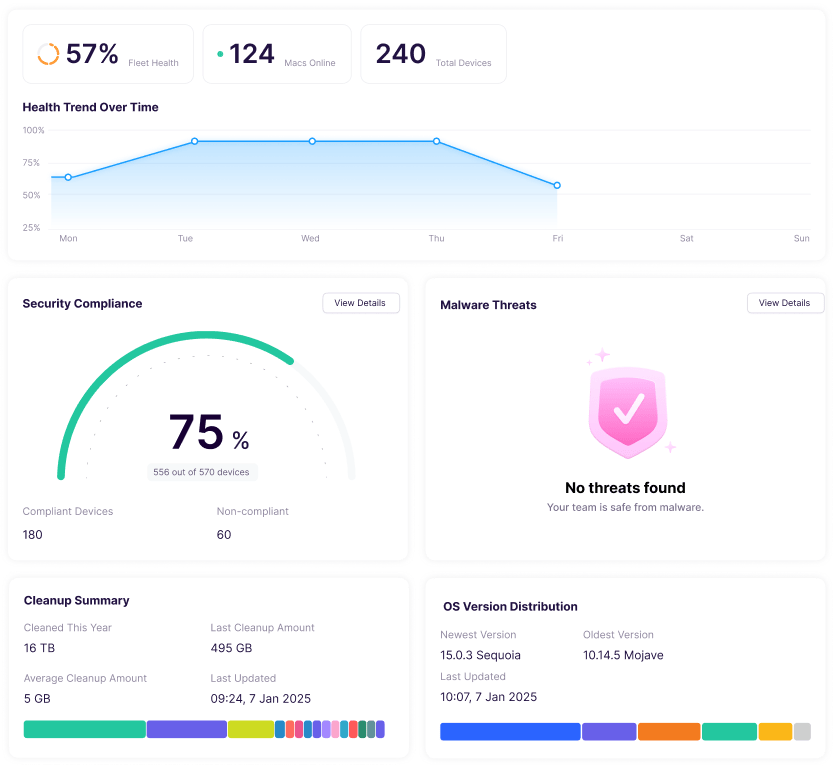
According to a recent survey by National Business Communications, 70% of office employees use their smartphones to work. So, whether your organization is a 5-person design agency or a 5,000-seat enterprise, your employees most likely use mobile devices for some part of their work activities.
This growing reliance on mobile devices in the work environment means the increasing need to manage them properly to secure your organization’s data. It is where MDM and MAM can change the game. But what are they, how do they differ, and which one should you choose for your business? In this article, we’ll answer these questions and even more.
What is MDM?
MDM (Mobile Device Management) is both a methodology and a toolset. It is designed to keep your organization’s data secure and, at the same time, provide your employees with productivity tools and applications.
This solution is used to manage both BYOD and corporate-owned mobile devices regardless of their operating system: iOS, macOS, iPadOS, Android, Windows, or purpose-built devices.
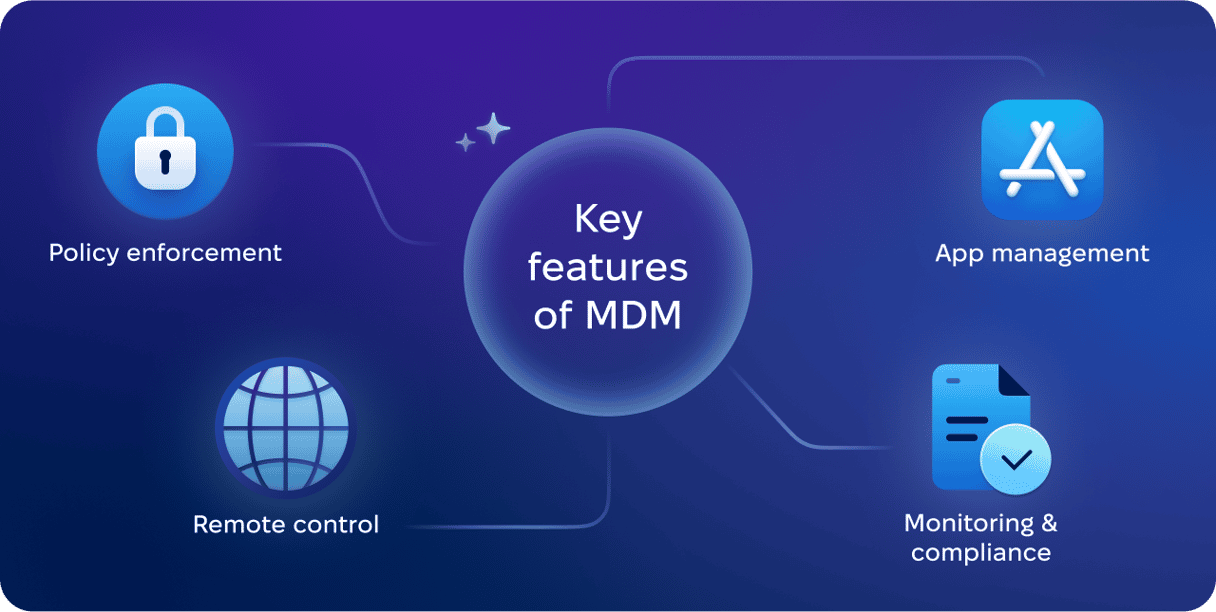
Key features of MDM
Here are some main characteristics of any MDM solution:
📌 Policy enforcement: IT teams ensure that devices comply with security policies. It is achieved by determining password policies and applying other policies, like allowed apps or encryption.
