As malware researchers in Moonlock, the cybersecurity division of MacPaw, we are always on the lookout for new samples to analyze and protect our users from. One day, we came across a sample with the name CleanMyMac, which caught our attention. However, this sample was not the genuine CleanMyMac, but a malicious impersonation.
We decided to investigate this campaign further and uncovered many more samples with different malware inside, such as Atomic Stealer, PSW Stealer, and AdLoad Adware. These malware can steal users' passwords and personal data and display unwanted ads on their Macs. The samples had different file types, such as macho files, dmg, shell scripts, etc. Fortunately, our Lab is always updating the rules to detect such threats, and users who use the official CleanMyMac with the Moonlock Engine will be safe from these attacks.
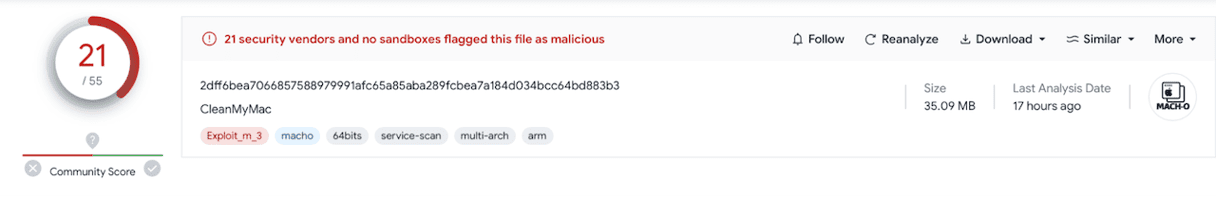
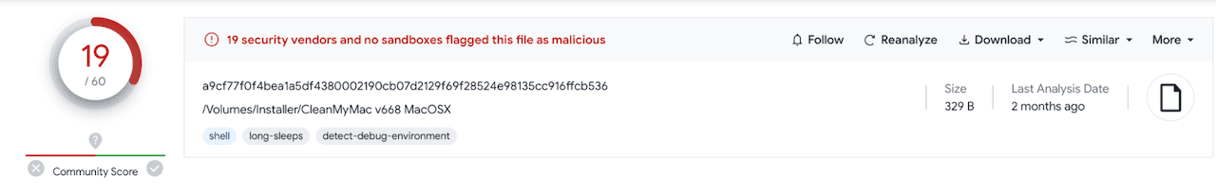
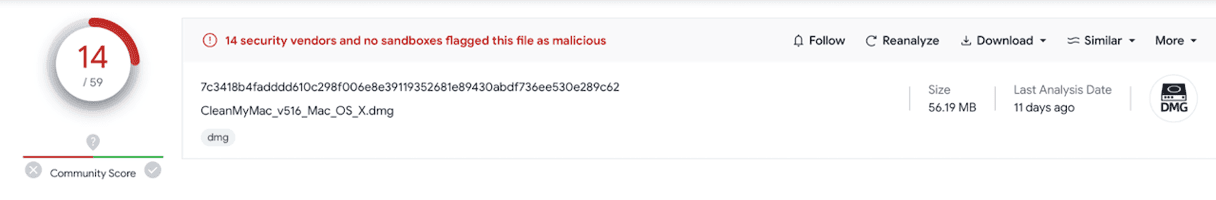
How cybercriminals spread CleanMyMac impersonation
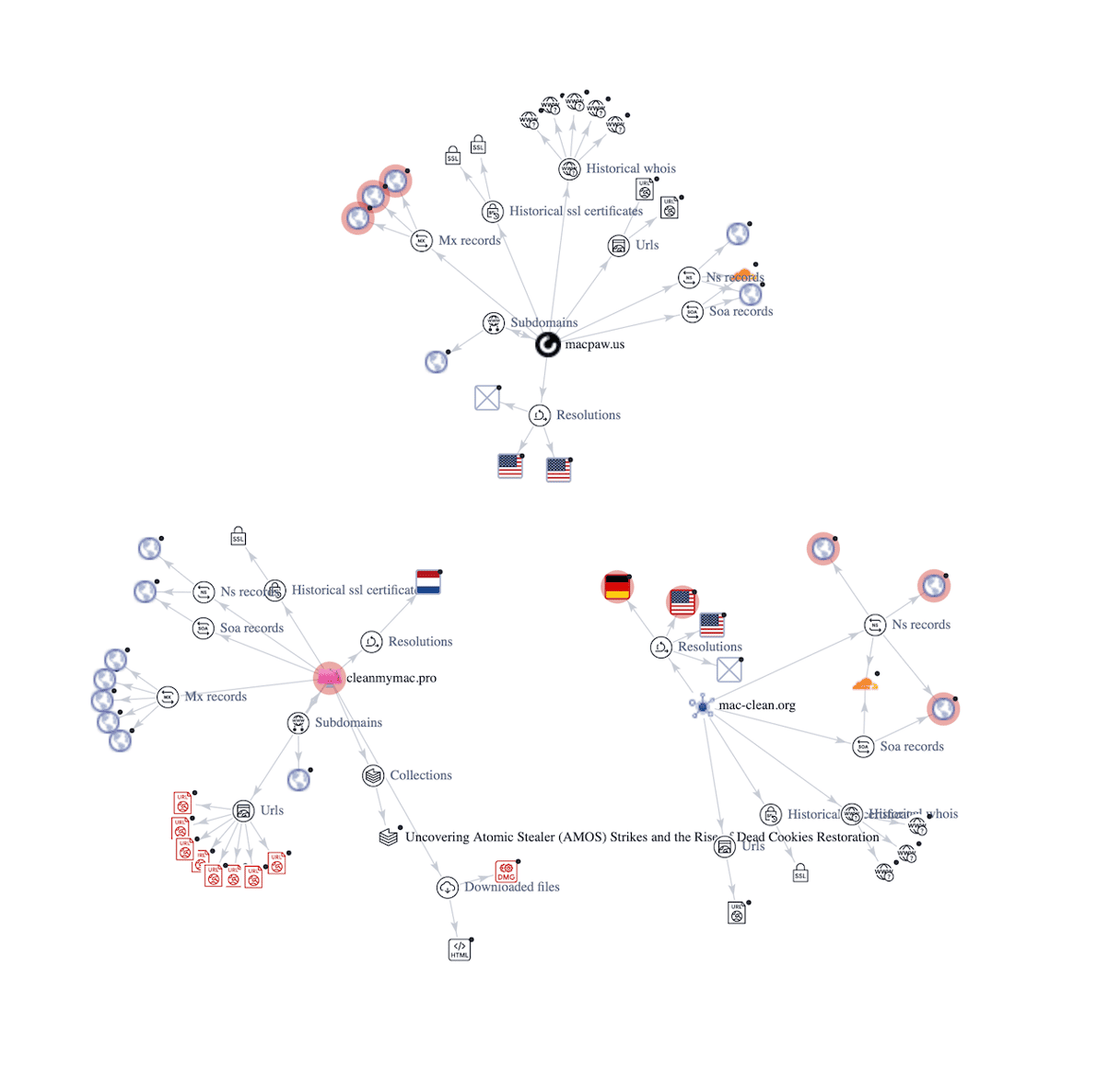
However, not all users are aware of the dangers of downloading software from untrusted sources. We found several pages from which the malicious software was distributed. These were phishing pages that leveraged MacPaw's name and logo and manipulated users' trust. Among these pages were macpaw[.]us, cleanmymac[.]pro, mac-clean[.]org, and others. These pages looked very similar to the official MacPaw website but had subtle differences and errors. For now, these pages do not respond, but they might resurface under different domains.
