Racoon infostealer is one version of a breed of so-called ‘infostealer’ malware that targets web browsers and steals information stored by them on your computer, such as login usernames and passwords, details of sites you’ve visited and searches you’ve done, and even financial details if they are stored by your web browser. In Raccoon infostealer’s case, it’s targeted at Windows PCs. However, there are other infostealers that are targeted at Macs. So, learning about how Raccoon infostealer malware works and what you can do to protect against it is important and will help you deal with other infostealers if you encounter them.
What is Raccoon infostealer malware?
Raccoon infostealer is malware that was first detected in 2019. It’s sold on forums on the dark web as malware-as-a-service (MAAS) and charges a weekly or monthly fee for its use. It’s targeted at Windows systems, and once deployed on a system, it targets browser autofill passwords, history, cookies, credit cards, usernames, passwords, cryptocurrency wallets, and other sensitive data. It has infected hundreds of thousands of systems since it was first released and is one of the most widely discussed malware tools on dark web forums.
In addition to targeting browser data, it has custom modules that target cryptocurrency applications, password managers, email clients, and other applications. Some versions of Raccoon also allow it to be a ‘man in the middle’ between the host system and the internet, stealing data that uses that connection.
The Raccoon infostealer network temporarily closed down in 2022 but returned later that year. And in October 2022, one of the alleged hackers behind the malware was indicted by a US Grand Jury on charges of conspiracy to violate the Computer Fraud and Abuse Act, having previously faked his own death.
How does Raccoon infostealer malware work?
The first thing to say is that Raccoon is designed specifically to work on Windows systems. However, there are very similar infostealers that target Macs. Raccoon uses the process injection technique to hijack legitimate browser processes and create new ones that target cache files, steal the data from them, and send it back to a host server. It also targets the SQLite database used by web browsers and steals autofill passwords, credit card data, cookies, and browser history. Although Raccoon encrypts the data it steals, it doesn’t use sophisticated antidetection techniques, so it can be picked up by good IT security tools.
Once the data has been stolen, it can then be used by the hackers to target bank accounts and credit card accounts or to impersonate the user from whom it has been stolen. More likely, the data will be sold to multiple different parties, who will each use it to commit theft and fraud.
Why is the Raccoon infostealer considered dangerous?
The Raccoon infostealer is malware that isn't exactly subtle. It's dangerous because it is extremely effective malware that's designed to grab as much private, sensitive data as possible.
This data includes but is not limited to saved passwords, browser cookies, credit card details, crypto wallet credentials, and even autofill details on your browser. Since many people save their credit card details and home addresses in the autofill, this alone makes Raccoon extremely dangerous. Therefore, you should remove Raccoon Stealer as quickly as possible.
The Raccoon stealer locates data by digging through your browser, your files, and your apps. It steals everything and sends it via your Wi-Fi network to a server controlled by the hacker. This data is then sold on the dark web to unscrupulous third parties or is used by the hackers themselves.
Since Raccoon stealer malware is malware as a service (MaaS), the risk is greatly increased. This is because anyone, regardless of their technical knowledge, can purchase access to this malware and use it to start stealing from other people. In other words, with the help of Raccoon, anyone willing to pay can become a cybercriminal.
How does Raccoon infostealer infect your Mac?
Needless to say, Raccoon malware does not ask for permission to enter your Mac. It finds a variety of ways to penetrate your Mac without your knowledge:
- The most popular and most effective way is by sending out malware-infected web links in phishing emails, SMS messages, and chat messages. Once the victim clicks on the link, it leads to a malware-infected file, which then installs itself on the target computer.
- The Raccoon stealer may come bundled with software you consider to be legitimate. When you install the software you want, Raccoon will install itself in the background. This is why you should never buy software from outside of the Mac App Store or from recognized developers. Downloading free software is also a bad idea.
- Another method of entry is via torrent file downloads and/or websites that provide downloads of cracked software. Cracked software commonly has malware hidden inside it.
- Browser extensions installed from outside the browser’s official extension site can also be a culprit. These outside sources don’t have the safeguards that are normally in place to stop malware.
- The final method is when the victim clicks on a malicious ad. This can lead to malware-infected software, or it could take the user to a sketchy website with malware in the background.
What infostealers target Macs?
In the past, infostealers tended to only target Windows machines. However, with the surging popularity of Macs, cybercriminals are quickly pivoting to specifically targeting Mac computers.
Today, there are many versions of infostealer malware targeting Macs. Let's look at some specific examples of Mac-targeting infostealers:
- The biggest player when it comes to Mac-targeting info stealers is Atomic Stealer (AMOS). This one is a classic example of malware-as-a-service. It's usually distributed on Telegram with a subscription fee that's reported to be somewhere in the region of $1,000 per month. According to reports, Atomic Stealer comes as a malicious DMG file and is specifically designed to attack iCloud keychain passwords, crypto wallets, and autofill data in the browser.
