Adware is a type of malware that, once your Mac or PC is infected, displays adverts for software and services that are, at best, highly questionable on websites you visit or directly as pop-up windows on your computer. CrossRider is a type of adware that comes in many different guises.
What is the new CrossRider variant?
Discovered in 2018, this new CrossRider variant is similar to other versions of CrossRider in that it is bundled with potentially unwanted programs (PUPs), such as Advanced Mac Cleaner, and masquerades as an apparently legitimate download. In this case, the download is a fake Adobe Flash updater, and the process involves a user arriving at a website that tells them they need to update Adobe Flash and supplying a link. If the user clicks the link, it downloads the fake Flash updater and installs the adware.
The new CrossRider variant also installs a profile in System Preferences called AdminPrefs. This profile, which has also been seen in browser hijackers like Any Search, forces Safari and Chrome to redirect their homepage to chumsearch.com. The profile also makes it impossible to change the homepage settings in both browsers without first removing the profile.

How to tell if CrossRider has infected your Mac
The most noticeable change will be what you see as soon as you launch Safari or Chrome since your homepage will have changed from whatever you had it set at to chumsearch.com.
There’s no evidence that CrossRider will do any damage to your Mac. However, by redirecting your homepage, it allows hackers to gather information about the sites you visit and what you do on those sites. It also allows it to display adverts and otherwise make your browsing experience much less enjoyable. It could also slow down your Mac by consuming resources, such as RAM, to display ads or for other purposes.
The latest CrossRider variant uses a fake Adobe Flash Updater to install itself on your Mac. To avoid it and other malware, you should never click on a link in any window that tells you that you need to update Flash. Here's how it tries to sneak onto your Mac:

If you still have Flash installed on your Mac and want to keep it, click on the Flash Player pane in System Preferences, and choose the Update tab. If you haven’t got it set to “Allow Adobe to Install Updates,” choose “Check for Updates.” That’s the only method you should use for updating Flash. If you don’t use it or don’t know if you use it, uninstall it.
How does CrossRider malware impact users?
The CrossRider malware may not sound so bad at first, but it can cause some serious real-world problems:
- Browser changes — CrossRider will change your homepage and default search engine. It can also downgrade your security settings and redirect your website visits to other sites, especially search queries.
- Intrusive pop-up ads — CrossRider can bombard your browser with annoying pop-up ads, some of which may urge you to buy their product to solve a nonexistent problem.
- Data theft — The malware will collect your browsing data, such as your IP address, sites visited, search queries, and more. This information could then be sold to third-party brokers.
- Interference with your device’s performance — your browser will slow down and, in some cases, eventually crash. CrossRider will likely consume a large amount of CPU and memory, making even normal computer processes difficult. It may also block security updates from installing, in addition to interfering with antivirus programs.
- More malware — once inside a target device, the malware can begin to introduce even more malware.
- Data theft — since CrossRider redirects users to unsafe websites, victims can be tricked into entering personal information, such as their credit card details.
What are the variants of CrossRider, and how do they differ?
There have been 3 different types of CrossRider over the years, each using a different method to infiltrate computers:
- Advanced Mac Cleaner Bundle (2015) — this one has been around the longest, and online chatter seems to indicate that this variant is still affecting people today. It bundles itself with software and installs itself in the background, especially with software like Advanced Mac Cleaner. Once on a device, it tells the user that their system is experiencing stability problems and pressures them to pay for software to “fix” the mythical problem.
- Configuration Profile (2018) — disguising itself as an Adobe Flash updater, this version tricked people into believing that their version of Adobe Flash was outdated. Once the victim downloaded the fake “update,” CrossRider leaped into action by making a configuration profile on macOS devices and redirecting users to a CrossRider-owned website.
- Searchmine.net redirect (2019) — similar to the 2018 variant, Searchmine.net used the fake Adobe Flash method to get onto target computers and then redirected users’ online searches to searchmine.net. Removing this variant was extremely difficult due to the installation of a configuration profile on macOS, which locked the malware changes.

How to remove CrossRider manually
Step 1: Remove it from your Applications folder
1. Go to your Applications, locate Advanced Mac Cleaner (since CrossRider is bundled with it), and drag it to the Bin. Empty the Bin.
