In CleanMyMac X, suspicious are the applications developed or hosted in Russian
Federation and Belarus, as
these apps may
threaten your Mac or the safety of your data. You can find these apps in the Suspicious category of the
Uninstaller module.
You may ask:
- Why are apps from Russia and Belarus suspicious?
- What can I do with a suspicious app in Uninstaller?
- Why an app is marked as suspicious although it’s not related to Russia or Belarus?
- What are the criteria to detect suspicious apps?
- What if I think an app is not suspicious and can prove that?
Let's find the answers in this article.
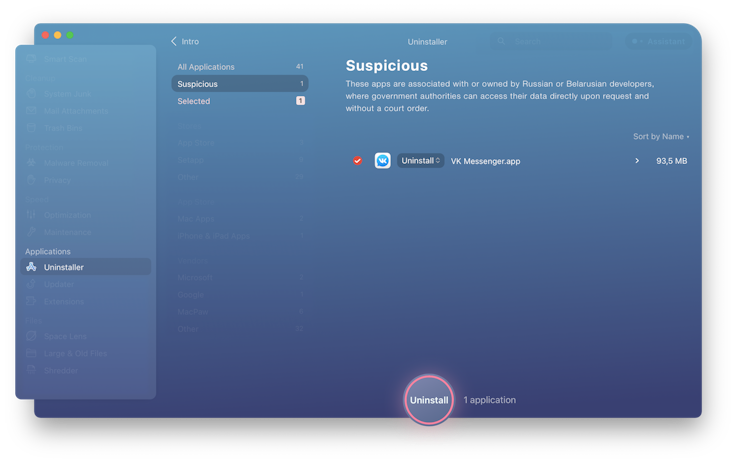
Why are apps from Russia and Belarus suspicious?
Local laws (like 374-FZ and 375-FZ) oblige many app developers to store data on servers in Russia and Belarus. Law enforcement agencies can easily access that information, often without a court decision. Moreover, Russia and Belarus may use software to attack other nations and break people’s right to privacy. We at MacPaw feel it's our responsibility to alert users of such dangers, thus defending their right for privacy.
You may also remove suspicious apps and support the worldwide boycott of businesses cooperating with Russia and Belarus — the states that lead an unlawful and brutal war against Ukraine.
For more details, see the criteria that CleanMyMac X uses to identify suspicious apps. We also explain our motivation to add suspicious apps to the Uninstaller in the MacPaw blog.
What can you do with a suspicious app in Uninstaller?
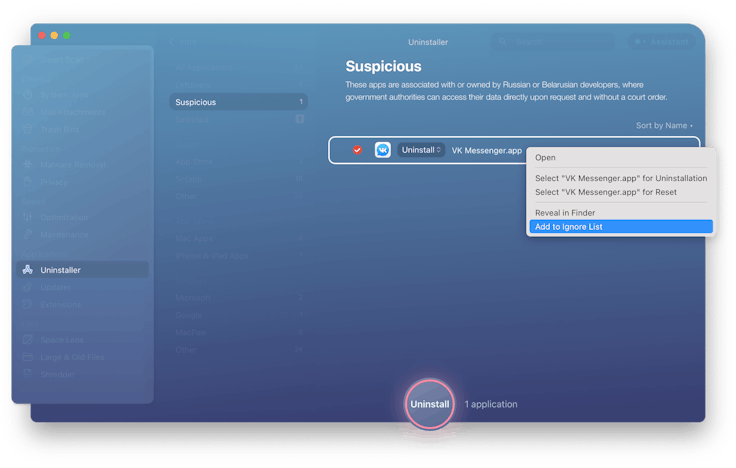
- Uninstall the app completely.
- Reset it to original state.
- Add the app to the Ignore list so that the Uninstaller doesn't show this application again.
Uninstaller marks an app as suspicious, although it’s not related to Russia. Why?
Apps that seem unrelated to Russia but have code signing certificates pointing to Russia are probably cracked.