📌 Remote device control: IT teams can lock, configure, or wipe enrolled devices remotely.
📌 App distribution and management: IT teams can control which apps are installed and how they use data, as well as push any required apps on devices remotely.
📌 Monitoring, reporting, and compliance: IT teams can track the status of devices, their location, and security posture.
Pros | Cons |
Greater control over a device and enhanced security | Can seem overly intrusive |
Seamless device management | Raises privacy concerns, especially with personal devices |
Cost-effective and scalable | Limits employees’ control over their personal devices |
Convenient enrollment options | Employees may adopt shadow IT |
How MDM works
MDM solutions are based on containerization. Typically, it requires the creation of a profile or the installation of an agent that grants an organization control over the entire device. This way, it separates personal data and apps from corporate ones, thus ensuring and maintaining the security of data, devices, and mobile apps.
If a personal device is enrolled into MDM, it receives role-based access to corporate email and data, GPS tracking, VPN, password-protected apps, and any other elements you may find necessary for optimal data security. You can then monitor behavior on these devices and thus prevent malware or other cyberthreats.
What is MAM?
MAM (Mobile Application Management), unlike MDM, focuses on the security of apps and their data usage. It has emerged as a response to increased usage of mobile apps. MAM can be part of MDM.
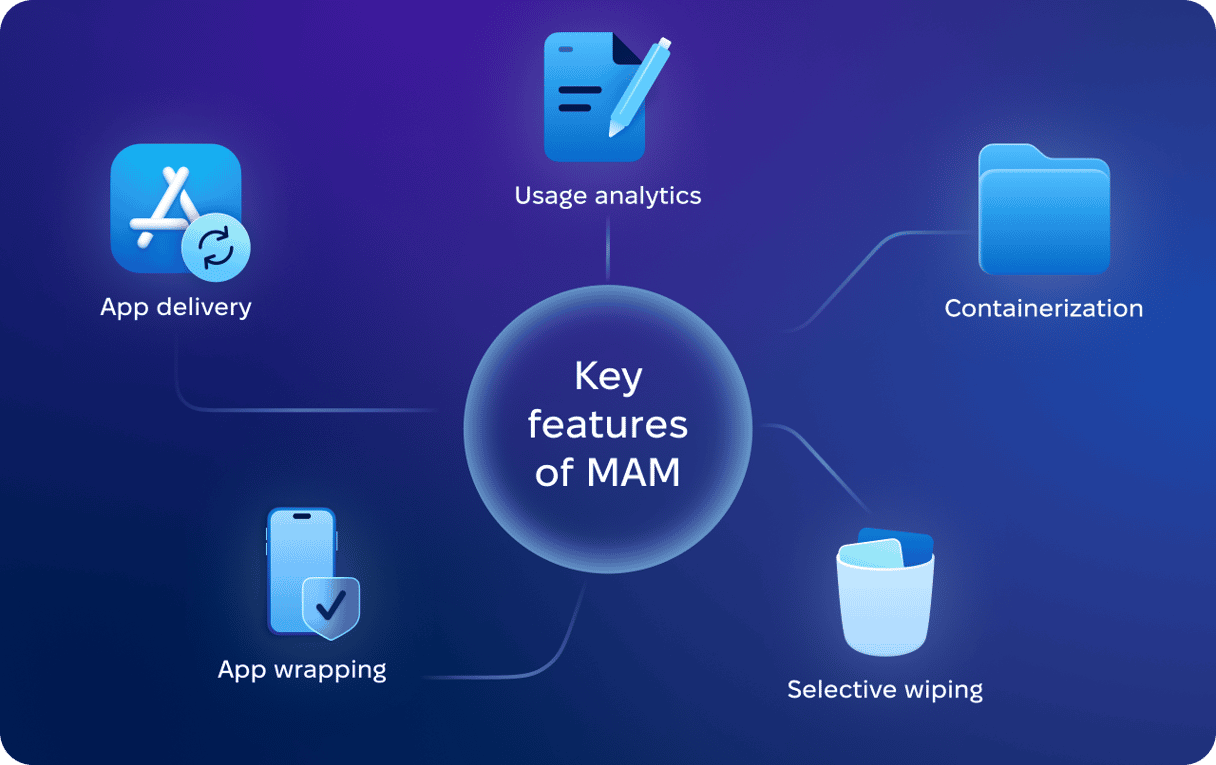
Key features of MAM
Here’s what MAM usually has to offer:
📌 App delivery: IT admins can both distribute and update apps to personal devices through enterprise app catalogs or app stores.