2. Click on the Apple menu and choose System Settings.
3. Go to General > Device Management. Click the profile that has been installed without your knowledge and click the “-” at the bottom of the box.
This will remove malicious admin profiles installed by the virus.
Step 2: Remove CrossRider from Safari
Even after you’ve trashed the Advanced Mac Cleaner app and removed the AdminProfiles malware, your Safari settings are still set to redirect your homepage to chumsearch.com. To change that, do the following:
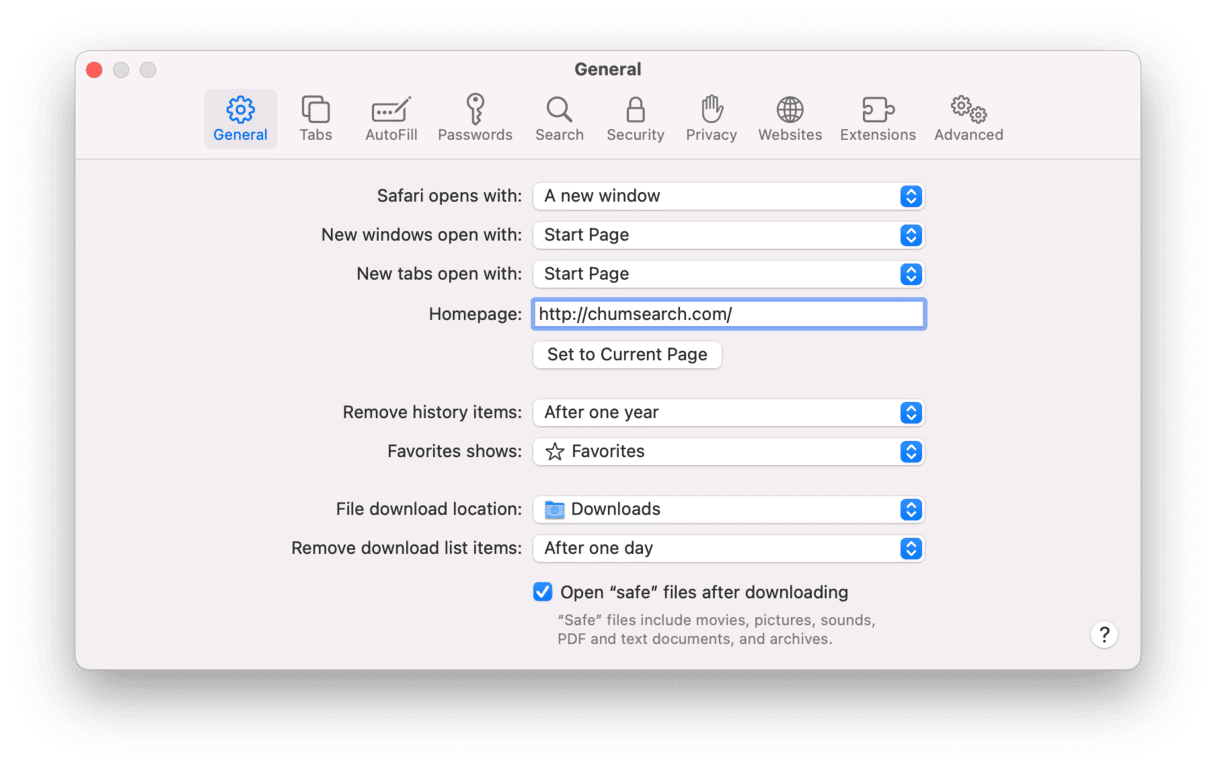
1. Launch Safari and choose Settings from the Safari menu
2. Choose the General tab, and in the Homepage text box, enter the name of the website you want to use as your browser homepage.
3. Now, go to the Search tab and change the search engine to the one you want to use as the default
Step 3: Remove CrossRider from Chrome
1. Launch Chrome.
2. Do one of the following:
a: Choose the Settings icon (three dots) on the left of the window.
b: Type “chrome://settings” into the address bar.