Hackers who break software often insert their own digital signatures instead of the apps’ native certificates. For some hackers, cracking apps is a way "to manifest the strength and greatness of Russia,” their homeland. That's why the Uninstaller detects any app as suspicious if it has:
- a code signature tied to Russia, or
- the
ruelement in its bundle ID
In the end, if an app can be traced back to Russia, it's most likely insecure. The app may spy on you and bring harm — either because it was designed like that or because it was cracked. Or, your personal data in the app may be exposed to Russian law enforcers. We’ve discussed these risks earlier in this article.
Please note: detecting cracked software is not a dedicated CleanMyMac X feature.
Now, what if the Uninstaller claims an app suspicious because of its Russian traces, but you think the app is not
related to Russia — and may still be safe? Here’s our recommendation for such cases:
- Uninstall the suspicious (cracked) app.
- Download the latest app version from a reliable source (for example, the developer’s website).
- Install the app anew.
If you have questions, don’t hesitate to contact our Support Team.
Criteria that CleanMyMac X uses to detect suspicious apps
The Uninstaller module scans all apps installed on your Mac and identifies an application as suspicious if it matches any criteria below. Criteria 1 and 2 are purely technical; they only require an automated check on your computer. Criteria 3, 4, 5 involve verifying if an app is mentioned in the Suspicious Apps Database.
The MacPaw team carefully curates this Database together with the software development community and socially responsible people across the globe. We do our best to avoid bringing safe apps to the Suspicious Apps Database. Before making a decision, we study information from different sources, consult security experts, compare various opinions, and try to contact the app developers whenever possible and reasonable.
Criterion 1. Application contains the ru element
in any part
of its bundle ID
Bundle ID is the main programmatic identifier of any app in the Apple ecosystem. This ID usually includes a direct reference to the app developer and their country of origin. The App Store review team verifies bundle IDs thoroughly, so we can be sure the app is related to Russia.
Surely, developers of suspicious Russian apps may reside in other countries or hide their origin. For such occasions, we maintain the Suspicious Apps Database, which is based on the criteria below.
Criterion 2. Application's code signing certificate indicates Russia as a country of origin
Code signing is a security technology with which developers certify that they have created or updated an application. Apple utilizes code signing certificates to assure users that an app is from a known source and hasn’t been modified since developers last signed it.
A certificate pointing to Russia means an app has been developed there, which already makes the application potentially insecure. But it might also imply that hackers have cracked the app and replaced its authentic certificate — to emphasize they did it from Russia. You could have accidentally downloaded this cracked app from an untrusted source; more details are in the section about cracked apps.
Criterion 3. Application data is stored or processed on servers located in Russia or Belarus
The legislation of these countries allows governments and affiliated agencies to access vast amounts of private or commercial information stored on local servers, without user consent or a judicial order. Thus, when you use apps hosted in Russia and Belarus, your data is at high risk of exposure.
Criterion 4. Application developers, owners, or beneficiaries are registered in Russia or Belarus
Laws oblige most companies with local registration to store and process data on servers in Russia or Belarus, making this data an easy target for law enforcers (see Criterion 3).
There’s another risk yet: app developers who successfully work in Russia and Belarus may cooperate closely with the state. Apps developed by these developers can be used as an asset in government-led cyber attacks. Such apps may spy on you, steal your data, or harm your computer.
Criterion 5. Application developers, owners, or beneficiaries have a functioning office in Russia or Belarus
Every legal entity in these countries is under the risk of pressure from law enforcement authorities like the FSB (Federal Security Bureau). Using that pressure, authorities can access company-related information even when application and data servers are located beyond Russia and Belarus. If you’re using an app created by such a company, your data is also at risk.
MacPaw doesn’t consider this criterion as decisive. However, we’re using it as an extra proof or an aggravating circumstance for adding an app to the Suspicious Apps Database.
Do you think an app is safe and should be removed from the Suspicious Apps Database? Tell us!
We're cautious about declaring apps as suspicious, and we appreciate any feedback that could help us improve.
If you're a CleanMyMac user and you're sure an app is not suspicious, please let us know. Any proof or details would be helpful, but if you don't have extra info—write to us anyway, and we'll do a research.
App developers are also welcome to contact us at [email protected] and
provide proofs that your application
doesn't fall under the Suspicious criteria. We don't have strict requirements for such
proofs as
we're always open to a productive discussion.
