Popular Mac viruses, malware and security flaws
In this article, we will look at the most common Mac viruses and security flaws. I'm about to show you how to detect, remove and prevent your Mac from getting them.
The more macOS popularity grows, the more lucrative it becomes to hackers. Consequently, your Mac is vulnerable to attacks like never before. Viruses on Mac are more common than you might think, so we're going to go through known Mac viruses, malware, and security flaws. What's more, I'll demonstrate how you can keep your computer safe using a cool app like CleanMyMac X.
Before we continue it's important to mention that a virus is a type of malware, capable of copying itself and spreading across systems. Malware, on the other hand, is a blanket term for a wide range of malicious software like adware, spyware, ransomware, and Trojans. So all viruses are malware, but not all malware are viruses.
Okay, let’s dig in.

How a Mac virus infects your system
How does a Mac virus find its way into your system in the first place? Typically with a helping hand from you. Apple viruses require certain actions from you: downloading a program, clicking a link, or installing an app and plugin.
The most common ways for malware to infiltrate your computer are through third-party browser plugins like Adobe Reader, Java, and Flash, or by using a Trojan horse or phishing scam — an app or email that appears to be from a legitimate source, but is in fact fraudulent.
The moment you click on a link and enter details or download the seemingly genuine app, you give the green light to the virus. And the best way to avoid that is to be vigilant. Double-check every email and everything else you want to download to your computer. If something seems off, there’s every chance that it is.
Sometimes though, being attentive won't protect you. But knowing the most well-known viruses might. Keep reading to learn more about it.
Common Mac viruses
1. Microsoft Word macro viruses
What? Microsoft programs can infect my Mac?... Unfortunately, yes.
Macros are commonly used by Word users to automate repetitive tasks which makes them a target for malware. Macro support on Mac was removed by Apple with the release of Office for Mac back in 2008 but was reintroduced in 2011. That means files opened with macros could run a Python code to log keystrokes and take screenshots of personal data.
In 2017, Malwarebytes discovered malware in a Word document about Donald Trump that caused Mac users to worry. However, the chances of being infected rely on you opening specific files. But keep calm, Apple displays a warning message every time a file contains macros. That should be enough to keep you safe from Word macro viruses.
2. Safari-get
Safari-get is a denial-of-service (DoS) attack that began targeting Mac in 2016. The malware is hidden in a seemingly genuine tech support email containing a corrupt link — you click on the link, the malware automatically inhabits your computer.
What happens then depends on whether you’re running macOS 10 or 11. The first case scenario: it takes control over your mail application creating multiple draft emails. The second one, the virus keeps opening iTunes multiple times. The end goal is to overload system memory forcing you to call a fake Apple tech support and hand over your personal or credit card information.
MacOS High Sierra versions 10.12.2 and above include a patch to deal with such vulnerability, so updating your machine should keep you safe.
3. OSX/Pirrit
OSX/Pirrit is a virus that is able to gain permission to create a new account and download software that you neither want nor need. The virus was found by Cybereason to be hidden in cracked versions of Adobe Photoshop and Microsoft Office that are popular on torrent sites.
Just a reminder, if you needed one: never ever download pirated software!
Common Mac malware
1. OSX/MaMi
OSX/MaMi is the first macOS malware that was identified in 2018. It targets Mac users employing social engineering methods such as malicious emails and website pop-ups. Once it's in your system, the malware changes DNS server settings that allow attackers to route traffic through malicious servers. That's how they gain your sensitive data.
MaMi is also capable of taking screenshots, downloading and uploading files, executing commands, and generating mouse events. The Hacker News provides instructions on how to identify the virus in your system:
“To check if your Mac computer is infected with MaMi malware, go to the Terminal via the System Preferences app and check for your DNS settings—particularly look for 82.163.143.135 and 82.163.142.137.”
2. OSX/Dok
This piece of Malware is dangerous since it's signed with an Apple-authenticated developer certificate. That allows it to bypass Mac’s Gatekeeper security feature and XProtect. Like OSX/MaMi, OSX/Dok intercepts all traffic (including traffic on SSL-TLS encrypted websites) shifting between your computer and the internet to steal private information.
Since April 2017, Apple has revoked the developer certificate and updated XProtect. However, it remains one to watch out for.
3. Fruitfly
Fruitfly malware has stolen millions of user images, personal data, tax records, and “embarrassing communications" by capturing screenshots and webcam images. The preventive solution has not been found yet since the nature of it remains unknown. So while Apple has been working on finding a way to detect and remove it, the newer and more sophisticated versions might still exist in the wild.
4. MacDownloader
While its name suggests it could be a useful app, MacDownloader is a very nasty piece of malware programmed to attack the US defense industry. It’s hidden inside a fake Adobe Flash update and shows a pop-up claiming your system is infected with adware. By clicking on the alert and entering your admin password, MacDownloader obtains sensitive data and sends it to a remote server.
MacDownloader is designed to attack a particular audience, but it’s worth checking for updates on Adobe’s official website before installing any new version of Flash.
5. KeRanger
KeRanger is macOS’s first introduction to ransomware — malware that encrypts system files and demands a ransom to decrypt them. It was bundled with the torrent client Transmission version 2.90 and installed using a valid Mac app certificate to cheat Apple security. Once documents and data files are encrypted, KeRanger demands payment in bitcoin for the malware to be removed.
Transmission has released an update to remove the malware and Apple has removed KeRanger’s GateKeeper signature to protect users. If you’re using Transmission 2.90, head over to the Transmission website to download the latest update.
Known Mac security flaws
1. Goto fail bug
The Goto fail bug was a bit of an embarrassment for Apple because this security flaw was a result of its own doing. A bug in Apple’s SSL (Secure Sockets Layer) encryption meant that a Goto command was left unclosed in the code, thus preventing SSL from doing its job to protect users.
Such glitch put communications sent over unsecured Wi-Fi (the hotspots you use at the mall and in coffee shops) at risk, allowing hackers to abduct almost anything they want. Apple managed to fix the issue on macOS, but it certainly makes you think twice about how you browse the web in public places.
2. Meltdown and Spectre
In January 2018, it was announced that there was a flaw in Intel chips used in Macs, giving rise to the dastardly duo of Meltdown and Spectre.

