Choosing the right operating system for your team isn’t just about productivity — it’s about security. With the growing frequency of cyberattacks, understanding the strengths and weaknesses of macOS and Windows could be the difference between a data breach and business continuity. In this article, we’ll look at each aspect of the question and explain the technologies designed to keep you safe from bad actors.
Built-in security features
Both macOS and Windows have built-in features designed to protect them and your data from hackers and malware distributors. Let’s look at those in detail, starting with macOS.

macOS
System Integrity Protection (SIP)
SIP places restrictions on the access of third-party applications to the deeper parts of the system. Before SIP existed, if a third-party application was run from an administrator account it could access the whole system.
GateKeeper
GateKeeper controls which applications can be installed on your Mac. You can choose to allow only apps downloaded from the Mac App Store to be installed on your Mac or those apps plus applications from what Apple calls ‘known developers’. Applications from known developers are scanned for malware by Apple in a process known as notarization. If no malware is found, Apple issues a notarization ticket, and if that ticket is attached to the app, GateKeeper will allow it to be launched. Notarization tickets can be revoked if an app is later found to be malicious.
XProtect
XProtect is macOS’ built-in signature-based malware detection and removal tool. XProtect checks an app when it is first launched, when it’s updated, and when the signatures used by XProtect are updated. When XProtect detects malware, it notifies the user and blocks the app from launching.
FileVault
Macs with a T2 security chip or Apple silicon encrypt files by default. If FileVault is turned on, a password is needed to open files. In earlier Macs without a T2 security chip, turning on FileVault encrypts files.
Windows
Windows Defender Antivirus
Windows Defender is Windows’ built-in anti-malware tool. It uses more sophisticated techniques than XProtect, such as behavioral heuristics. It also provides real-time scanning of files and websites, as well as cloud-based detection and sandboxing. Unlike XProtect, it’s not reliant on malware having been previously detected and a signature created.
BitLocker
BitLocker is a security tool that encrypts data volumes to prevent unauthorized access. It works alongside a hardware component, called the Trusted Platform Module (TPM), which is found in many Windows laptops. Together, BitLocker and TPM can ensure that a Windows laptop hasn’t been tampered with and require a security code to be entered to unlock the startup process.
Windows Firewall
Like other software Firewalls, Windows Firewall filters network traffic and blocks unauthorized incoming connections. It bases that filtering on properties like IP addresses, ports, or program paths. Windows Firewall allows networks to be designated as public or private and sets rules for access based on that designation.
SmartScreen
SmartScreen is designed to protect against phishing and malware by analyzing webpages, checking them against a list of known malware sites, and warning users if a site they visit is likely to be harmful. It also compares downloaded apps or installers against a list of files that are known to be unsafe as well as a list of files that are well known and downloaded often. If an app appears on the first list, the user is warned that the file might be malicious. If the app doesn’t appear on the second list, caution is advised.
Vulnerabilities and malware incidents
One of the most notable malware campaigns targeting macOS systems in business environments is the BeaverTail attack. Targeting both macOS and Windows users, the attackers impersonate recruiters on platforms like LinkedIn and Freelancer, offering job opportunities to lure victims in. The fake recruiters trick targets into downloading and running trojanized apps disguised as legitimate tools for job interviews or collaboration.
The fact that the malware's code has been continuously refined between attacks shows how active and adaptive the attackers are. These sophisticated social engineering tactics highlight the importance of solid security measures, including advanced malware detection and thorough employee training.
The number of incidents targeted at Macs pales by comparison to those targeted at Windows, however. The sheer number of people using Windows, even as the Mac has become more popular, makes it a much more attractive target, especially for those who sell malware toolkits to would-be malicious actors. As an example of the difference in the volume of threats between the two platforms, in 2022, AV-TEST Institute registered more than 62 million new Windows malware samples, compared with fewer than 100,000 macOS samples.
Historically, macOS has been targeted by malware distributors much less often than Windows. In 2024, there was a noticeable spike in malware attacks targeting macOS.
