In May 2017, blog posts and tweets started appearing from people who had been hit by what they called a Google Docs virus. The virus pretended to be a shared Google doc and was apparently a typical phishing scam. But all was not as it seemed. The apparent malware had — or was claimed to have — very different intentions from most malware. Read on to find out everything you need to know about the virus that hit Mountain View’s favorite online office suite.
What is the Google Docs virus?
The Google Docs email virus first appeared in May 2017 when several Twitter (now X) users shared that they had been caught in what looked like a scam involving the well-known and widely-used office tool. Each report said that the user had received an email that appeared to come from someone they knew, claiming that a Google Doc had been shared with them. The email contained a button to allow the recipient to view the Google Doc. When they clicked the link, they were redirected to a non-Google web address, and everyone in their Google address book was spammed with the same email.
Within a few hours of the virus gaining wide public attention, Google posted on its official G Suite blog and said that the problem, which affected G Drive, should be resolved.
Was the virus a scam?
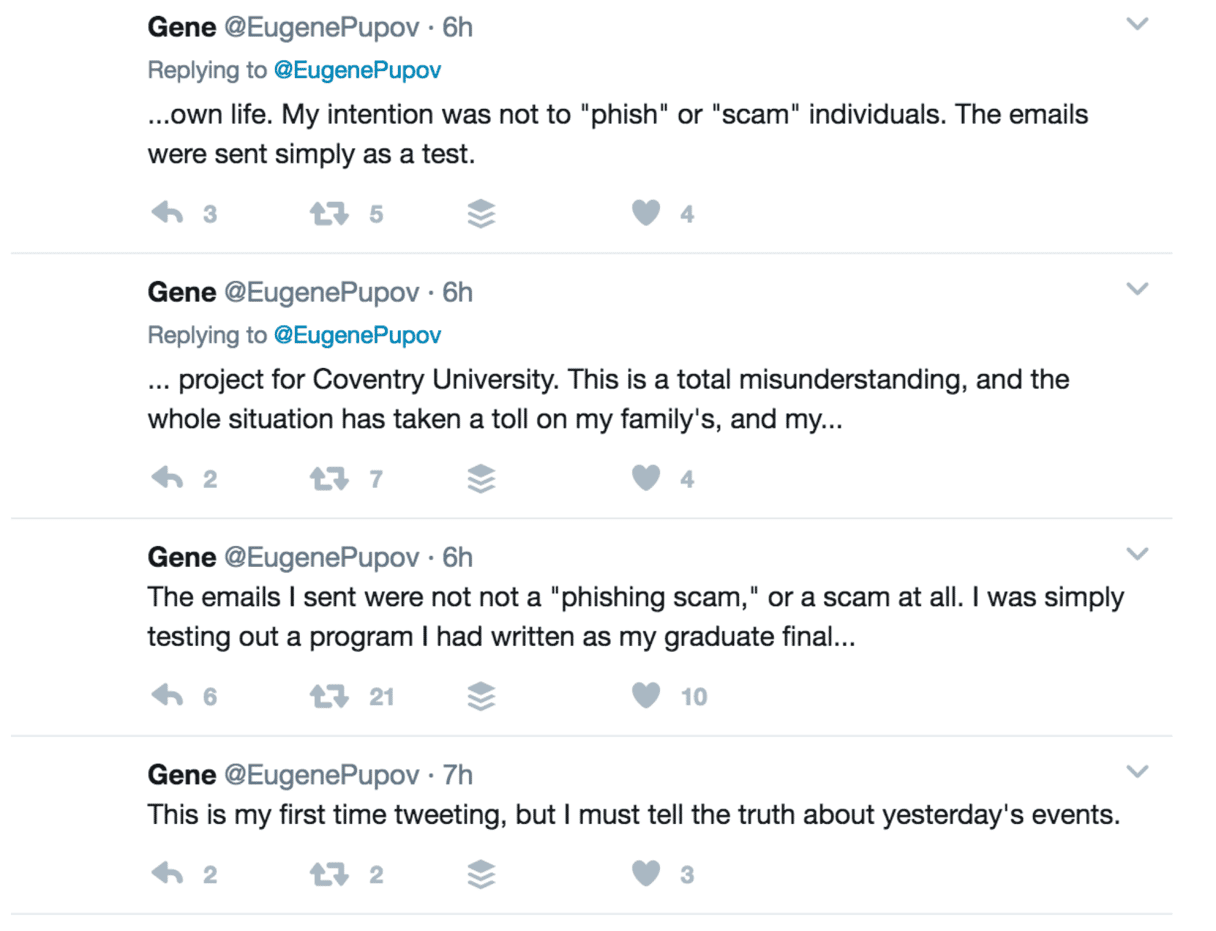
One of the most intriguing aspects of this phishing attack is that it was later claimed to have been an academic experiment that had gone wrong. A student at Coventry University in the UK claimed to have written the code as a test as part of his final year project. The student called himself Eugene Pupov, and that was indeed the name used to sign the code. However, the name was made public before the Twitter account that claimed responsibility was created, so no one was sure whether the claim was true or not.