📌 App wrapping: An extra layer of management and security features, like copy/paste restrictions or data encryption.
📌 Selective wiping: The ability to remove corporate data without affecting personal content (on controlled apps only).
📌 Usage analytics: IT admins have reports on app installs, crashes, launches, and licensing.
📌 Containerization (not on all devices): MAM allows you to create a secure partition on a target device and separate personal apps and data from work-related ones.
Pros | Cons |
Easy corporate app management | Limited control over devices |
Lower risks of data breaches | Less comprehensive security (compared with MDM) |
Minimally invasive for an employee | Complicated enrollment |
Reduced IT burden | Can increase IT implementation costs |
How MAM works
Instead of enrolling an entire device into MDM, MAM works by either of these:
- Using OS-level frameworks
- Adding management code to apps before they are distributed
Unlike MDM, devices are not directly enrolled in MAM. Instead, when the user signs in with their corporate credentials, the apps they use connect to the organization’s MAM service that checks for existing MAM policies and enforces these policies.
MAM vs MDM: Top differences
What they manage and how they do it
- MDM provides device-level management for enrolled devices, which is achieved by standard app management (installation- and update-related).
- MAM provides app-level protection of corporate data, which is achieved by granular app management across the entire lifecycle of an app (installation, deployment, patching, and removal).
What they secure
- MDM focuses on device security by using functions like remote wipe, geo-location, or threat management features.
- MAM focuses on app security by using functions like automatic app removal under predetermined circumstances.
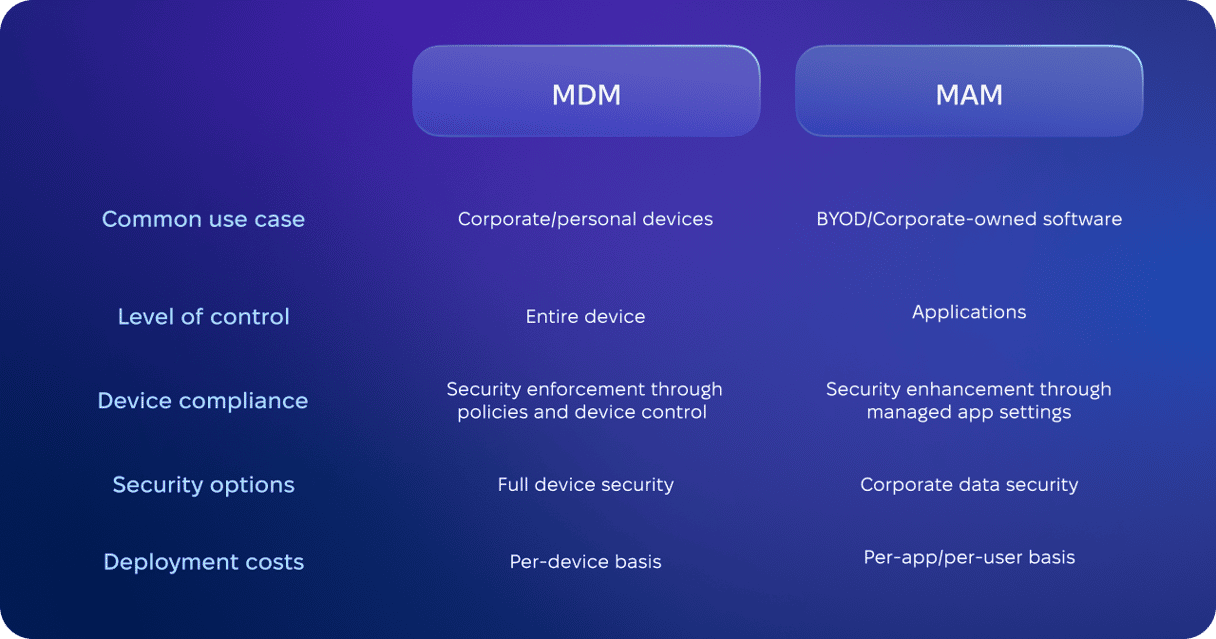
What they control
- MDM controls an entire device.
