What is XcodeGhost?
In September 2015, Chinese developers and the U.S. cybersecurity firm Palo Alto Networks discovered an iOS malware known as XcodeGhost. For developers creating iOS and macOS (previously OS X), tvOS, and watchOS apps, Xcode is an integrated development environment (IDE) containing a development tool suite.
In 2015, a maliciously modified version of Xcode was released through the popular Chinese file-sharing service, Baidu. Chinese developers who downloaded this version were unaware that it contained malware, and so many used it to create and compile or update apps. Once these apps were ready, the XcodeGhost was similar enough to Xcode that Apple could not spot the difference in the compiled apps. This infection impacted everything between and including Xcode 6.1 and Xcode 6.4.
As a result, over 50 malware viruses infected iOS and macOS apps were published through the iOS App Store and Mac App Store. This malware infects locked and jailbroken devices. When this was discovered, security experts estimated that this could have impacted 500 million people, partly thanks to the inclusion of WeChat in this list. Many in China, although millions more around the world, could have downloaded some of the apps. Even if you didn’t download any on your Mac, any backups you did around that time (2015 and into 2016) could include an infected app.
If you did download any of the infected apps — listed below — during that time, there is a risk that one or more of them is still active on your iPhone or Mac today. Checking this list and taking action is worth it to ensure your devices aren’t infected.
_1560159995.png)
Which apps were infected?
It took some time for Palo Alto Networks to check which apps were infected. Thankfully, the malware source was discovered, and the developers who downloaded the malicious Xcode were traced and contacted. Here are the apps that were infected with the malware:
- Didi Chuxing
- Angry Birds 2
- NetEase
- Micro Channel
- IFlyTek input
- Railway 12306
- The Kitchen
- Card Safe
- CITIC Bank move card space
- China Unicom Mobile Office
- High German map
- Jane book
- Eyes Wide
- Lifesmart
- Mara Mara
- Medicine to force
- Himalayan
- Pocket billing
- Flush
- Quick asked the doctor
- Lazy weekend
- Microblogging camera
- Watercress reading
- CamScanner
- CamCard
- SegmentFault
- Stocks open class
- Hot stock market
- Three new board
- The driver drops
- OPlayer
- Mercury
- WinZip
- Musical.ly
- PDFReader
- Perfect365
- PDFReader Free
- WhiteTile
- IHexin
- WinZip Standard
- MoreLikers2
- CamScanner Lite
- MobileTicket
- iVMS-4500
- OPlayer Lite
- QYER
- golfsense
- Ting
- Golfsensehd
- Wallpapers10000
- CSMBP-AppStore
- MSL108
- TinyDeal.com
- snapgrab copy
- iOBD2
- PocketScanner
- CuteCUT
- AmHexinForPad
- SuperJewelsQuest2
- air2
- InstaFollower
- CamScanner Pro
- baba
- WeLoop
- DataMonitor
- MSL070
- nice dev
- immtdchs
- OPlayer
- FlappyCircle
- BiaoQingBao
- SaveSnap
- Guitar Master
- jin
- WinZip Sector
- Quick Save
As you can see, many of those are only applicable or popular in China. However, thousands of users have downloaded some of these apps across the Asia-Pacific region.
What can XcodeGhost do?
Make no mistake, this was a pretty sophisticated cyber hack, and the malware was created to get as much information as possible from millions of devices. The information it sent back to command and control (C2) servers included the following:
- The current time on a device
- Infected app’s name
- Apple’s bundle identifier
- Device name and type
- System’s language and country
- Device UUID
- Network type and name
Beyond collecting data, the infected apps and devices could receive commands from the server and those responsible for this. XcodeGhost was designed to perform these malicious functions:
- Create a fake alert message to use phishing techniques to steal passwords.
- Hijack browser and in-app URLs to exploit iOS and macOS vulnerabilities.
- Read and write clipboard data to unlock any passwords copied and pasted or stored in password management systems.
