Rootkits are a hazardous type of malware because they attack deep within a computer system, often at the BIOS level, and are very hard to detect. Once installed, there are several ways in which they can cause damage to you and your Mac.
However, there are anti-rootkit tools that can detect and remove them. This article will explain what a rootkit is, how you can avoid getting one on your Mac, and how to remove it.
What is a rootkit?
A rootkit is a special type of malware designed to hide its malicious processes and activity from both the operating system and the user. Whether anti-malware tools can detect it depends on the type of rootkit and how deeply it’s embedded in the system.
Most antivirus tools include Mac rootkit scanners and can usually detect rootkits operating on the surface. But once they reach the computer’s firmware, only cybersecurity experts and in-depth analysis can help uncover and remove them.
Rootkit is still very rare on macOS. However, macOS malware is evolving so quickly that understanding how rootkit attack works gives you a chance to stay ahead.
Is a rootkit considered malware, and how does it actually work?
Yes, a rootkit is a form of malware that can be quite destructive if it gets onto your device. This is because it is specifically designed to be stealthy and hide deep inside your MacBook, where it’s hard to detect.
What makes rootkit malware especially dangerous is the depth to which it burrows in and takes over your MacBook. It gets down to the kernel level of your operating system and gives itself access to your device.
Rootkits manage this by modifying your core system files, masking themselves, and making it extremely difficult for antimalware tools to find them. They then go on the hunt for your sensitive and private information by installing keyloggers, as well as copying your files and exfiltrating them through your Wi-Fi connection to their external server.
Types of rootkit
1. Hardware or firmware rootkit
These are installed in the system BIOS of a computer or the firmware of a network router. They can be used to intercept data on a disk or transmitted over a network. One example of such firmware is Thunderstrike discovered in 2014. This malware exploited the Mac’s Thunderbolt port to install code and could install malware on the ROM EFI boot chip on Macs. It was difficult to detect and, once in place, could steal data or spy on activity.

2. Bootloader
The bootloader is the part of the system that loads the operating system when a computer starts up. A bootloader replaces the actual bootloader, meaning the malware is activated before the computer has started up.
3. Kernel mode rootkit
The kernel is the core of your Mac’s operating system. Based on Unix, it’s the software that makes everything else, including macOS, possible. A Kernel rootkit attacks that software and changes it. A hacker can do pretty much anything they want, including spying on you, stealing your data, or locking you out of your Mac altogether.
How to detect rootkits on your system
Although it is extremely difficult to detect rootkits inside your operating system, it isn’t impossible. Here is a list of methods you can try:
- Use an anti-malware tool. We will be going into more depth later in the article about Moonlock, a Mac protection and antivirus app. For now, just know this should be your first port of call to remove a rootkit.
- Check Activity Monitor. Rootkits run their own scripts and programs. So, the next step is to see if there is anything running that you don’t recognize. If you see a running process you’re not sure about, run a web search for the name and see what comes up. You should also use Activity Monitor to see if any running processes are consuming an inordinate amount of CPU and memory.
- Use EtreCheck to troubleshoot macOS problems. If you have a persistent issue, try the free EtreCheck. Choose the type of problem you’re having, and it will attempt to diagnose it, including the possibility of rootkits.
- Use KnockKnock to find persistent processes. One of the rootkit symptoms that makes this malware difficult to combat is that it restarts when the MacBook restarts. The Mac rootkit scanner KnockKnock can be used to look for processes that automatically restart when the device does.

How to avoid a rootkit
There are two ways a rootkit can find its way onto your Mac: over a network like the internet or via an external peripheral. Thunderstrike used the latter mode — a device connected to the Thunderbolt port on a target Mac could exploit the firmware in the port and install malware. However, most such malware is transferred over the internet in exactly the same way as other malware. Follow these guidelines to avoid a rootkit being installed on your Mac.
- Don’t leave your Mac unattended in a public place. If you’re staying in a hotel, lock it in the safe when you’re out of the room.
- Don’t click on a link in an email or instant message unless you are 100% sure it’s safe.
- Don’t download attachments in email messages unless you know what they are.
- Don’t click on links in pop-up adverts that tell you Flash Player or any other piece of software is out of date.
- Keep your operating system up to date.
- Don’t ignore warnings from your web browser when it tells you a website you are trying to visit is unsafe.

