The role of security management should be the number one priority for all organizations. Although, sadly, that’s not always the case. Cybersecurity management is, more often than not, an afterthought. And well, if you want to protect your company’s assets, then that is going to need to change fast.
But don’t worry, I’ve got you covered. Even if you’ve never heard of enterprise security management, this article will explain what that is, why you need it, and what you can start doing to improve it within your organization.
What is security management?
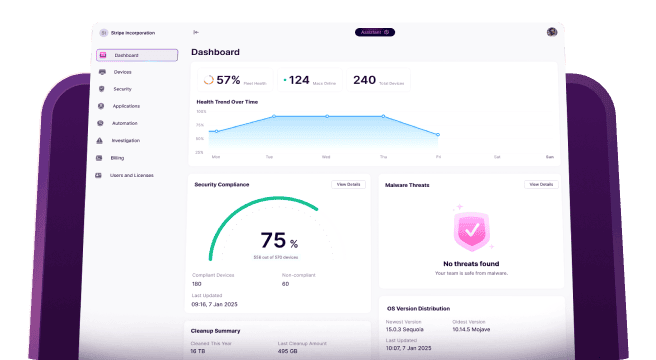
Security management is the team and policies an enterprise puts into place to identify and minimize the risk of any potential threats.
An information security management team is there to stay up to date with current or possible hacking attempts or ransomware floating around the internet. They also create and enforce security policies that will keep the enterprise safer. These policies help manage how often passwords must be set, handle end-user device lockdowns, and control which applications are permitted for use.
Purpose of security management
A common misconception is that this team or person just says “No” to everything. But in reality, a good security management department is collaborating with end users to find solutions that make their workflows more efficient and even safer at the same time.
The main goal of a security management team is to keep the company safe. But, if the security policies are causing more work, they could be costing the enterprise money now. That’s where data classification, risk management, and threat protection come in.
Data classification
Not all information is created equal. At least some data is not as valuable as other data might be. That’s why it’s critical to do an analysis of what files or information are being saved or used in specific apps.
Using a doctor’s office as an example, a patient’s medical history would be classified with the highest level of security. While the office staff’s lunch order from last Tuesday is probably not important at all. So, when it comes to allowing an app or website to be used in your enterprise, it might depend on the data classification you assign to it.
Risk management
At a certain point, having no security risks is impossible, especially as different departments start working with different vendors or partners. Exchanging information and files always comes at a risk.
For instance, if another team at your enterprise needs to use an app that is not up to your security standards but it’s mission-critical to their work, that’s when you’ll need to do a risk assessment. You’ll audit their workflow and see what policies can be put in place to mitigate any potential leaks or hacks.
Threat protection
These are the steps your team is taking to get ahead of any threats or attacks that could be lobbed at your company — protecting your users with a firm password policy, encrypting devices so information can’t leak, or even configuring firewalls so that your users can safely and securely browse while on your network.
Types of security management
Security management can sound like a big and arduous undertaking, especially if it’s not something you’ve ever had to do before. But I’m sure if you broke it into three bigger categories — information, network, and cyber security — you’d realize you know a lot more than you think.
1. Information security management
These are the best practices and policies you have in place to manage access to data in your environment. The ISO/IEC 27000 family is a series of standards designed to help companies mitigate the threat of data leaks and help ensure confidentiality. So, becoming ISO/IEC 27000 certified is a great place to start formalizing information security management in your enterprise.
2. Network security management
Network security management is arguably one of the most important components of enterprise security. Your network is where all external attacks and internal leaks will occur. Safeguarding it with firewalls, segmentation, and network monitoring are all incredibly useful steps you can take.
3. Cybersecurity management
Cybersecurity management is more of a general catch-all when it comes to it. These are the policies you implement to help manage the oddball, one-off devices that might need to connect to your network. Policies of using cloud solutions both internally and from partner companies. And, of course, this is the category that poses the question, “How do you handle BYOB devices brought into the environment?”
Security management architecture
Having a security management architecture is incredibly important for your company’s future. Creating standards and policies that can grow and scale with your company will help your team enforce those and develop guiding principles for everyone in the organization to follow. Rather than just having standalone policies, architecture creates a roadmap of sorts to help create consistency across the company.

Tests for better information security management
If you’re just starting to wrap your head around security management but want to know what you can do today to improve your security, I’ve got some ideas.
Penetration tests
Penetration tests — or pen tests — help you identify problem spots by exploiting any and all vulnerabilities. By figuring out where the gaps are in your security, you can fill them up and stay more secure.
Network vulnerability management
Similar to pen tests, network vulnerability management is the process of being a little more proactive about it. Instead of pushing your equipment to see where the faults are, this is when you do that homework upfront on various apps or devices you have deployed in your enterprise.
Endpoint security
Ensure you have endpoint protection installed and running on every computer in your environment. This includes everything from antiviruses to hard drive encryption or disabling USBs.
Phishing tests
Phishing is a common scam today. Doing regular phishing tests is a great way to make sure your enterprise is staying alert to these kinds of attacks.
If you’ve never heard of phishing before, it’s when a hacker pretends they’re a legitimate person or source to trick you into giving them private information.
Information security management is something we should all be thinking about every time we use our computers. Hopefully, these simple steps will help make it all seem more digestible. And then, you can be on your way to becoming a master in security management.