Once this was discovered, responsible developers started to update apps they’d compiled using the XcodeGhost, and Apple moved forward with security updates to flush it out of the system. However, anyone who’s downloaded any of these infected apps or maybe downloaded them and has not updated them since this was discovered (or still has any backups on macOS devices) could still be infected.

How to protect against XcodeGhost
Here are a few basic tips to stay safe:
- Delete any of the infected apps from your iPhone or iPad.
- Update your iOS.
- Reset your iCloud and any other passwords on your iOS device.
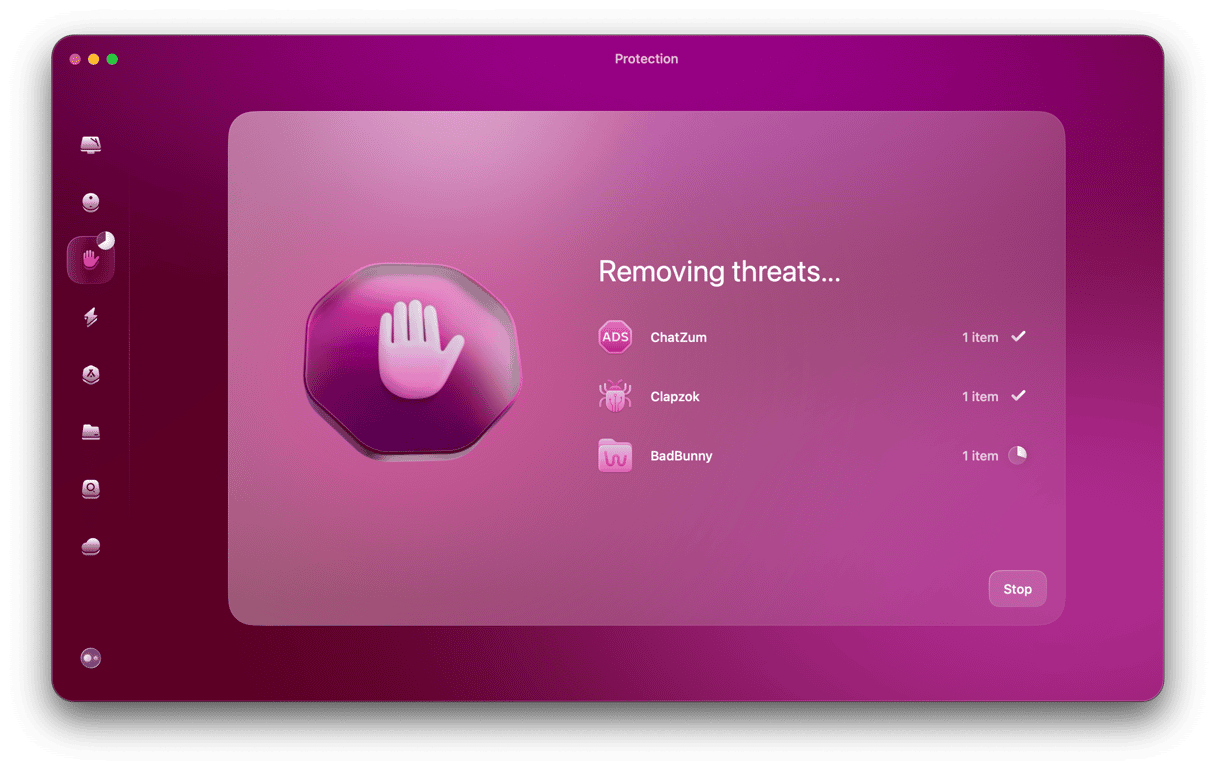
Moreover, make sure to scan your Mac for malware using special software like CleanMyMac. It has a Malware Removal tool that detects and neutralizes thousands of threats, including spyware, adware, viruses, and other threats. CleanMyMac will find and remove the XcodeGhost virus in a matter of seconds:
- Download CleanMyMaC X (free trial available).
- Choose the Malware Removal tab.
- Click Scan.
- Click Remove.
That’s it! Now your Mac’s safe and can run at full speed again!