- Another example of an infostealer is KeySteal. Like other popular stealers, KeySteal attacks the macOS keychain and tries to extract and steal the passwords contained inside.
- If you were starting to think that fake Adobe Flash Player installers were being left out here, then don't be disappointed. OSX.CrescentCore poses as a fake update to install launch agents on your Mac. It is said to be a rather basic form of infostealer compared to Atomic Stealer, but it is nevertheless dangerous and does its job very effectively.
- MacStealer is a newer infostealer, but it's becoming a much worse threat to Mac devices. This one is particularly nefarious because it is able to bypass the built-in security features normally found in macOS. Once inside, it will steal your private browser data, Apple ID login, passwords, and cookies.
How to protect against infostealers
Like a lot of malware, infostealers like Raccoon and Atomic rely on a user downloading malware to their Mac. There are lots of different ways hackers can do this, including phishing emails and messages, fake downloads, and other scams that involve persuading the user to download a file. The advice is always to be vigilant:
- Never click a link unless you are certain where it leads.
- Never download software unless you are certain the site you are downloading it from is legitimate.
- Don’t respond to pop-ups telling you that software needs to be updated or that your Mac is infected.
- Don’t ignore warnings from macOS telling you that something you are trying to install is from an unidentified developer.
How to check whether your Mac has been infected with malware like Raccoon infostealer
If you suspect any form of malware, including the Raccoon infostealer, it’s essential to scan your Macbook as quickly as possible. For a job like this, you need a no-nonsense tool that is going to swiftly attack the problem. That tool is CleanMyMac, powered by Moonlock Engine.
Because CleanMyMac draws its malware and virus data from a frequently updated database, it can recognize malware regardless of how new or old the threat is. It will target all corners of your Macbook and destroy all threats. To prove it, we offer a no-obligation free trial so you can try it out for yourself.
Here are the steps to permanently bid farewell to Raccoon:
- Sign up for 7 free days with CleanMyMac
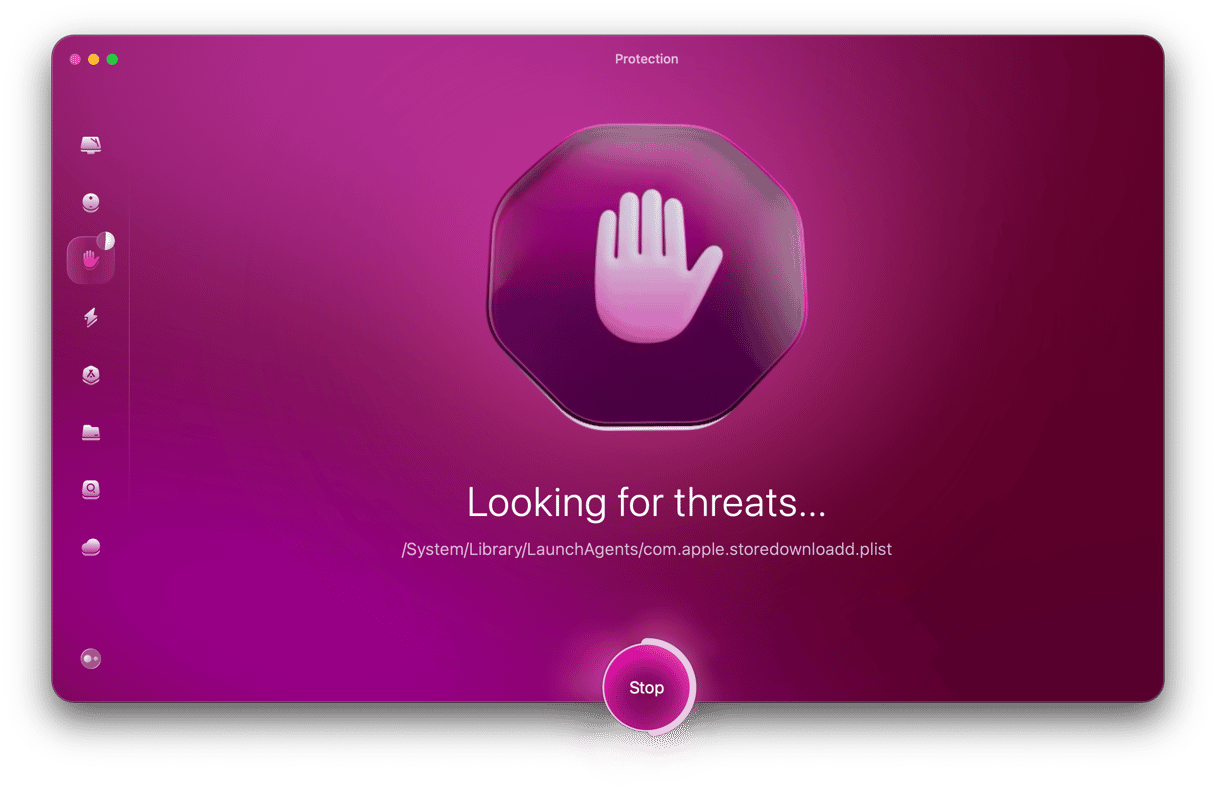
- Open CleanMyMac and click the Protection feature on the left.