- MAM controls apps installed on a device.
How they approach app deployment
- MDM allows apps to be installed or pushed remotely.
- MAM allows apps to be installed or pushed by IT admins, or enables end users to install approved apps themselves.
How they are implemented
- MDM is more difficult to implement because it requires setting up servers and determining enrollment processes and device-wide policies.
- MAM is easy to implement because it requires simply distributing approved apps through existing channels.
What are their deployment costs
- MDM is priced on a per-device basis, and the costs depend on the number of functions an organization needs.
- MAM is priced on a per-user or per-app basis. Deployment costs are lower compared with MDM, but so is the level of customization.
What is their Total Cost of Ownership (TCO)
- MDM has higher TCO due to managing an entire device.
- MAM has lower TCO because the IT admin can choose to manage only critical apps.
MDM vs MAM: Which one you need
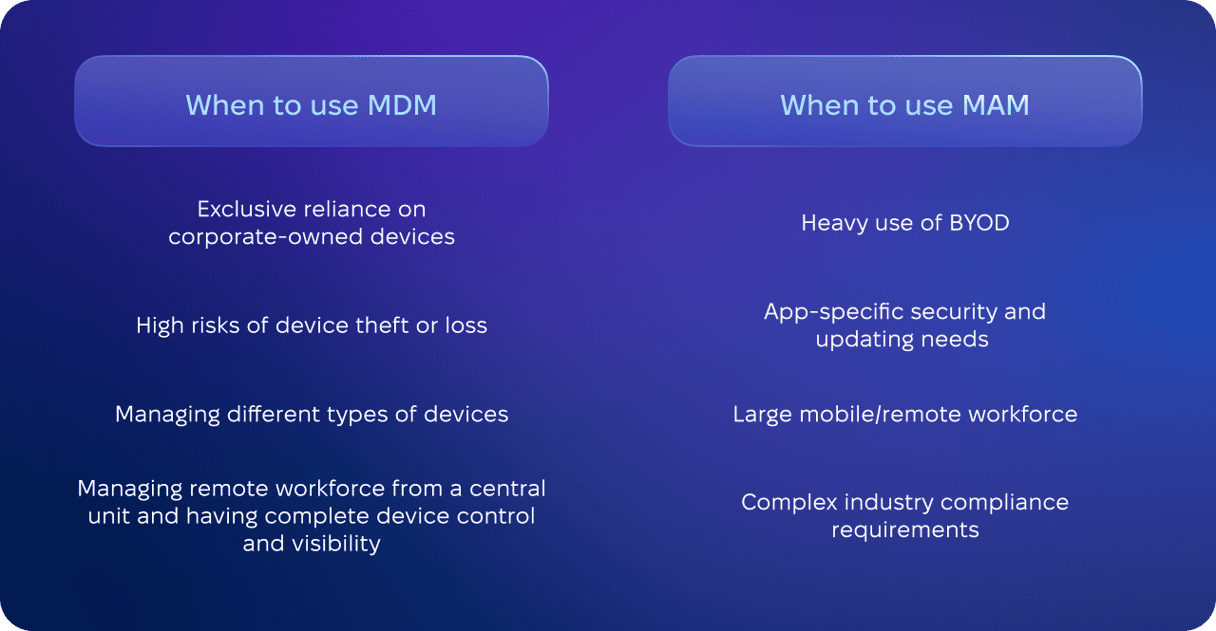
A general rule of thumb: if you need comprehensive control over security settings, compliance enforcement, and software updates on corporate-owned or personal devices, you need MDM. Also, if your organization works in highly regulated industries like healthcare or finance, invest in a reputable MDM solution.
However, if your organization supports BYOD but does not need complete control over personal devices or you need to enable enterprise mobility, MAM is a perfect option.
At the same time, if you need to be 100% sure about data and device security, you can implement MDM and MAM together. This may also be an option if your organization has a mixed approach to employment types, combining on-site, full-time, remote, part-time, and consultants. In such cases, consider unified endpoint management (UEM) tools that offer both of them.
Both MDM and MAM are valuable if you seek to improve security. They are both effective, but IT admins use them for different purposes. So, consider the size of your organization, its needs in terms of the degree of device control and data security, regulatory compliance requirements, and available budgets, and you will make an informed decision on which one is best in your specific case.