How did it work?
This particular scam took advantage of a system known as 0Auth, which allows you to stay logged into an online account across multiple browser windows and browser sessions. The hacker used that authentication to trick Google into giving his code permission to read emails and access the address book of anyone who clicked on the link.
What should I do to protect my Mac?
Google said that it has now taken steps to close the vulnerability exploited by this virus and protect users against emails impersonating Google Docs, so you shouldn’t be affected in the future. However, that doesn’t mean that hackers won’t find other ways to exploit Google Docs or other online systems in the future. The key, as always, is to remain vigilant.
- Don’t click on links or buttons in email messages unless you are certain where they lead, even if the message seems to come from someone you know.
- Log out of online accounts if you don’t use them regularly.
- Report anything you suspect to be phishing to whoever the link is impersonating or in Gmail if the email comes through a Google account.
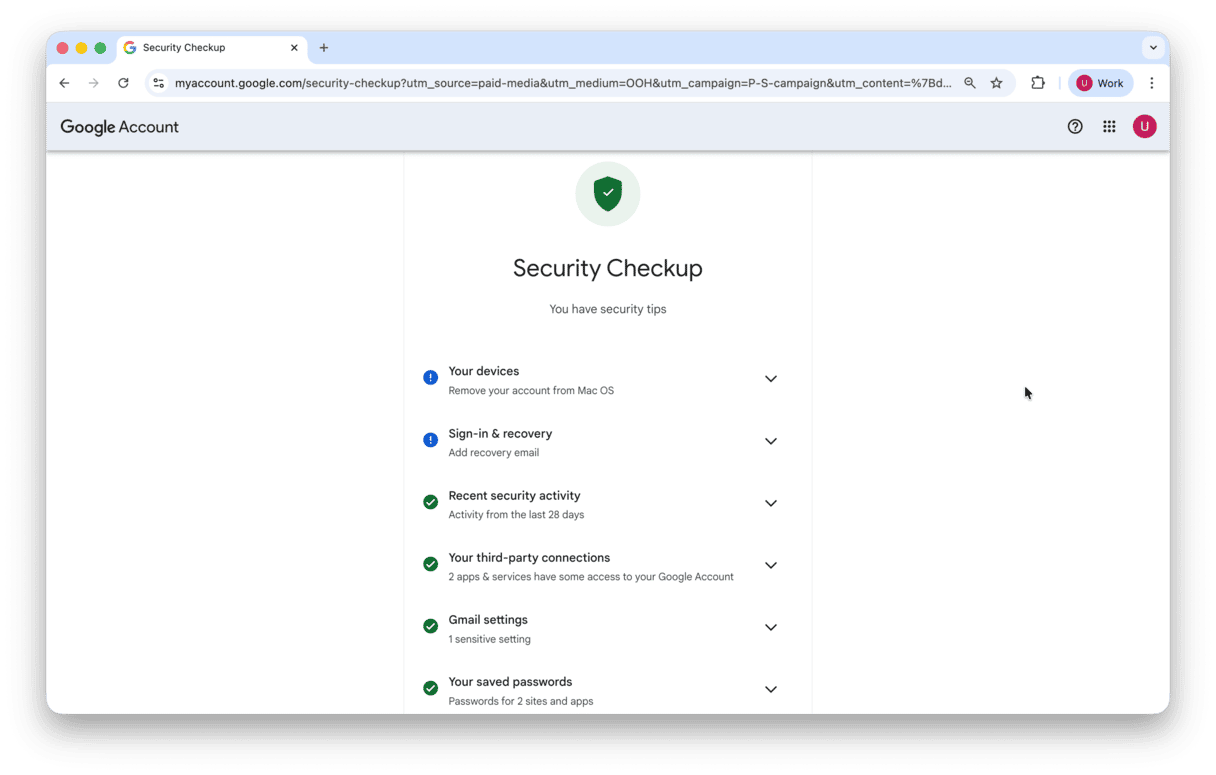
- Use Google’s security check-up tool (g.co/SecurityCheckup).