- Before starting the malware removal process, you need to make sure you’re taking full advantage of everything CleanMyMac offers. Click Configure Scan and select all of the scan settings.
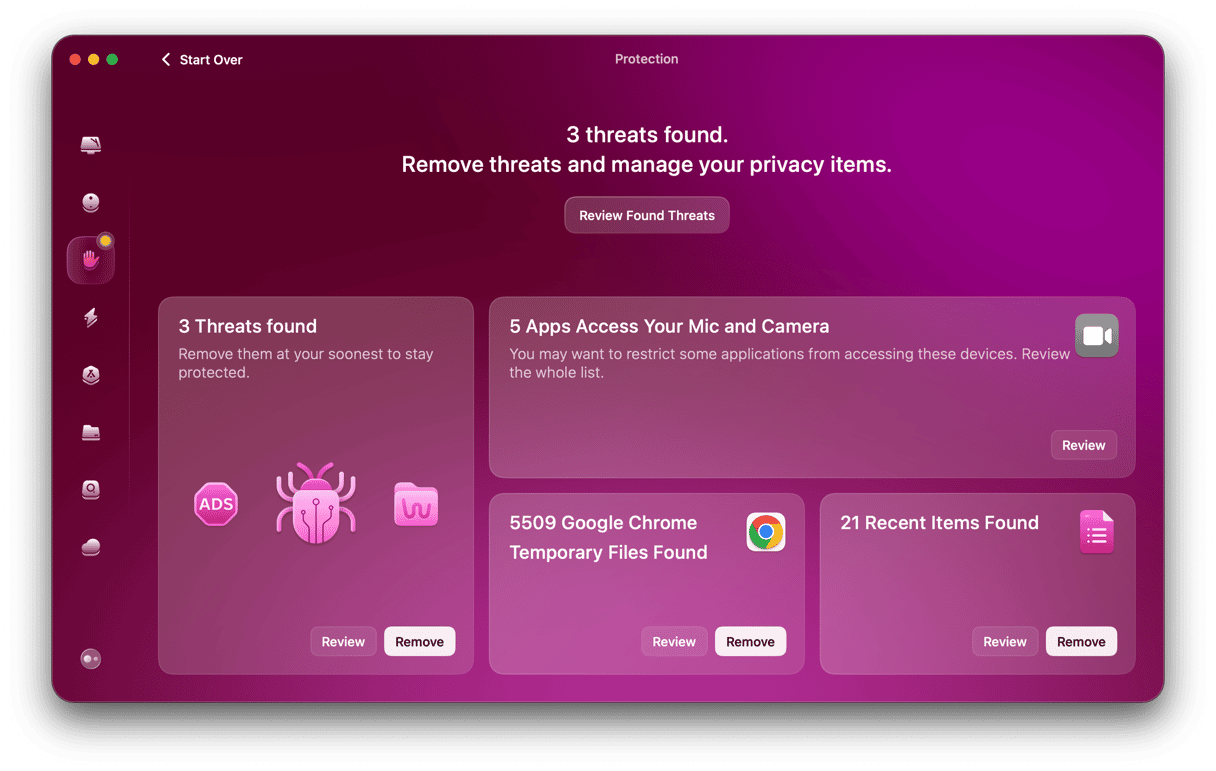
- Exit Configure Scan. It’s now time to start scanning for gremlins. Click the Scan button to unleash CleanMyMac to do its job. It will thoroughly scan all areas of your Macbook and find anything identified as a malware threat — including Raccoon Stealer.
- When infected files have been found, CleanMyMac will give you a list of them all. Select them and click Remove to clean your machine.
As a final measure to ensure a thorough job, it’s a good idea to take advantage of CleanMyMac’s Cleanup module. This will sweep up and remove all junk files that are clogging up your Mac. Some of them could be linked to Raccoon, so removing them will guarantee that the last remnants of the Raccoon stealer are gone forever.
Raccoon infostealer is a nasty piece of malware that is sold on the dark web on a subscription basis. Once deployed and installed on a target PC, it can steal sensitive data like browser autofill passwords, history, and cookies, credit cards, usernames, passwords, and cryptocurrency wallets. It is also able to hack cache files from some password managers.
Raccoon itself isn’t targeted at Macs, but there are infostealers, including Atomic, that are. So, you should be careful about which links you click and what software you download onto your Mac, as always. If you’re worried about malware on your Mac, you can use CleanMyMac to scan it and remove any malware it finds.