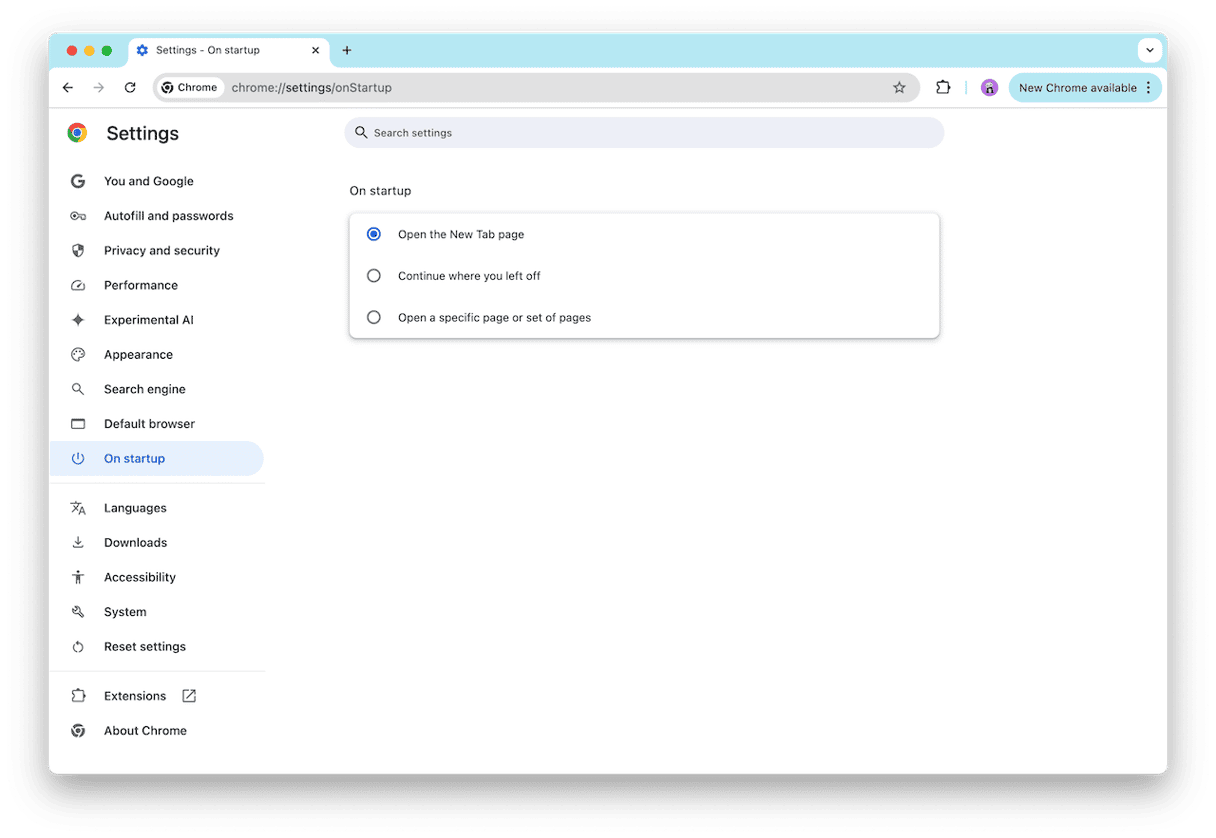
3. Choose “on startup” and check the button next to “Open a specific page or set of pages.”
4. Click the More button (three dots on top of each other).
5. Select “edit” and type the address of the homepage you want to use.
6. Click Save.
7. Go to Settings again and this time, choose “search engine.”
8. Select “manage search engines” and press the More button next to chumsearch.com, then choose “delete.”
9. Click on the dropdown menu next to “Search engine used in address bar” and pick the search engine you want to use.

How to remove Crossrider in a click
That’s quite a long process with several steps. Thankfully, there is an easier way. CleanMyMac has a malware utility that recognizes CrossRider and can remove it from your Mac at the press of a button.
CleanMyMac’s malware database is updated regularly, and so it knows about all the latest malware threats. It’s lightweight, fast, and powerful, and using it is easy. The app knows where all the different elements of each piece of malware are stored, it can remove them all in one go.