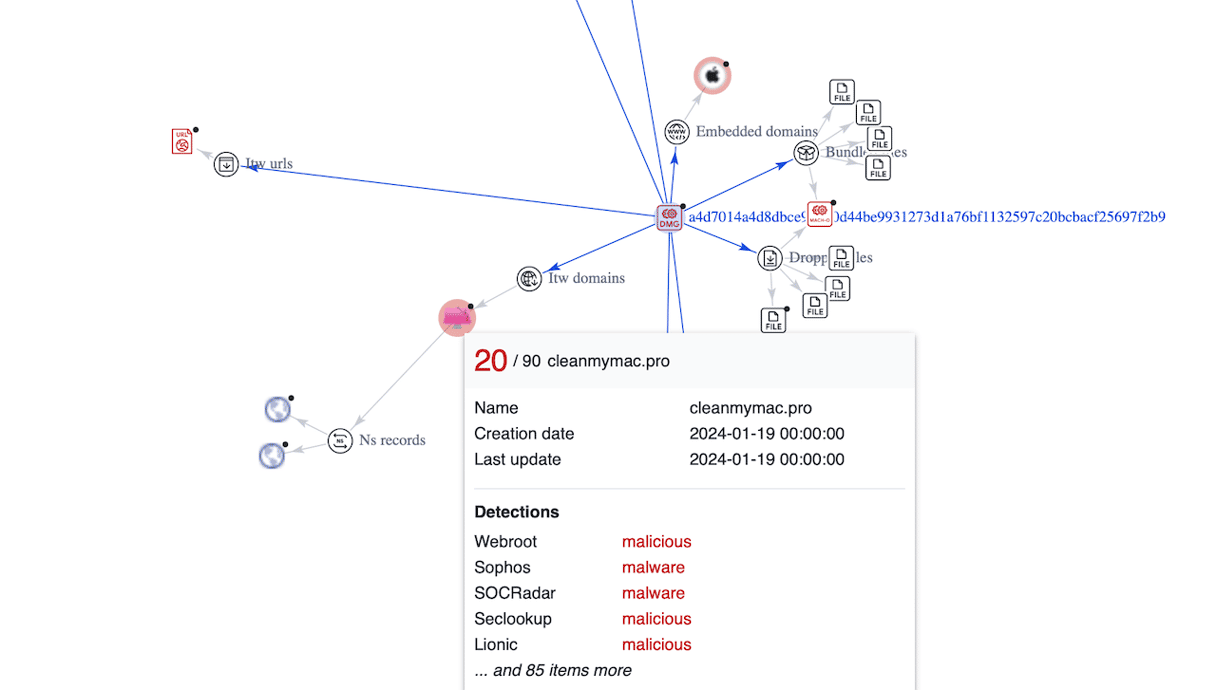
![Malicious URL 'cleanmymac[.]pro' scan results](https://cdn3.macpaw.com/cdn-cgi/image/format=auto,quality=60,width=608,dpr=2/images/content/CleanMyMac%20impersonation10_1711017561.png)