Message from Apple:
The Meltdown and Spectre issues take advantage of a modern CPU performance feature called speculative execution. Speculative execution improves speed by operating on multiple instructions at once—possibly in a different order than when they entered the CPU. To increase performance, the CPU predicts which path of a branch is most likely to be taken, and will speculatively continue execution down that path even before the branch is completed. If the prediction was wrong, this speculative execution is rolled back in a way that is intended to be invisible to software.
The Meltdown and Spectre exploitation techniques abuse speculative execution to access privileged memory—including that of the kernel—from a less-privileged user process such as a malicious app running on a device.
Meltdown and Spectre affect all Mac systems, but Apple insists there are no known exploits currently impacting customers. macOS 10.13.2 and above includes a patch to protect against both flaws.
3. High Sierra “root” bug
As far as security flaws go, High Sierra’s “root” bug is a pretty big one. It was discovered by software developer Lemi Orhan Ergin. The bug allows anyone to gain root access to a system by leaving the password field blank. So, anyone with physical, remote desktop, or screen-sharing access to your system can type in “root” and hit enter. Done, they're in! Scary, right?
Apple has recently released an official bug fix, but it’s worth thinking twice before sharing access privileges on your Mac.

How to recognize a virus on Mac
Curious about how you can spot a virus on your Mac? In the case of ransomware like KeRanger or a DoS attack like Safari-get, the issue is more obvious. With other malware, however, the infection is much harder to track.
A few of the tell-tale signs include:
- Unexpected system reboots
- Apps closing and restarting for no reason
- Browsers automatically install suspicious updates
- Web pages obscured with ads
- Drop in system performance

How to stay away from viruses on Mac
Below is the list of practical steps that you can do to safeguard your system:
- Always check the source of an email by looking at the address of the sender
- Avoid pirated software
- Avoid software and media downloads from torrent clients
- Avoid apps or pop-ups that ask you to “fix” an infected Mac
- Never download codecs or plug-ins from unknown websites
If you suspect a Mac virus has infected your system, it’s important to address the problem immediately. There are two ways that you can do this: manually or with my personal favorite app, CleanMyMac X.
How to remove a virus on Mac manually
To remove a virus manually, the first thing to do is find out what’s causing the problem. If it's a downloaded file, go to the Downloads folder and search for .DMG files. If the file is unfamiliar, delete it and empty the Trash afterward.
If an app is an issue, go to your Applications, drag the icon to the Trash bin and empty the Trash immediately.
Both of these methods offer just a quick fix. In order to remove infection completely from your system, you'll have to use extra tools.
How to remove malware on Mac with CleanMyMac X
CleanMyMac X is designed to detect and remove malware threats from your Mac, including adware, spyware, ransomware, worms, and more. Here's how it works:
- Download CleanMyMac X (free download) and launch the app.
- Click on the Malware Removal tab.
- Click Scan.
- Then click Remove.
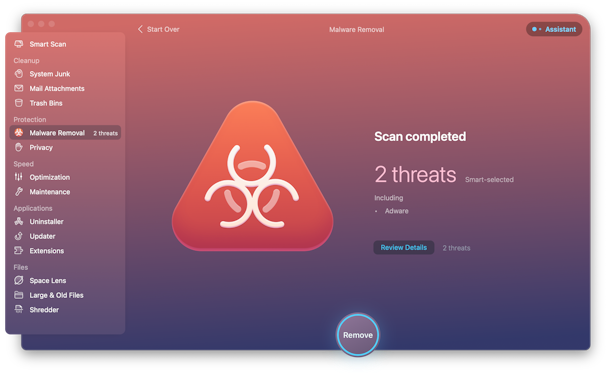
This app is notarized by Apple so you are safe using it. It also has a real-time monitor that sends you an instant notification when an unknown app tries to penetrate your system.
Keep your Mac virus-free
For the most part, using a Mac is a pleasant, malware-free experience, but no computer is ever 100% virus-free. Keeping in mind the most common Mac viruses can actually help keep your system secure. And if a rogue app does make its way on your system, keep CleanMyMac X handy to remove it once and for all.





