Locky is the nickname of crypto-ransomware that infects computers by encrypting files and preventing user access. Cybercriminals use it to scare victims into handing over money. They hold encrypted data for ransom and demand payment for a decryption key that can restore inaccessible files. But nobody guarantees that after making a payment, you will get your data back unscathed.
The good news is that you can remove Locky ransomware from your computer in no time without the need to pay the ransom. In this article, we’ll show you how to get rid of this malware in a few simple steps and protect your Mac from future threats.
What is Locky ransomware?
In February 2016, Locky authors used the Necurs botnet to run a massive spam campaign sending emails with malicious code called to encrypt users’ data. The ransomware quickly spread throughout the world but affected North America and Europe the most. Since that time, it has become one of the most ever-multiplying members of the ransomware family.
The initial extension of encrypted files was LOCKY. As the malware evolved, new editions emerged, along with new file extensions.
Locky ransomware attacks individual users and large businesses. One of the first and most significant attacks hit primarily the healthcare sector as well as the transportation, telecom, and manufacturing industries. The virus is best known for a high-profile infection at a hospital in Los Angeles, which paid a $17,000 ransom to recover its data.
How did Locky get on my computer?
Ransomware authors spread the infection via fraudulent emails similar to those used by Dridex malware focused on stealing banking information. The email is designed to make you believe that it comes from a reputable company. It always includes an attachment which you’ll be asked to download. Usually, it’s Word, Excel, or ZIP files disguised as an invoice. Here is a typical scam email with Locky virus:
Dear [Name],
Please find an invoice attached below. Make a payment according to the terms listed at the bottom of the invoice.
Let us know if you have any questions.
We greatly appreciate your business!
[Name]
How does Locky ransomware work?
Locky is a big player in the malware industry. It’s powerful enough to encrypt over 160 different file types, including videos, images, and Microsoft Office files. Although Locky tends to infect Windows, it also attacks macOS. Here is how it works:
- You download and open an attached document.
- The content in the document looks like gibberish.
- A warning message advises you to enable macros so that the content can be displayed correctly. But this social engineering technique is used as a bait to trick you.
- By enabling macros, you activate a malicious script that installs Locky malware on your computer.
- The virus begins to lock specific files, rename them to a weird combination of letters and numbers, and change their extensions.
Once the files are encrypted, Locky starts demanding ransom from you. It asks you to install the Tor browser and make a payment in Bitcoin (BTC) to get the decryption key. Generally, ransom varies from 0.5 to 1.0 BTC.
How to remove Locky ransomware
First of all, you should ignore it. Never follow the steps described in the ransom note. There is no guarantee that the scammers will keep their promises and turn your files back to life. By fulfilling their demands, you’ll encourage cybercriminals to expand their grim business and use your money to attack even more users.
To remove Locky virus, you need to fire up an anti-malware software and let it do its job. There are several useful tools available for Mac, both free and paid. We opt for CleanMyMac by MacPaw. It’s approved by Apple, which means we can completely trust this software.
With its user-friendly Malware Removal module, CleanMyMac turns Locky ransomware removal into a piece of cake.
Here is how to use it:
- Open CleanMyMac (download it here for free).
- Select Malware Removal from the sidebar.
- Hit the Scan button and let it look for malware.
- If anything suspicious is found, click Remove to get rid of it. That’s all!
How to protect your Mac from Locky
Prevention is always the best protection strategy. Stay vigilant and follow these simple tips to keep your computer safe from Locky or other types of ransomware:
- Avoid opening any suspicious attachments or links. Make sure you know and trust the source of the document before opening it.
- Disable all macros in Office for Mac by default, and never enable them in any dubious documents you get. Open Word, Excel, or PowerPoint, go to Preferences > Privacy, and configure desired settings.
- Regularly back up your files to cloud storage or an external drive.
- Install system and software updates and patches as soon as they are released.
- Develop a habit of scanning your Mac for malware. If you do not want to do it manually, consider using the background scanning tool that comes with CleanMyMac. To enable it, just open CleanMyMac Menu > Settings > Protection and select the checkboxes next to the second item.
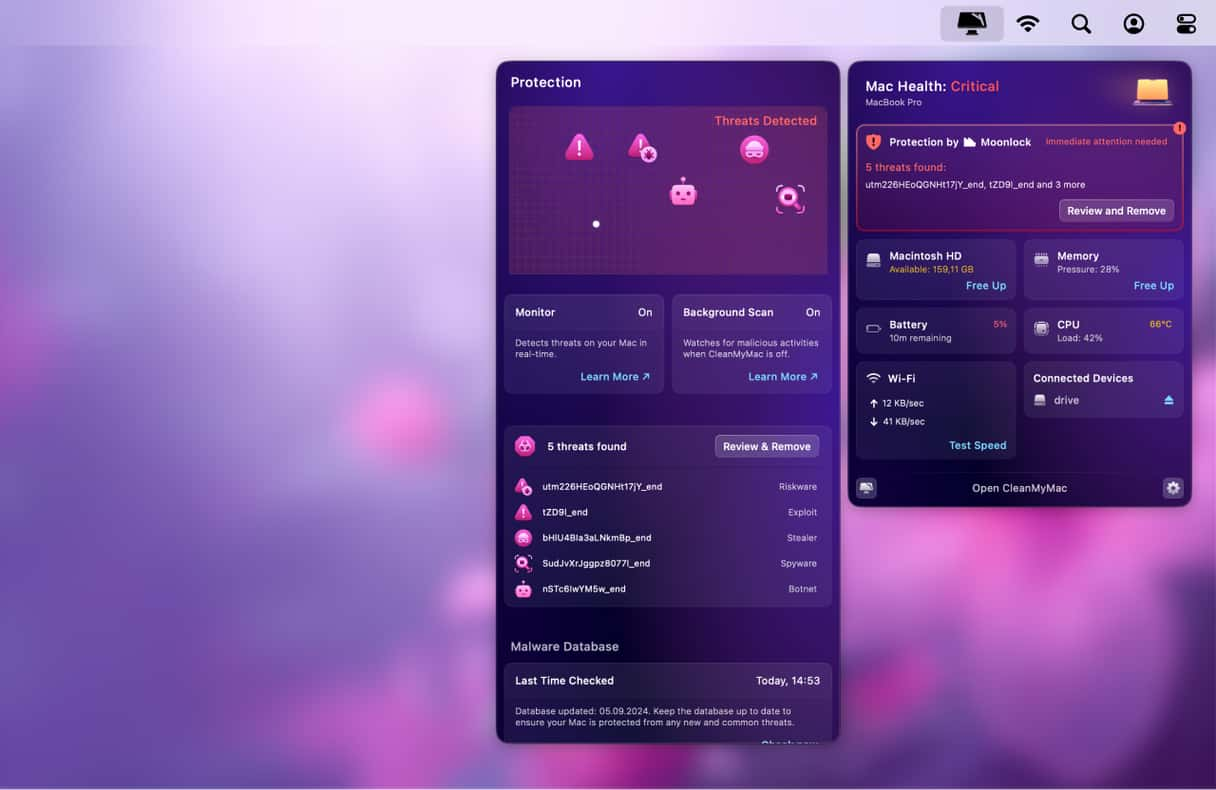
Locky operates all top ransomware features, such as colossal spam email campaigns, BTC payment gateway, different scripting languages, and server-side encryption. Luckily, it’s not too difficult to keep your Mac clean and protected from this or any other type of ransomware. With CleanMyMac, you can be sure that nothing goes unnoticed, thanks to its vast database of malware threats. It checks your Mac in a background mode, ensuring your data and files are in safety.