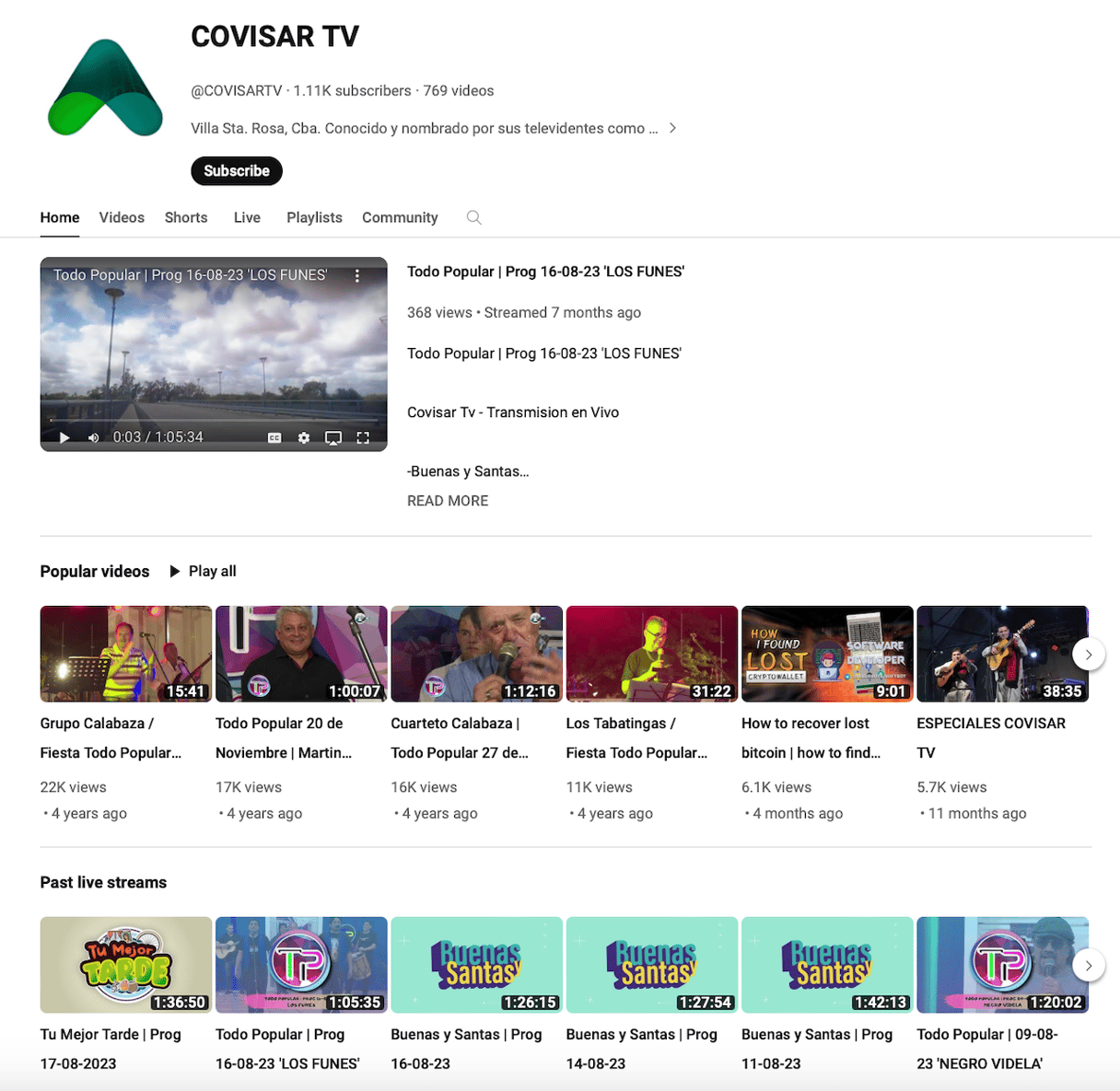
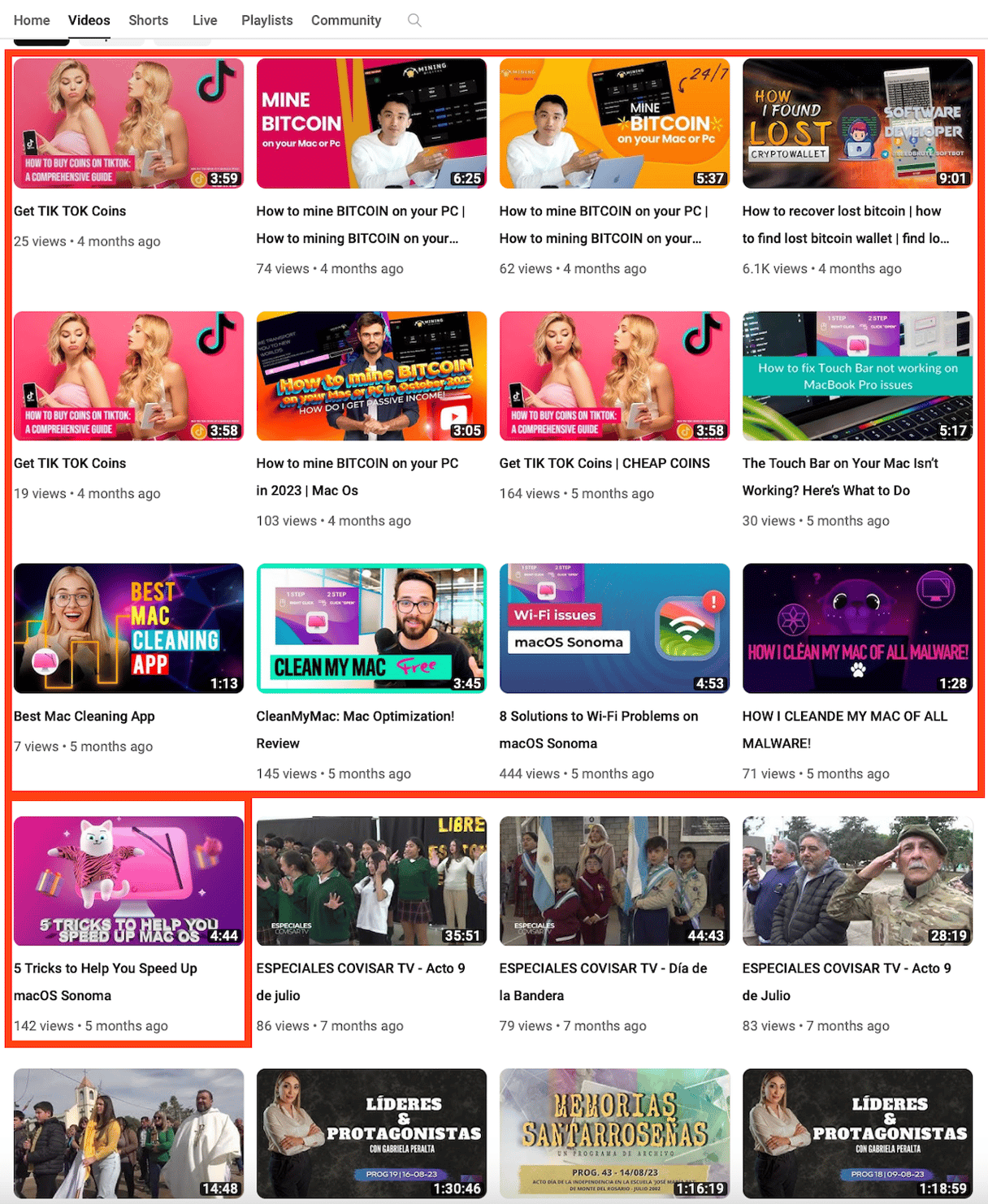
Phishing URLs are not enough to spread malware, so the attackers also use different channels to promote their software. For example, YouTube channels. When we searched for "cleanmymac x free download full version" on YouTube, we uncovered dozens of videos from a hijacked YouTube channel called COVISAR TV.