- Get your free CleanMyMac trial.
- Open the app.
- Select the Protection feature on the left.
- Go to Configure Scan first to get into the settings and choose your scan options. We recommend selecting everything — especially Deep Scan.
- Once your settings have been configured, exit Configure Scan and click the Scan button. CleanMyMac will start searching the inner depths of your Mac for any traces of CrossRider.
- When CrossRider has been found, CleanMyMac will show it to you in a list of discovered threats. Select it and click Remove.
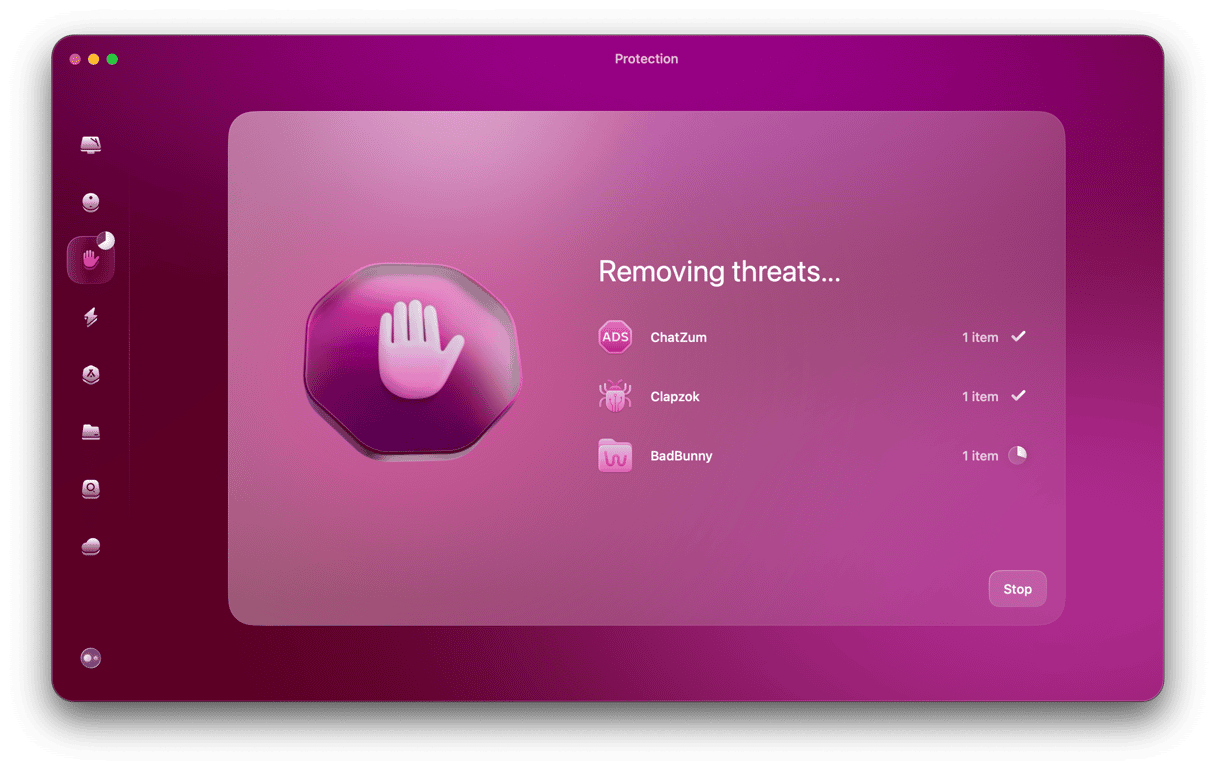
There may also be debris files left over. We recommend you now click the Optimize tool to remove them all. Some of them may be linked to CrossRider, and removing them will complete the job.
The latest CrossRider variant masquerades as an update to Adobe Flash and is bundled with an app called Advanced Mac Cleaner. It also installs a Profile in System Preferences that changes settings in Safari and Chrome in order to redirect your browser homepage.
To avoid downloading it, never update Flash from anywhere else but its own System Preferences pane. If you’ve already been infected, you can remove it manually following the steps above or using the Malware Removal utility in CleanMyMac.