User behavior and security practices
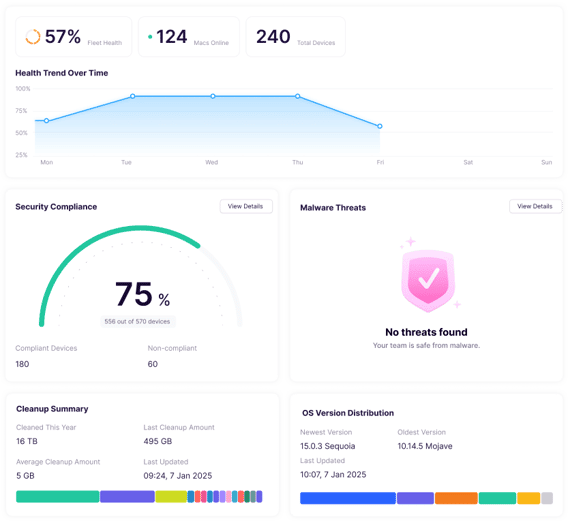
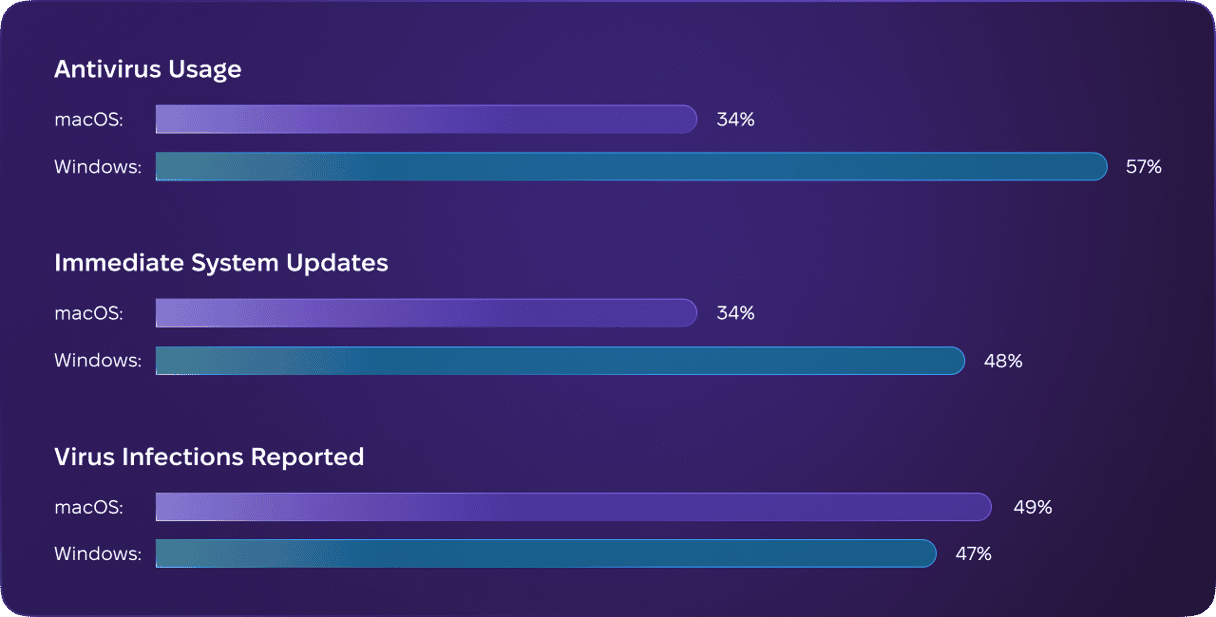
One area where the perception that MacBooks are more secure than Windows laptops has had a significant impact is user behavior and security practices. Mac users’ belief that Macs are somehow inherently secure means that they tend to use anti-virus software, for example, at a much lower rate than Windows users.
A survey carried out by security information website All About Cookies in 2023, found that only 34% of Mac users used anti-virus software, compared with 57% of Windows users. Worryingly, this disparity occurs despite more Mac users, 49% compared with 47%, reporting their computer has been infected by a virus. The survey also found that fewer Mac users use anti-spyware tools and firewalls. Where Mac users had higher rates of good security practice, it tended to be in areas where Apple provided built-in hardware such as TouchID and software like Time Machine.
The survey also found that Mac users are slower in installing system updates. Only 34% of Mac users said they did so immediately after they became available, compared with 48% of Windows users.
Relying on employees to update their systems or install security software on their own is not enough. Establishing a company-wide policy that mandates regular software updates, combined with automated patch management tools, ensures that vulnerabilities are addressed promptly across all devices.
Security incidents and their implications
The widespread use of Windows not just in homes and offices but also in hospitals, schools, airports, and other places where thousands of people rely on them means that security incidents affecting that platform tend to have a much bigger impact than those affecting Macs. This can be illustrated by looking at the impact of two recent incidents, one on each platform.
CrowdStrike update
In July 2024, a faulty update to CrowdStrike’s Falcon cybersecurity tool brought down checkouts in grocery stores, check-in desks at airports, and even a TV broadcaster. Banks, hospitals, and airlines were all hit by computer crashes. For a few hours, it seemed like all the computers in the world had crashed. In reality, it was only a few million. The faulty update exposed a flaw both in Falcon and the way it worked, and in the way Windows allowed some access to the system at the deepest level. While it wasn’t a cyber attack, the incident highlighted the importance of software reliability and rapid incident response protocols in place. For businesses that were affected, it wasn’t just about patching a bug; it was about getting back online, communicating with customers, and mitigating reputational damage.
HM Surf
By contrast, the impact of the HM Surf vulnerability that affected Macs a few months later was much, much more limited. HM Surf was a vulnerability in Safari’s transparency, consent and control (TCC) technology discovered by Microsoft Threat Intelligence. According to Microsoft’s security researchers, HM Surf could allow malicious code to bypass TCC and access sensitive user data like the camera microphone and location. The vulnerability was reported to Apple and patched in an update to macOS Sequoia.
Conclusion
Both Apple and Microsoft have made great strides in improving security in recent years. Apple and Mac users benefit from the tight integration of hardware and software and the fact that Apple has control over both. But Windows has a much more sophisticated anti-malware tool in Windows Defender.
It’s clear that those Mac users who still believe that Macs are somehow immune from viruses or malware are misguided, even if the threat to Macs is lower and the wider implications less serious. Users of both platforms should adopt robust security practices including, but not limited to: installing OS updates immediately; using reputable security software; paying attention to warnings about insecure web pages or potentially harmful software; and vigilance when reading messages and emails that contain hyperlinks.