If you have even the vaguest interest in computer security, you’ve probably heard the term ‘backdoor’ used a great deal. But what is a backdoor, what kind of risk does it present, and what can you do to protect your Mac? Read on to find out.
What is a backdoor?
In computer security terms, a backdoor is anything that allows the usual authentication process for a computer or other device to be bypassed. It could be deliberately installed by the original programmer — if you’ve seen the 1983 movie Wargames, you’ll remember that Dr. Falken installed a backdoor in the supercomputer system he designed, and it was used by Matthew Broderick’s character to play what he thought was a video game, with almost drastic consequences. Other backdoors are a result of poor security protocols, such as default usernames and passwords that allow access to the whole system. And the third group of backdoors is created by hackers inserting code into a system.

What damage can a backdoor do?
The short answer is lots. A backdoor gives anyone, including a malicious hacker, access to your Mac. They could use that to illegally use resources for a nefarious distributed computing project like crypto mining or steal personal data, such as email addresses or even bank and other financial details.
Backdoors can also be used by the authorities to access personal details and messages. This type of backdoor has been in the news a great deal recently due to tech companies refusing to, or being unable to, give access to devices and accounts to law enforcement agencies. Some believe that these companies should build backdoors into their networks and devices to allow law enforcement to access data. Others point out that any backdoor is a security risk, and so allowing law enforcement to use one would put it at risk from hackers.
Notable examples of backdoor attacks
There are 2 prime examples of backdoor attacks that illustrate their danger and the potential to cause long-term damage.
SolarWinds
In 2020, hackers attacked the software company SolarWinds and inserted malicious code into the company’s Orion software platform. The hackers were suspected to be tied to the Russian government, and the fact that SolarWinds provided network management software to the US government made the attack a national security incident.
The code compromised all company software updates and affected the networks of any clients who installed the update. Remarkably, the backdoor attack went undetected for months, and the hackers were able to gather huge amounts of valuable data from SolarWinds and their clients.
Microsoft Exchange Server
In 2021, cybercriminals discovered a series of undiscovered vulnerabilities inside Microsoft Exchange Server, otherwise known as “zero-day exploits.” This allowed the attackers to get into email accounts, install malware, steal data, and, more importantly, install backdoor code into the software.
Microsoft’s substantial user base made the attack catastrophic. Tens of thousands of customers were involved worldwide, including government agencies.
Useful tips to prevent backdoor attacks on your Mac
How to protect your Mac from backdoor vulnerabilities will depend on the nature of the backdoor. Is this something that was installed by the actual creator? Or is it a security vulnerability?
A lot of the time, backdoors are undetectable and only present a problem when a hacker who knows the backdoor is there takes advantage of it. Until the hidden access point becomes known, the problem lies dormant.
The other difficulty is that in most backdoor cases, there is nothing you can do to immediately solve the problem. Running an antivirus scan will not make the backdoor go away.
If it’s a software backdoor, the developer has to bring out a patch to plug the hole. If it's a hardware issue, the manufacturer has to provide a firmware update. Until then, you either need to keep the software/hardware closed and unused or uninstall/get rid of it completely.
Although many backdoor vulnerabilities are outside your control until updates are provided, there are some things you can do to mitigate the risk.
Disconnect your device from the internet
When you don’t need a Wi-Fi connection, disconnect from the internet. A backdoor vulnerability can’t be exploited if hackers have no way to access your network.
On a related note, never use public Wi-Fi networks, as they are notoriously insecure and misconfigured. If you must absolutely use one, enable a VPN (see the next section).
Use a VPN
If the internet must be on, use a VPN such as ClearVPN to encrypt your web traffic. This is particularly good if the backdoor vulnerability is coming from your Wi-Fi router.
Make sure all device updates are installed
Cyber attackers take advantage of any and all security gaps they can find. Therefore, make a point to constantly check for macOS updates and app updates that will patch vulnerabilities.
Only download software and hardware from trusted sources
Whether or not there’s a backdoor will depend on where you got the software or hardware from. If you stick to reputable sources like the Apple App Store or a trusted developer like MacPaw, you will be safe. With hardware, go with the big names.
If you download and install software — or buy hardware — from lesser-known sources, your chances of a backdoor attack increase. Be very circumspect about your sources.
Be extremely cautious about email links and attachments
Sometimes, a backdoor is activated by another piece of malware, and this could come in the form of an infected email attachment or infected web link.
If you get an email from someone you don’t know (or don’t entirely trust), don’t open any attachments or click any links.
Enable the Mac Firewall
As we said, an attacker can only take advantage of a backdoor if they’re able to access your machine online. Enabling tools like the Mac Firewall will severely hinder them.
It’s very easy to enable the Mac Firewall. Just go to System Settings > Network > Firewall. Toggle it on.
