Do you want to stay really private online and leave no trace of your online activities? The best thing you can do is to try a VPN service, a special tool created to ensure users’ safety and security online. But the main point here is VPN connection logs. Despite claiming a no-logs policy, some VPNs actually log every single action their users make online. But if a VPN keeps logs it means a privacy breach. Use a reliable rock-solid ClearVPN to stay safe when browsing.
Reasons for VPN providers to collect/log users’ data
Settings and efficiency optimization
Connection logs are important for network configuration and possible limitations of use problems.
Marketing purposes
Selling browsing logs containing users’ data to third parties is a source of income.
Analytics
Logs can be collected for different analytical purposes. It’s OK if used for Google Analytics to know the number of website visits only.
To detect anomalies
Companies can use logs to alert the users in case of anomalies in behavior. It helps to set up a good combination of alerts individually for their cases. Logs audit helps to understand how well VPN works.
Spying agencies force them to log
National agencies force VPN companies to keep users’ personal information and disclose it upon request. It can even include a gag order.
VPN logs types
1. Connection logs (or metadata logs)
They can encompass your and VPN’s IP addresses, connection details (date, time, session duration), amount of bandwidth consumed by the user.
2. Browsing logs
These are usage logs that usually contain such data about a user's activities as IP addresses, the number of connection times, user’s browsing/download history, the most used servers.
3. No-logs or zero log
User’s activities aren’t recorded at all.
What are VPN connection logs?
Connection log files record users’ multiple online activities. They represent the least noticeable form of logging and a user can’t be identified directly. It isn’t very dangerous for user’s privacy because it includes the data about VPN sessions but it doesn’t contain any information about the content of the user’s encrypted messages. In case if connection logs contain the user’s IP address it can cause the user’s VPN account identification which means a privacy leak. VPN connection logs consist mainly of the list of the incoming and outgoing VPN server connections. It can be one piece of data or a combination of several ones:
- Incoming IP address (User’s real IP address)
- Outgoing IP address (It is assigned to the user by the VPN server)
- Time frameworks (All the period of a VPN session from the beginning to the end and also its duration).
- Data (All the data downloaded/uploaded/transferred and used during the user's online session).
- Connection frequency (How often a user is connected to the server)
Many VPNs declare they collect no data while they still store connection logs. Frankly speaking, it’s almost impossible to ensure VPN’s performance if no data is logged, especially when it refers to connection logs that are technically demanded. So, read carefully your potential VPN provider’s policy before you start using it.
Why are connection logs important?
- Technical aspect
These logs are helpful to monitor how servers are loaded, manage the traffic and ensure the normal functioning of the network.
- Focus on improving the service
Technical assistance specialists use this data to improve the performance, solve some technical troubles/issues, and troubleshoot the services.
- Control users’ simultaneous connections
Because the number of connections is limited by the devices of one service subscriber.
- Bandwidth usage limiting
The bandwidth usage data management for VPNs is tracked according to its monthly limits.
VPN logs policy and storage duration
VPNs are tools created to protect users’ personal data. But VPNs can collect a big number of connection (and sometimes even browsing) logs and get access to users’ IP addresses, the most popular sites one visits. Many VPN providers abuse users’ collected data and sell it to third parties. When choosing a VPN service make sure its logging policy is clear and meets your security needs.
The privacy policy is where you’ll find the information about VPN client connection logs storage time on the VPN’s servers. Be attentive and read the document carefully before accepting its terms and conditions! It makes a significant difference if your logs are stored 24 hours, half a year, or even more. If a VPN stores connection logs, the less time it keeps them, the better. It’s really good when connection logs are deleted right after the user’s online session is over.
Why you should worry about VPNs that store connection logs
- Users can be identified based on online activities.
- They can share and sell data to third parties for targeted ads and user’s analysis
- Authorities or hackers can access unencrypted hard drives.
- Legal authorities can request to identify the user.
