Malware comes in many different forms — from adware to worms — that spread quickly and cause serious problems for major computer systems. WannaCry was an attack that exploited a flaw in Windows in order to extort money from users and gained notoriety around the world.

What is WannaCry?
Launched in May 2017, WannaCry was a ransomware attack that used a cyberworm to target Windows computers and encrypt data on them. It then demanded a ransom payment in Bitcoin to unencrypt the data.
WannaCry used an exploit developed by the US National Security Agency called Eternal Blue, which was released into the wild by a group of hackers called The Shadow Brokers. Eternal Blue exploited a vulnerability in Windows’ implementation of the SMB networking protocol and only worked on older Windows computers. Microsoft had already released a patch for it by the time WannaCry was released. However, many organizations had not applied the patch to their machines and were left vulnerable to the attack.
Despite Microsoft releasing an emergency patch and the discovery of a kill switch that stopped computers that were infected from spreading the worm, meaning that the attack only lasted a few days, it was estimated that more than 200,000 computers in 150 countries were hit. Estimates of financial loss varied between hundreds of millions and billions of dollars. Affected organizations included Boeing, Honda, and the UK’s National Health Service. Several governments, including the UK, US, and Australia, asserted that North Korea was behind the attack.
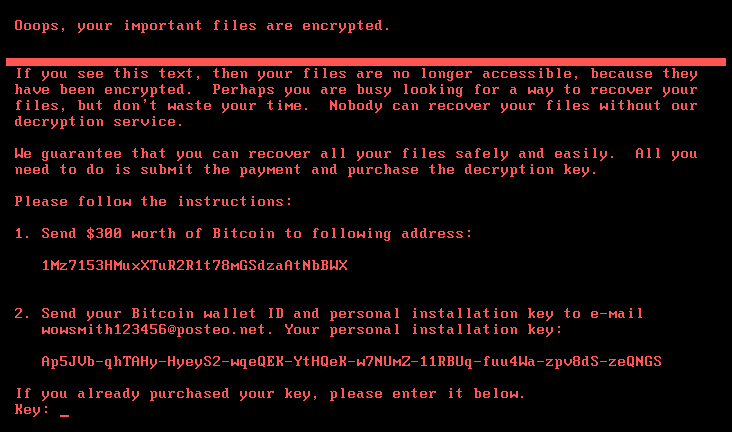
This is how WannaCry and similar viruses typically look like:
Who was behind the WannaCry ransomware attack?
Governments and intelligence agencies in the US and UK investigated the WannaCry attack and determined that it was carried out by the Lazarus Group.
The Lazarus Group has been connected to North Korea’s Reconnaissance General Bureau since 2009. They’re responsible for other high-profile incidents, such as the Sony Pictures hack and stealing $80 million from a Bangladesh bank.
North Korea naturally denies involvement in the WannaCry ransomware attack, but it’s undisputed by others whether North Korea was involved.
How was the WannaCry virus stopped?
The WannaCry virus was eventually stopped after Microsoft pushed out an urgent security update to patch the vulnerability. But WannaCry was permanently stopped in its tracks with the discovery of a “kill switch.”
A British security researcher, Marcus Hutchins, was examining the WannaCry code and discovered a domain name hardcoded into the ransomware. He quickly realized that WannaCry would be stopped if it checked to see if the domain name was active.
Hutchins discovered that the domain name was available. So, he bought it and activated the domain, and it killed the ransomware in its tracks. This didn’t remove the ransomware that was already on computers. It did, however, stop it from spreading elsewhere.
How do I know if my computer has been infected by WannaCry?
The good news is that the WannaCry attack is now over, and in any case, it only affected Windows machines. So if you’re using a Mac, you don’t have to worry about it. The only exception is if you were using Boot Camp or a virtual machine to run Windows on your Mac. In those circumstances, if you were running an old version of Windows, it was possible to be infected.
Windows users whose machines were attacked saw an alert on the screen telling them that their files had been locked and that in order to unencrypt them, they would have to pay between $300 and $600 in Bitcoin.
Is there a Mac equivalent of the WannaCry virus?
There’s no direct equivalent since WannaCry exploited a vulnerability in Windows. However, there have been and will be again ransomware attacks that affect Macs. For example, in 2016, a ransomware attack known as Patcher was distributed via BitTorrent, disguised as a tool to crack the authentication in Adobe Premiere CC and Microsoft Office 2016. And also in 2016, the KeRanger ransomware targeted Macs by hiding in downloads of BitTorrent client Transmission. Since then, Macs have become an even more attractive target for malware developers.
