Who hasn’t started going stir-crazy working at home or from the office? It’s nice to get out and have a change of scenery while you’re working. Free, public Wi-Fi has made that entirely possible. But, before you connect to the first unprotected network you see at your coffee shop, you might want to think again. Unfortunately, there are scammers out there waiting to trick you. And this is why we can’t have nice things.
So, buckle up and keep reading. This article will outline what could happen to your Mac if you’re not careful enough about what networks you’re connecting to. I’ll also explain what an evil twin attack is and what you can do to protect your computer from one.
What is an evil twin attack and how does it work?
Let’s get down to it. What is an evil twin attack? Well, the easiest way to explain it is when someone sets up a Wi-Fi network that looks like an exact duplicate of another network. This is typically done in public places like airports and coffee shops — sites with a lot of foot traffic where users normally won’t know what the right Wi-Fi network is called.
Scammers set up these networks with the hopes of tricking strangers into connecting. This way, the bad actors will be able to track all of your internet activity, get access to your computer, and even install malware.
What’s the process for an evil twin attack? It’s not as complicated as you might think. In fact, many people online have broken it down into just four steps.
Step 1. Find the right location.
As you read earlier, it’s all about location, location, location. Scammers will typically pick a public place just because there are so many customers coming in and out that it’s very likely that a high number of those people will be trying to connect to Wi-Fi.
Step 2. Set up your wireless network.
This is why it’s called an evil twin attack. Hackers will actually set up Wi-Fi networks to mirror already available networks or even just look like they belong in the space. So, if you check available networks the next time you get coffee, you’ll probably see a “Coffee House” network. That said, scammers will set up their own network and call it something like “Coffee House Guest” instead.
Step 3. Encourage people to connect to your network.
Bad actors may even go as far as talking to the customers or people they’re trying to scam. They may hint to visitors about what networks they should connect to or recommend people switch because the speeds are so much faster.
Step 4. Steal data.
Once your device is connected to this phony network, the scammers are able to start tracking your browsing history and attempt to gain access to it too.
Why are evil twin attacks dangerous?
Evil twin attacks are usually so dangerous because they’re being operated by highly skilled people — they know what they’re doing and what they’re after. And they have the tools and resources to do it by any means possible.
Here’s just a short list of what a scammer can do to your Mac — yes, your Mac — if you connect to their bogus network:
- Steal information
- Track your internet activity
- Adjust your computer settings
- Install malware
How to detect an evil twin attack and protect yourself from it?
The biggest thing you’ll notice if your computer is under an evil twin attack is that it will get really slow. It may even overheat or drain the battery completely in a matter of minutes. It will do this because the hacker will be messing with your computer and installing malicious software to keep tracking you even after you leave.
Want to make sure you’re protected from attacks like this? I thought so. Here are a couple of tips:
- Avoid unprotected wireless networks in public
- Always use an encrypted VPN when connecting to a public Wi-Fi network
- Use your own hotspot
- Disable auto-connect so that you only connect to the networks you want to
- Use multi-factor authentication for all of your accounts
- Avoid logging into personal accounts on public Wi-Fi
What to do if your Mac is affected by an evil twin attack?
If you think your Mac might have been exposed to an evil twin attack, the most important thing is to change the passwords to any account you logged in to while connected to the rogue network. Chances are, the hacker that intercepted your internet connection was also able to capture anything you typed into your computer during that time.
Of course, more malicious attacks try to infect your computer with malware. But, as long as you regularly scan your Mac, you should catch anything suspicious that might be sneaking around your hard drive.
You don’t regularly scan your computer, do you? Well, you’re in luck. You can download the CleanMyMac app, and it will get rid of any malware it finds but also make sure your privacy settings are set up properly.
So, now you really have no excuse for not keeping your computer safe and protected. In fact, once you get it installed on your Mac, you need to take just a few steps to make sure your sensitive and private information isn’t stolen by a hacker. These are:
- Open CleanMyMac.
- On the left side, click Privacy.
- Click Scan.
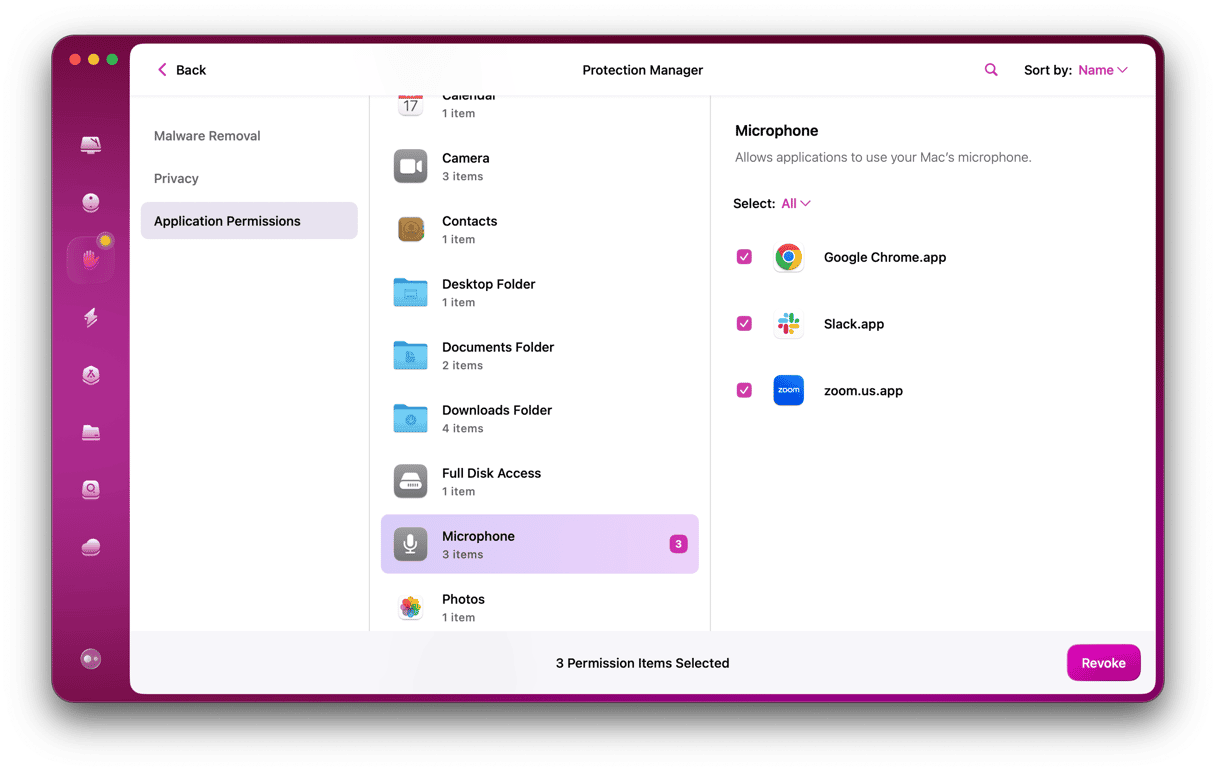
The privacy tool in CleanMyMac is great. It clears your browsing history and gets rid of any activity you performed on your computer. This way, if someone does try to hack into your Mac, there’s nothing for them to try and take.
Unfortunately, evil twin Wi-Fi attacks are becoming more common. But, hopefully, after reading this article, you’re feeling better equipped to protect yourself against any scams. You’ll know what to look for the next time you want to get a little work done while you enjoy a cup of coffee. Most importantly, though, now you know how to detect an evil twin attack and how to protect your Mac against one.