It is essential to know about any connection logs VPN provider collects about the users. There are reasons for some concerns in the case of IP address logs. The IP address is individual, when this data is logged and stored it can be shared with third parties. Users can’t feel private or anonymous because it is easy to know the user’s country, city, ISP, or even ZIP code. Also, some VPNs aren’t honest and transparent enough about connection logs because these logs aren’t considered to be a problem for users. Avoid VPNs that log the user’s originating IP address. Your data is safe only with a VPN that keeps no connection logs just like ClearVPN does. ClearVPN has a strict no-log policy. You can read more about it here.
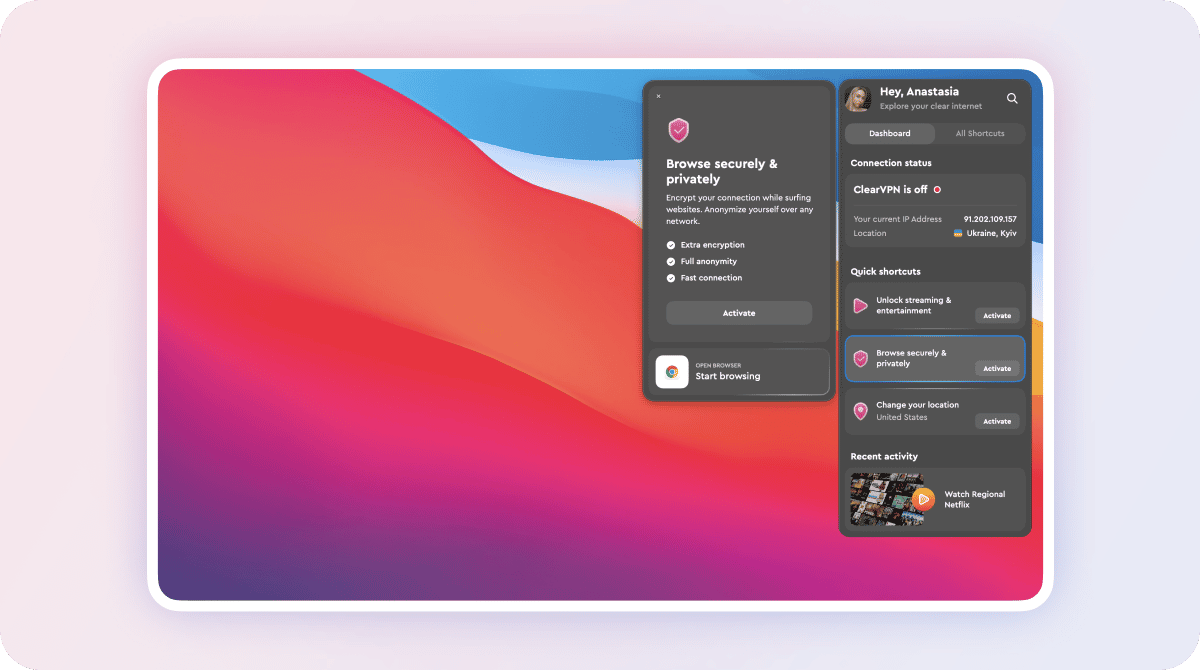
Try out ClearVPN to secure your online journey while being sure you leave no online trace:
- Install ClearVPN on your device (we use macOS as an example in the picture below)
- Open the app and activate Browse Privately and Securely shortcut.
- That’s it! Your online journey is protected and private.
To conclude
Striving for privacy is the reason why we use a VPN. But potential VPN users are confused about VPN logs. What kind of VPN connection logs do they keep on you? Are they dangerous or not? Honesty and transparency in the VPN policy are crucial. Still, some companies assure you they don’t keep logs of your online activities. To make the whole picture and make a decision in favor of a VPN service, users need to consider jurisdiction and test results.
You won’t need to worry about it using a recognized and credible Clear VPN. All your online activities and digital footprints will be protected along with your digital identity.