How did the WannaCry ransomware work?
The WannaCry malware used an unpatched exploit called Eternal Blue in Windows computers, which was originally discovered by the National Security Agency.
Before it was stopped, WannaCry had infected over 200,000 computers in 150 countries, causing billions of dollars in damage. It targeted government agencies, hospitals, and businesses, one of which was the British National Health Service.
How did the WannaCry ransomware spread?
The Eternal Blue vulnerability targeted an unpatched Windows vulnerability, affecting file- and printer-sharing features. This allowed hackers to remotely place malicious code on the target device.
It then looked for other computers on the same network which had the same vulnerability. The WannaCry virus then “jumped” onto that machine and began looking for another target to infect. After landing on each target computer, the files on that system would immediately be encrypted by the ransomware.
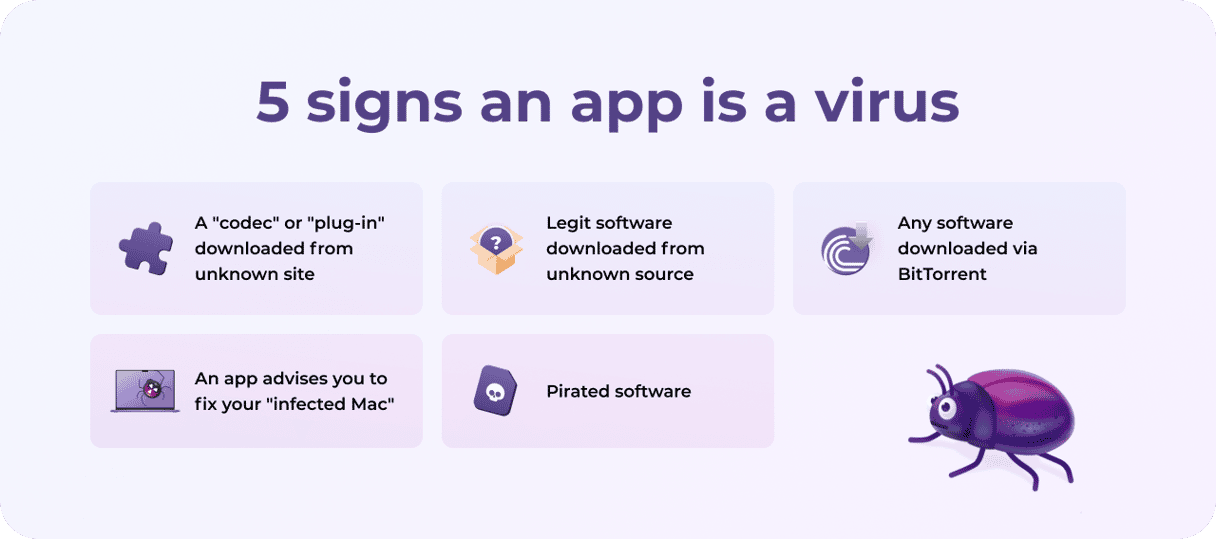
How can I avoid downloading ransomware?
The first thing you should do is be careful where you download software from. When you download cracked copies of software via torrent, pirated movies, or any tool that claims to allow you to circumvent copyright or license protection, you’re taking a big risk. Legitimate downloads have also been sources of ransomware in the past — the Transmission trojan was linked to from the official Transmission website — but it’s far less common.
Installing antivirus software will also help protect you. And backing up regularly will mitigate the effects of files being encrypted because you can just roll back to the backup.

How to remove WannaCry virus
As we said above, WannaCry only affected Windows computers, so here is how to remove it from Windows. Before you start, make sure you’ve updated Windows will the most recent patches.
- Click on the Start menu.
- Type Windows Defender into the search box.
- Double-click Defender to run a scan.
- If it finds anything, use Defender to remove it.
If you can’t run Defender or it can’t remove the virus, the next step is to run a third-party antivirus tool and use that to scan your PC and remove the virus.
If you have files that have already been encrypted, the simplest solution, if you have a recent download, is to use that to recover versions of the files before they were encrypted. If you don’t have a backup, there are a number of tools available online that claim to decrypt files encrypted by WannaCry. You should do your own research on these and only download one when you’re satisfied that it does what it claims to.

What should I do if I think my Mac has a virus?
If you think you’ve been infected by ransomware, the most effective method for removing it would be to use CleanMyMac, powered by Moonlock Engine. However, we need to clarify a few things before we continue.
CleanMyMac is most effective at removing ransomware as soon as it enters the computer, so you have to act fast. Once the encryption process has started, the ransomware can be removed, but the encrypted files cannot be decrypted.