How to remove a rootkit virus
Rootkits are notoriously tricky to detect, and it’s possible to have one on your computer and not know about it. If it doesn’t directly impact the performance of your Mac or display adware or have some other visible effect, there may be no way to spot it. It will just sit there silently, stealing your data and monitoring your activity.
There are rootkit scanner tools available for Unix that will run on macOS. However, you’ll need to be comfortable with Terminal to use one, so they are not the best choice as a rootkit removal tool for most people. Fortunately, there are other ways. Lots of these viruses are known and can be detected by anti-malware software.
Get rid of rootkit malware with a dedicated macOS antivirus tool
As we said previously, an anti-malware tool should be your first step to check your Mac for rootkits. The best one on the market that knows everything about macOS malware is Moonlock. It comes with powerful antivirus features designed to detect anything malicious coming after Mac users.
What’s even better is that new customers get a free trial to try out Moonlock before paying any money. So, if you think you have rootkit malware on your Mac, give Moonlock a try and see if it fixes the problem.
Follow these easy steps to carry out the rootkit removal process:
- Sign up for 7 free days with Moonlock.
- Once Moonlock is open, its real-time protection starts checking every file you interact with and blocks risky ones. It works on the surface level, like your downloads, and immediately neutralizes malware the moment it lands on your Mac.
With Moonlock’s real-time protection, you don’t have to drag and drop new files into a cybersecurity app. Moonlock scans everything you open, rename, or download in the background — locking rootkits, viruses, and other intruders in a digital cell.
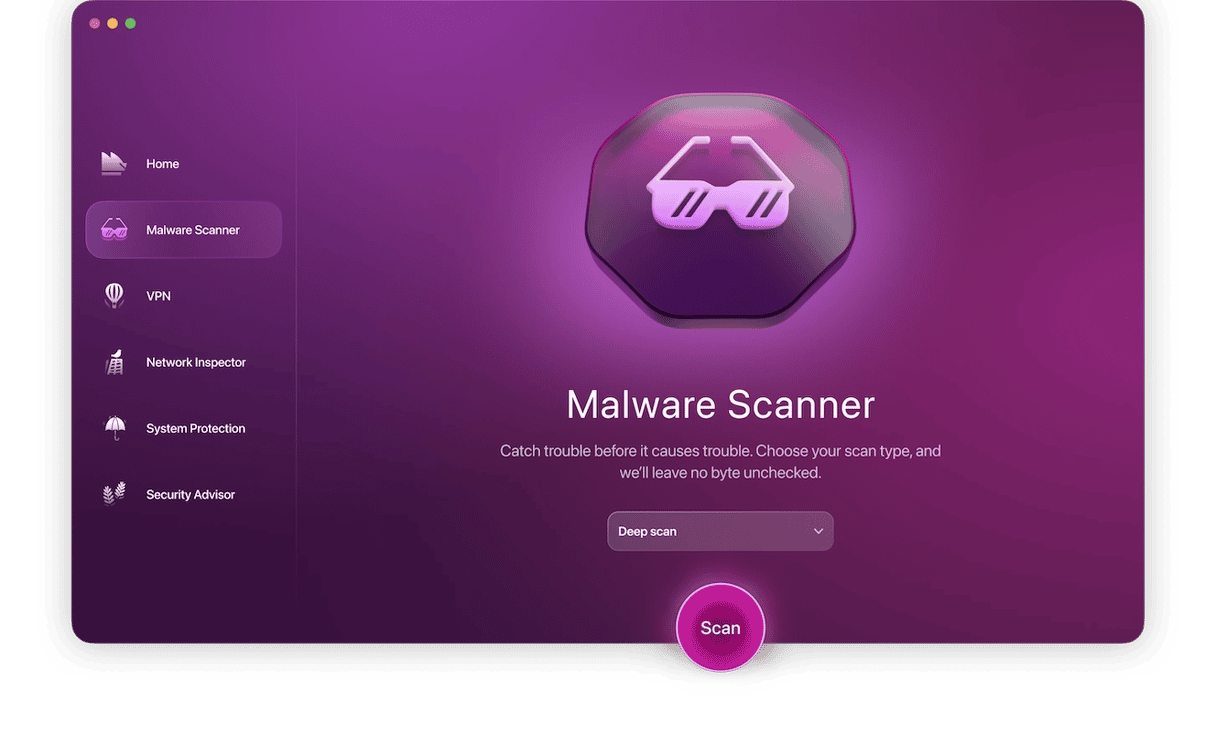
If you’re concerned about your system’s safety, run a full scan with Moonlock’s Malware Scanner. It will inspect every corner of your Mac, including long-forgotten files, and get rid of rootkits that may have been hiding there for a while. Here’s how to do it:
- Open Moonlock, then click Malware Scanner in the sidebar.