Monitor your system activity with Activity Monitor
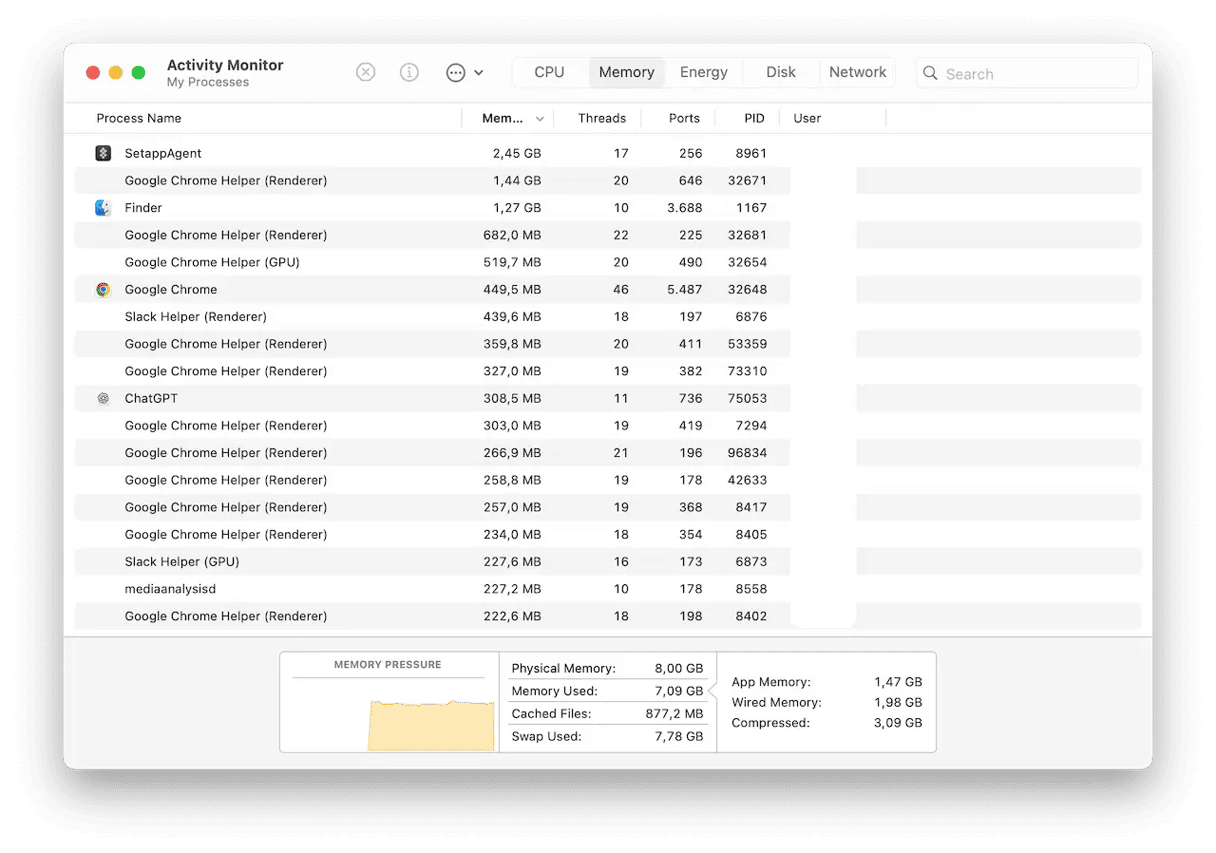
When a malware attack takes advantage of a backdoor, it uses a considerable amount of CPU and memory. This slows your computer down to a crawl. Always keep an eye on your running processes and force-quit any that you don’t recognize.
Use a top-notch antivirus platform
It may not be able to detect backdoors, but an antivirus program will detect malware attacks exploiting that backdoor, as well as other new malware being introduced to the target device.
Our recommendation is CleanMyMac powered by Moonlock Engine. Select the Performance module, select Deep Scan, and let it go on the malware hunt. You can also enable continual monitoring for instant malware alerts.

Other steps you can take to protect your Mac are:
- Use Activity Monitor (Applications > Utilities) to monitor network traffic and look for any unusual spikes at times when you haven’t been active online.
- Consider using the Little Snitch app to monitor which applications and processes are ‘phoning home’ and when.
- Scan your Mac for malware regularly. You can do this using the CleanMyMac (get a free trial). It uses CleanMyMac’s regularly-updated malware database and compares what it finds on your Mac with that. If it finds any malware, including that which may have installed a backdoor, it will offer to remove it. Besides, it comes with real-time and background monitoring tools that may prevent the installation of backdoor malware on your Mac.
- Make sure your Mac’s built-in firewall is switched on and your router is set up to prevent access to your network from the outside world.
- Watch out for apps that request access to your microphone or webcam when you don’t expect them to. And be cautious when your webcam turns on when you’re not using it.
- Use password managers to generate more secure and complex passwords. Developing this habit may help make getting into your network more difficult. If hackers have already succeeded in infiltrating your system, spreading the malicious code over it would be slower.
Backdoors are difficult to guard against because you won’t necessarily know they are there until they are either discovered or used to steal data or for some other purpose. However, there are a number of steps you can take to mitigate the risk they present. And for backdoors that are downloaded to your computer using an email phishing scam or a ‘drive-by’ download, such as those that pretend to be an important software update, common sense and vigilance will help protect you. If you do think you’ve downloaded malware like a backdoor, you can use CleanMyMac to scan your Mac and remove it.