This is why daily file backups are so important. If you get hit by a ransomware attack, the best option is to use CleanMyMac to remove the ransomware, then use Time Machine to remove the encrypted files and replace them with the backups.
Alternatively — and this may be a better option — you can use macOS Recovery Mode to reset the system completely. Or you can wipe and reset the entire system back to factory settings.
At the very least, you should run a deep scan with CleanMyMac to ensure that all traces of the ransomware are detected and removed.
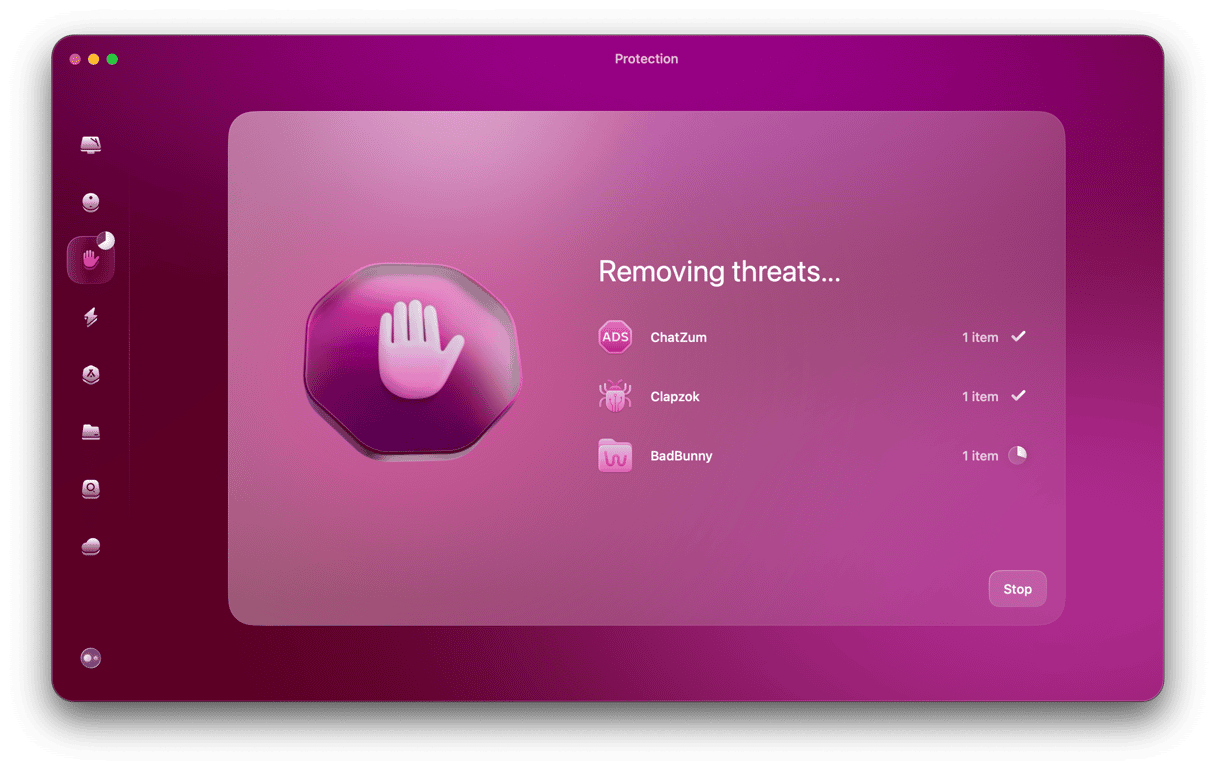
Here’s how to use CleanMyMac to remove ransomware:
- Get your free trial here
- Open CleanMyMac and select the Protection feature on the left.
- Click Configure Scan and select everything, especially Deep Scan. This is very important.
- Exit Configure Scan and now click Scan.
- CleanMyMac will start scouring your Mac, looking for all traces of ransomware. When the ransomware has been found, CleanMyMac will show you all instances of malware. Select them all and click Remove.
For newer ransomware variants, the Deep Scan option will definitely be required.
That’s it!
The WannaCry virus only affected Windows computers. However, Macs running Windows in Boot Camp or in a virtual machine could have seen those copies of Windows affected. The virus exploited a vulnerability in Windows’ implementation of SMB and encrypted files on the infected computer, demanding a ransom to unencrypt them. Microsoft released a patch, and if you have an old Windows machine that’s infected, the best way to remove WannaCry is to update and use Windows Defender or an antivirus tool.