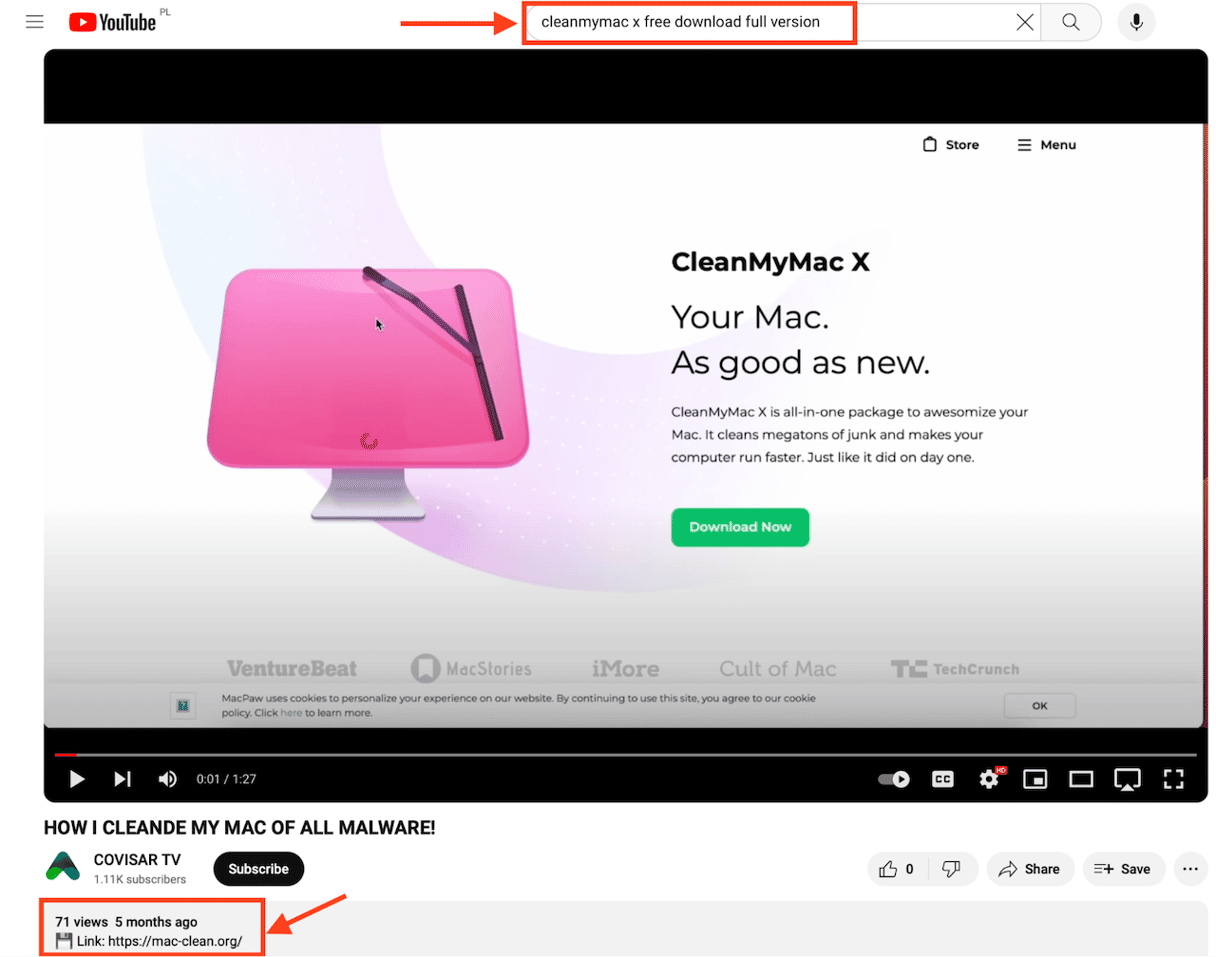
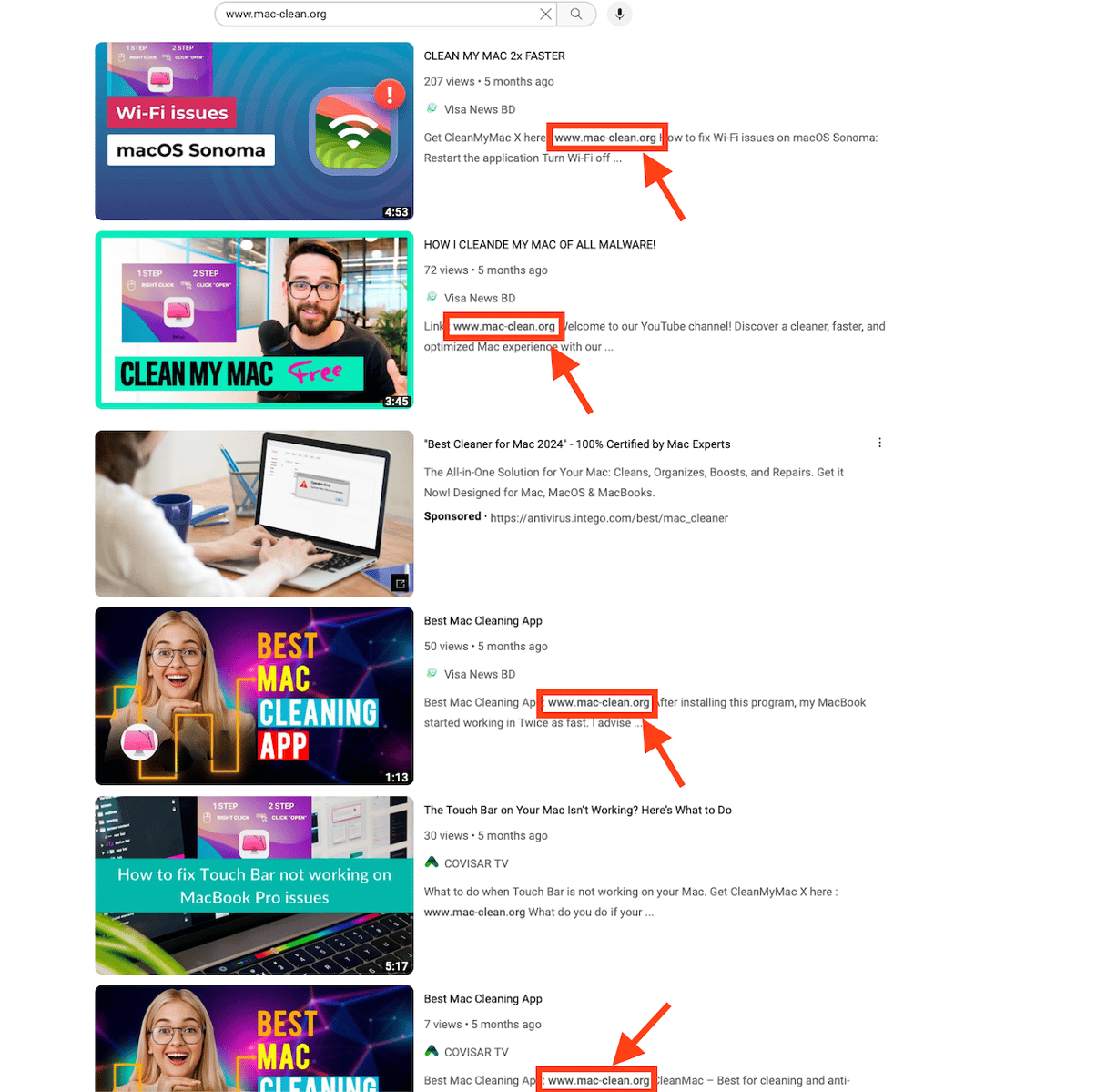
This channel had nothing to do with MacPaw or CleanMyMac. It had many videos of Portuguese musical bands, but the last videos were all about CleanMyMac and how to mine or recover bitcoins. These videos have links to the phishing pages in their descriptions. This looked like a scam, and indeed, MacPaw's security team confirmed that they had no idea what the advertising campaign and website were.
How to protect your Mac from malware
This is just one example of how cybercriminals can impersonate legitimate software and companies to trick users into downloading malware. Impersonation attacks are a serious threat to users' security and privacy, and they can cause financial, emotional, and reputational damage. Therefore, it is important to raise awareness about these attacks and how to prevent them. Here are some tips to avoid falling victim to impersonation attacks:
- Always download software from the official website or the App Store. Do not trust links from unknown sources or third-party websites.