In addition to all of the steps above, you should scan your Mac for malware regularly. There are several malware cleaning tools available for the Mac, but the one I use and recommend is CleanMyMac. This particular software is notarized by Apple — not to be confused with some other fake “system keepers” or cleaners.
In addition to scanning your Mac for malware and removing it, this app notarized by Apple provides real-time protection against threats and has tools to clean up browser files and email attachments.
Here’s how to use it to scan your Mac for malware:
- Open CleanMyMac — get your free trial here.
- Choose Protection in the sidebar and run a scan.
- If CleanMyMac finds any malware, it will tell you and offer to remove it. If that happens, click Remove.
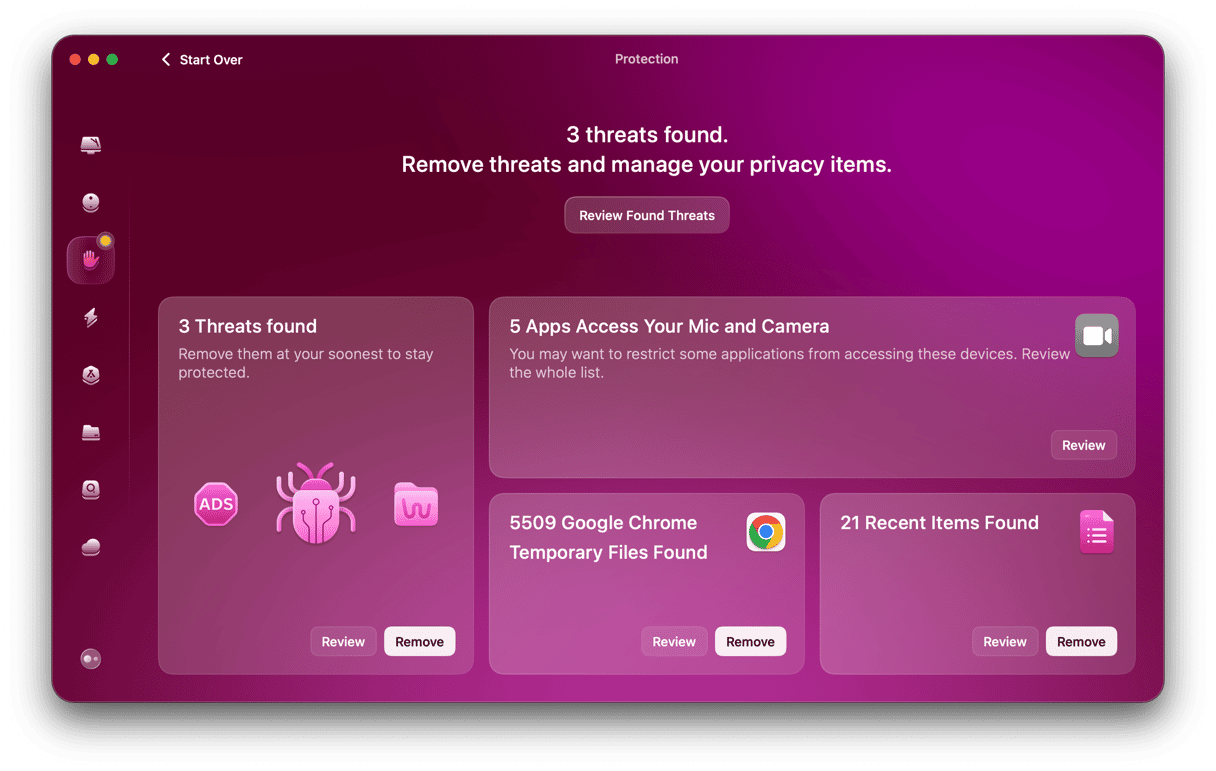
Note: You can use other tools within the Protection feature to enhance your privacy: remove browser data, get rid of recent items lists, and revoke excessive app permissions. Check those all out!
The original Google Docs virus was short-lived. And it doesn’t seem to have been malicious. However, it’s entirely possible that another similar virus could appear at any time, and that could be more dangerous. So, it’s important to be vigilant. Any email that contains a button to take you to a shared doc could be malicious, even if the email itself seems to come from someone you know. You should check with them first — before you click on the link. You should also use a tool that can detect Mac-specific threats (like CleanMyMac) to regularly scan your Mac and keep it protected.