According to a recent report by Malwarebytes, Mac has become a more attractive target for malware and scams, given that its market share is constantly growing and it is becoming increasingly popular. Today, we’ll cover one such threat — Mac spoofing. In this article, we’ll explain how spoofing works and how to prevent attacks from toying with you or your business.

What is Mac spoofing?
Spoofing — or Mac spoofing attack — is a type of scam aimed at getting your personal information, along with passwords and banking credentials, in which a scammer pretends to be a legitimate organization, a friend of yours, or any other reliable business. In most cases, cybercriminals use the names of big businesses and trusted organizations to fool you into some kind of action. They make you believe that the information you get via emails, text messages, or calls is trustworthy, and you might not even notice when you start disclosing your data or downloading malware.
There are different types of spoofing, and the classification depends on the channel cybercriminals use for distributing the scam. Most of them are also common Mac spoofing attacks. These are the following:
- Email spoofing — sending emails from fake addresses pretending to be a reliable and trusted organization (such as Apple and Apple support scam).
- Website spoofing — designing a fake website that looks just like the website of a reputable institution.
- Caller ID spoofing — falsifying phone numbers to make you believe that you know it or someone who is calling.
- Text message spoofing — sending an SMS with malicious links or another call to action (such as persuading you to call a particular phone number).
- GPS spoofing — deceiving a GPS receiver by broadcasting a fake signal from the ground so that all navigators start showing the wrong location
- IP spoofing — creating IP packets with a false IP address and pretending to be a legitimate sender, which is commonly used in denial-of-service attacks.
- DNS server spoofing — modifying the server to reroute a specific domain name to another IP address.
- ARP spoofing — sitting on your network and trying to crack your IP address and intercept all of the information to and from your computer.


How to prevent Mac address spoofing?
In order to avoid spoofing Mac address, add these methods to your cyber arsenal:
- Always double-check to whom you provide personal and sensitive information. Any email asking for your password, Social Security number, or other personal details could be a trick.
- Pay close attention to the URL of the websites you visit, especially if you aim at going to the website of a bank or any other organization storing your personal information.
- Be careful when answering phone calls and text messages, especially when a caller or sender is unknown.
- Take extra precautions to make your network safer: use firewalls and stronger authentication methods and ensure that unused services and ports are disabled.
- Turn on spam filter.
How to stop Mac spoofing?
The following steps will help not only prevent spoofing attacks but also keep your Mac safe.
Tip 1: Stick to two-factor authentication
Remember, passwords keep unwanted visitors out of your accounts. That’s why when it comes to protection, two-factor authentication is one of the most effective defenses available. It strengthens login security by requiring the second piece of information — usually a temporary code delivered by your phone.
When setting up two-factor authentication, most services allow you to use text messages. When logging in, you will receive a confirmation code on your mobile device. You just have to enter this code to confirm that you are trying to log in.
Here’s how two-factor authentication looks on Facebook:

Tip 2: Don’t click on unknown links or attachments
Email is a major source of concern with regard to spreading malware. Therefore, you need to be careful with all the letters you receive. Don’t download and open file attachments if you don’t know the person the message is from; just delete it. Also, never click on unknown links, as they may start downloading malware to your Mac. Any personal information you give away could help someone steal your identity.
Tip 3: Install antimalware software
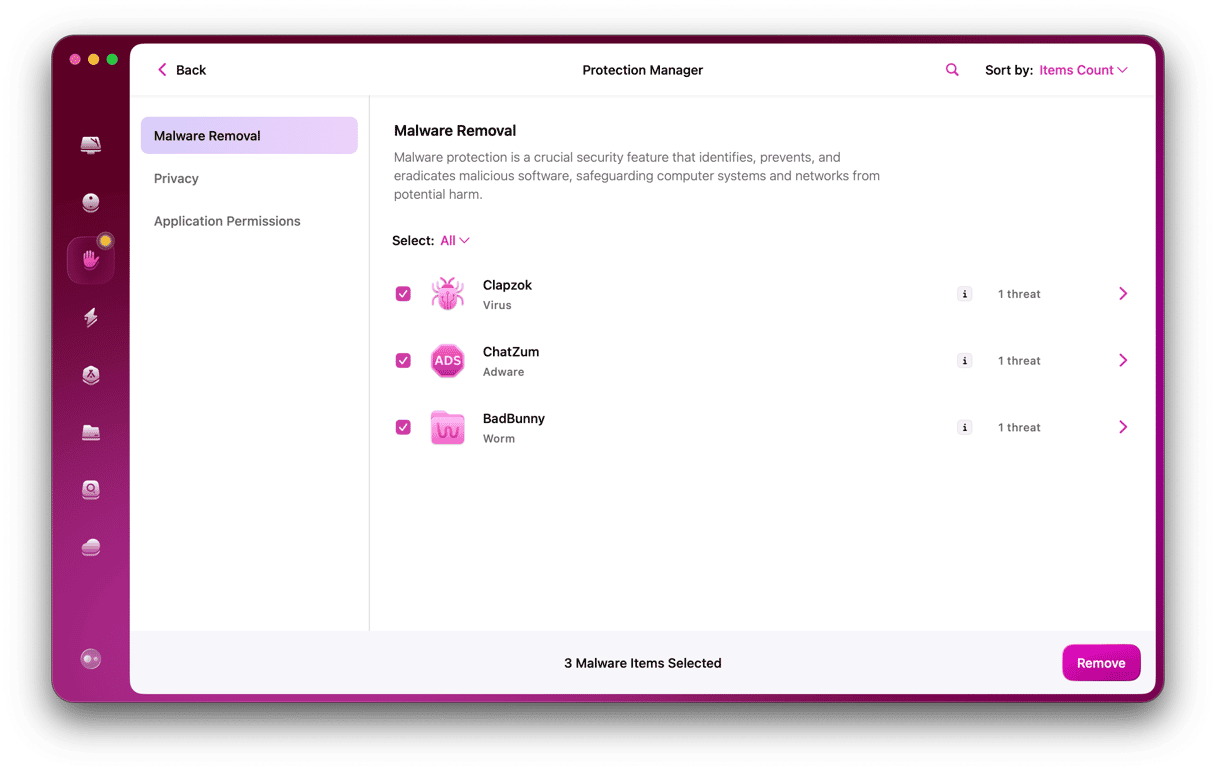
If you suspect a link you clicked downloaded something to your Mac, run a thorough scan of your system with a tool like CleanMyMac. Its Malware Removal module can easily detect Mac spoofing, malicious DMGs, and other files that you’ve been tricked into downloading. With the help of CleanMyMac, you can easily protect your system from worms, viruses, miners, and other malware threats.
Follow these simple steps to run a malware scan on your Mac:
- Start your free CleanMyMac trial (Apple-notarized app).
- Open the app and choose the Malware Removal tab.
- Click Scan.
- Click Remove to eliminate the found threats.
Moreover, CleanMyMac has a real-time malware monitoring feature. It checks your system for suspicious activity and informs you about potential threats. This feature is running in the background and takes care of your system 24/7.
Except for the Malware Removal tool, CleanMyMac has a lot of useful modules to keep your Mac protected. It’s used in more than 185 countries, making Macs as good as new. Note that the application is notarized by Apple and is running smoothly on the latest macOS version. Check it out — someone has to protect your Mac.
Tip 4: Avoid giving away your personal information online
Here’re a few simple things to keep in mind:
- Don’t needlessly disclose your date of birth, favorite pet’s name, or mother’s maiden name online — these things are often used as basic security questions.
- Don’t give away personal information on social networking sites.
- Don’t share your passwords and other sensitive data.
- If you are asked to fill out a profile of yourself, don’t give unnecessary personal information.
Tip 5: Remain extra vigilant
Spoofing can sometimes be easy to spot, but not always. Cybercriminals use sophisticated ways to trick you, so you always need to stay careful. Pay close attention to the web addresses of the sites you visit, links you open, and calls you receive. Caution is your greatest protection.
With these prevention methods and strong antimalware software, you can stop spoofing attacks and keep your personal data intact. Stay safe!