- Check the website URL before downloading anything. Look for spelling errors, unusual characters, or different domains. For example, the official MacPaw website is macpaw.com, not macpaw.us or macpaw.pro
- Verify the identity of the sender or the publisher of the software. Look for signs of authenticity, such as digital signatures, certificates, or reviews. If you are unsure, contact the company directly and ask for confirmation.
- Use a reliable antivirus or Mac cleaner software, such as CleanMyMac with the Moonlock Engine, to scan your Mac regularly and remove any threats. Keep your software updated and follow the security recommendations.
By following these tips, you can protect yourself and your Mac from impersonation attacks and enjoy a safe and smooth online experience 🙂
MITRE ATT&CK® Techniques
Tactic | Technique | Procedure |
Execution (TA0002) | AppleScript (T1059.002) | Executes Apple scripts and/or other OSA language scripts with shell command 'osascript' |
Execution (TA0002) | Scripting (T1064) | Executes commands using a shell command-line interpreter |
Persistence (TA0003) | Plist Modification (T1547.011) | Writes property list (.plist) files to disk |
Defense Evasion (TA0005) | Hidden Files and Directories (T1564.001) | Reads file resource fork extended attributes and creates hidden files, links and/or directories |
Defense Evasion (TA0005) | Obfuscated Files or Information (T1027) | Mach-O contains sections with high entropy indicating compressed/encrypted content |
Defense Evasion (TA0005) | File and Directory Permissions Modification (T1222) | Executes the "chmod" command used to modify permissions; Sample tries to set the executable flag |
Defense Evasion (TA0005) | Code Signing (T1553.002) | Sample is code signed by an ad-hoc signature |
Discovery (TA0007) | System Information Discovery (T1082) | Reads the systems hostname, OS release and/or type, the system or server version plist file, the sysctl safe boot value (probably to check if the system is in safe boot mode) |
Discovery (TA0007) | Security Software Discovery (T1518.001) | Uses the "uname" system call to query kernel version information (possible evasion) |
Discovery (TA0007) | Process Discovery (T1057) | Reads process information of other processes |
Exfiltration (TA0010) | Exfiltration Over Alternative Protocol (T1048) | Executes the "curl" command used to transfer data via the network (typically using HTTP/S) |
C&C (TA0011) | Application Layer Protocol (T1071) | Malware communicate to C&C server |
Indicators of Compromise (IOC)
Indicators | Description |
7c3418b4fadddd610c298f006e8e39119352681e89430abdf736ee530e289c62 | AdLoad Adware |
96f80fef3323e5bc0ce067cd7a93b9739174e29f786b09357125550a033b0288 | PSW Stealer |
2dff6bea7066857588979991afc65a85aba289fcbea7a184d034bcc64bd883b3 | PSW Stealer |
a9cf77f0f4bea1a5df4380002190cb07d2129f69f28524e98135cc916ffcb536 | Downloader |
be14c0850391fadb4b2056c6c8aeba44251a093a48210d45a5958632e87d0a18 | Atomic Stealer |
51048464b4fe5d0ed4a6a6fe4e30528fc815bff12f0cbb4cf57dc44ac2ea168d | Atomic Stealer |
3805cb7589da01a978e899fd4a051adec083c8543343ce637e448716cbbbcef1 | Atomic Stealer |
a4d7014a4d8dbce95960d44be9931273d1a76bf1132597c20bcbacf25697f2b9 | Atomic Stealer |
cleanmymac[.]pro | Phishing Site |
macpaw[.]us | Phishing Site |
www[.]mac-clean[.]org | Phishing Site |
https://cleanmymac[.]pro/files/CleanMyMac-App[.]dmg | Malware Download URL |
https://www[.]YouTube[.]com/@COVISARTV/videos | YouTube Channel where suspicious CMM URL is being promoted |
https://www[.]YouTube[.]com/@visanewsbd6404/videos | YouTube Channel where suspicious CMM URL is being promoted |