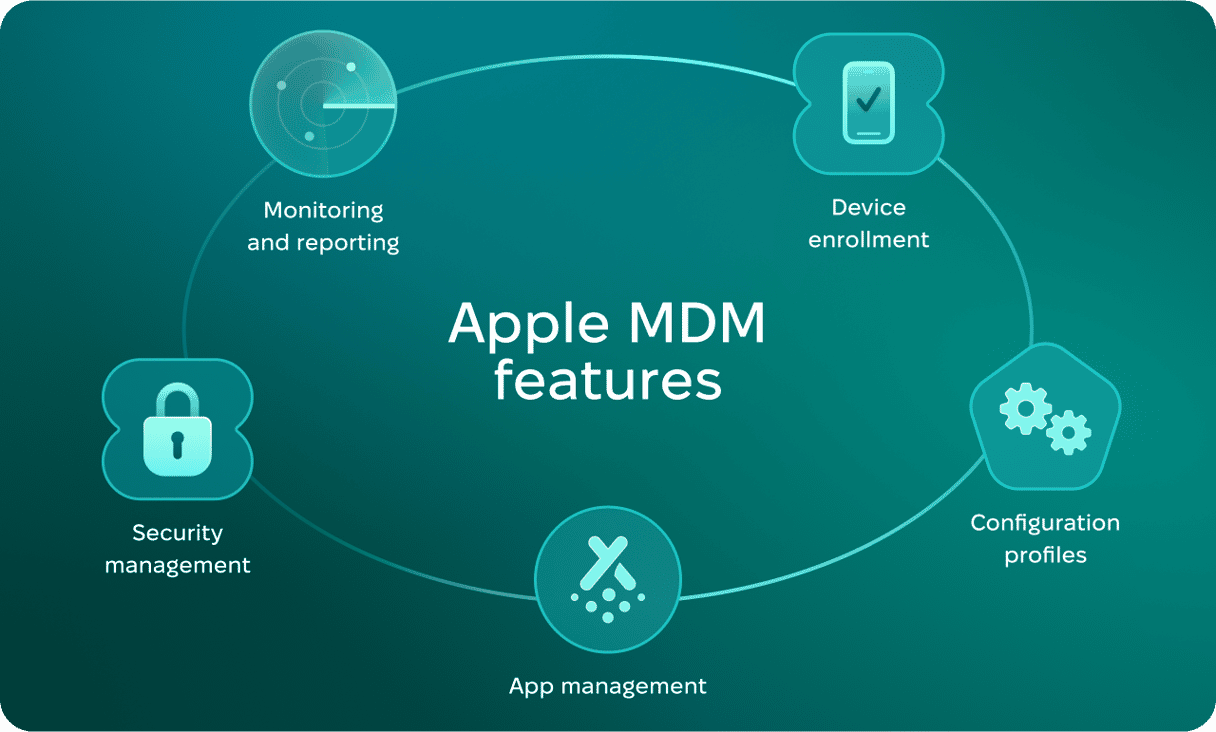
Device enrollment
If the third-party MDM is used in conjunction with Apple Business Manager or Apple School Manager, the device’s serial number can be added to those tools, allowing the device to be sent directly to the user where enrollment in Apple MDM Server can take place automatically. This process, known as zero-touch, makes it much easier to order new or replacement devices for remote workers.
Configuration profiles
Once a device has been enrolled with an MDM, either using an enrollment profile or user enrollment, the MDM can send it a configuration profile. Configuration profiles contain payloads that allow the organization to distribute, update, and configure apps remotely.
App management
Devices enrolled with Apple MDM receive notifications from the MDM server for commands like OS updates. The device then contacts the server, downloads a command, and acts on it. If the server sends an InstallApplication command, the Mac will connect to the server and download the app from the App Store or a local caching server.
Security management
Macs that are enrolled with Apple MDM server can be wiped if they are lost or stolen. They can also be locked. Organizations can also use Apple to enforce compliance with their own security policies.
Monitoring and reporting
A status channel carries communication from the device, which reports pro-actively to the server, about its current status for a number of items including battery health, OS version and background tasks.
Benefits of using Apple MDM server
Using Apple MDM server in conjunction with a third-party MDM, Apple Business Manager, and Apple School Manager has a number of benefits.
📌It’s highly scalable and suitable for organizations that are relatively small as well as large multinational corporations.
📌Security is improved because the Apple MDM server can ensure that organizational policies are followed and sensitive data is protected.
📌It improves efficiency because it can form part of a zero-touch rollout scheme, reducing the need for IT admin staff to be involved in setting up new devices.
📌User experience is better because settings and apps are pre-configured using the profile installed before they get the device.
Recent updates and advances
- Declarative Device Management (DDM). Apple describes the introduction of declarative device management as ‘transformative’. Using it, a MacBook or other device can apply management logic to itself without help from the server. And it can report state changes to the server in real time, without the server first requesting the information. IT admins can specify a desired state for devices and if, say, a Mac reports a state that is not compliant, it can be prevented from accessing the network.
- Apple Intelligence is a new set of features in macOS, iPhone, and iPad. However, not all IT admins will want devices on their networks to use all its features. So, Apple has given admins the power to control or even block these features. Using an MDM, admins can restrict features such as Siri, personal suggestions, and Apple Intelligence in Photos or prevent them from being used altogether.
Choosing the right MDM solution
There are a number of third-party MDM solutions available for macOS:
- Jamf
- JumpCloud
- Kandji
- Hexnode
MDM solution checklist: Key factors to consider
✔️What kind of support and training does the vendor provide?
✔️Do you plan to host the MDM server locally or in the cloud? Does the vendor’s solution accommodate both options?
✔️Does it support Apple-based portals like Apple Business Manager and Apple School Manager?
✔️Is the solution tailored for managing Apple devices?
✔️What commands and features does the MDM server support to manage your devices efficiently?
Summary
Apple MDM server is a protocol for Apple devices that, when used in conjunction with a third-party MDM server, allows devices to be enrolled, create configuration profiles, and manage app installation and updates. It also allows IT admins to enforce security policies.
If your organization deploys Macs and other Apple devices to staff, it’s essential to use an Apple MDM server along with a third-party MDM. This helps streamline onboarding new users and ensures existing devices comply with organization policies.