- Choose a Deep scan type. That’s the one that leaves no stone unturned on your Mac.
- Click Scan. Moonlock will start looking for anything suspicious everywhere, including external drives, Mail attachments, browser extensions, and ZIP files.
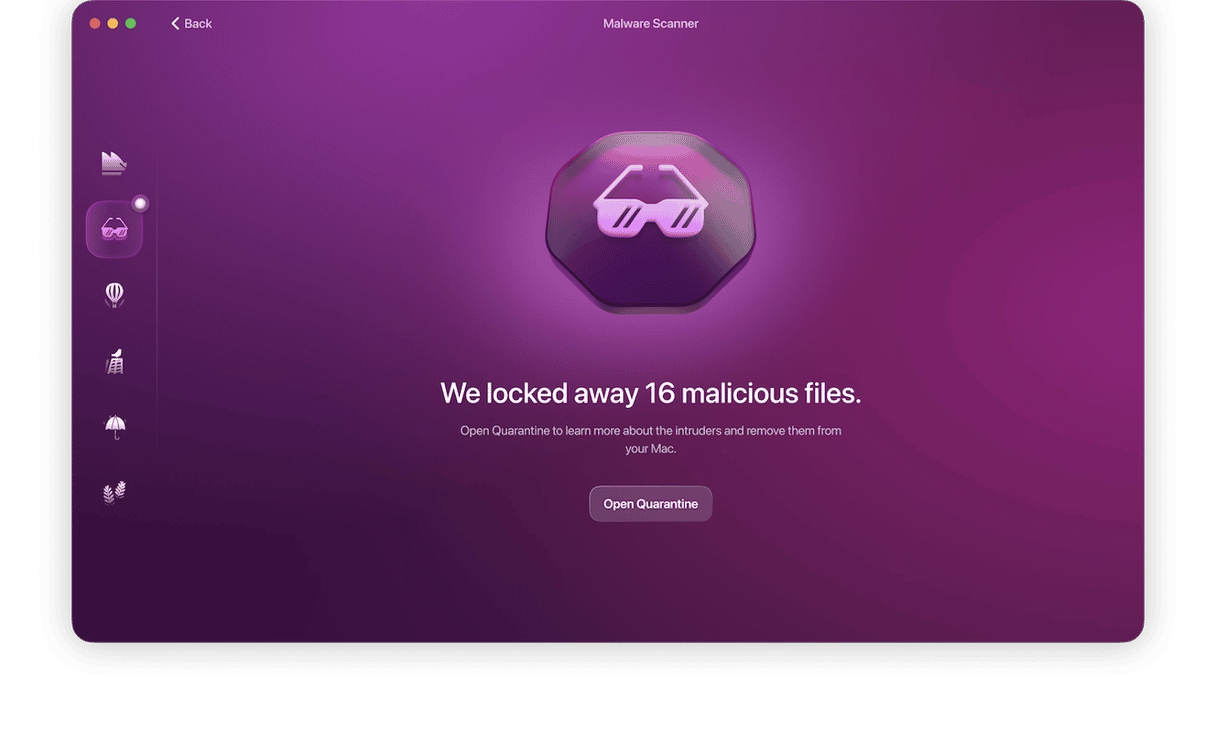
- Everything risky gets neutralized and locked in Quarantine. That’s where all malicious activity gets cut off for all malware. Review the files, select them all, and remove them. Moonlock will guide you every step of the way.
Some manual rootkit removal methods you can try
Manually removing a rootkit is no easy matter. Honestly, the best way to remove a rootkit is to use one of the methods outlined in this article. Or reset your MacBook to factory settings.
If you really want to try it the manual way, keep in mind that there is no guarantee you’ll get all traces of the rootkit. Make sure you’ve disconnected your Wi-Fi connection before doing the following.
Boot into Recovery Mode
First, reboot your computer. Once you see the Apple logo, press the key combination Command (⌘) + R to go into Recovery Mode.
Check if System Integrity Protection has been disabled
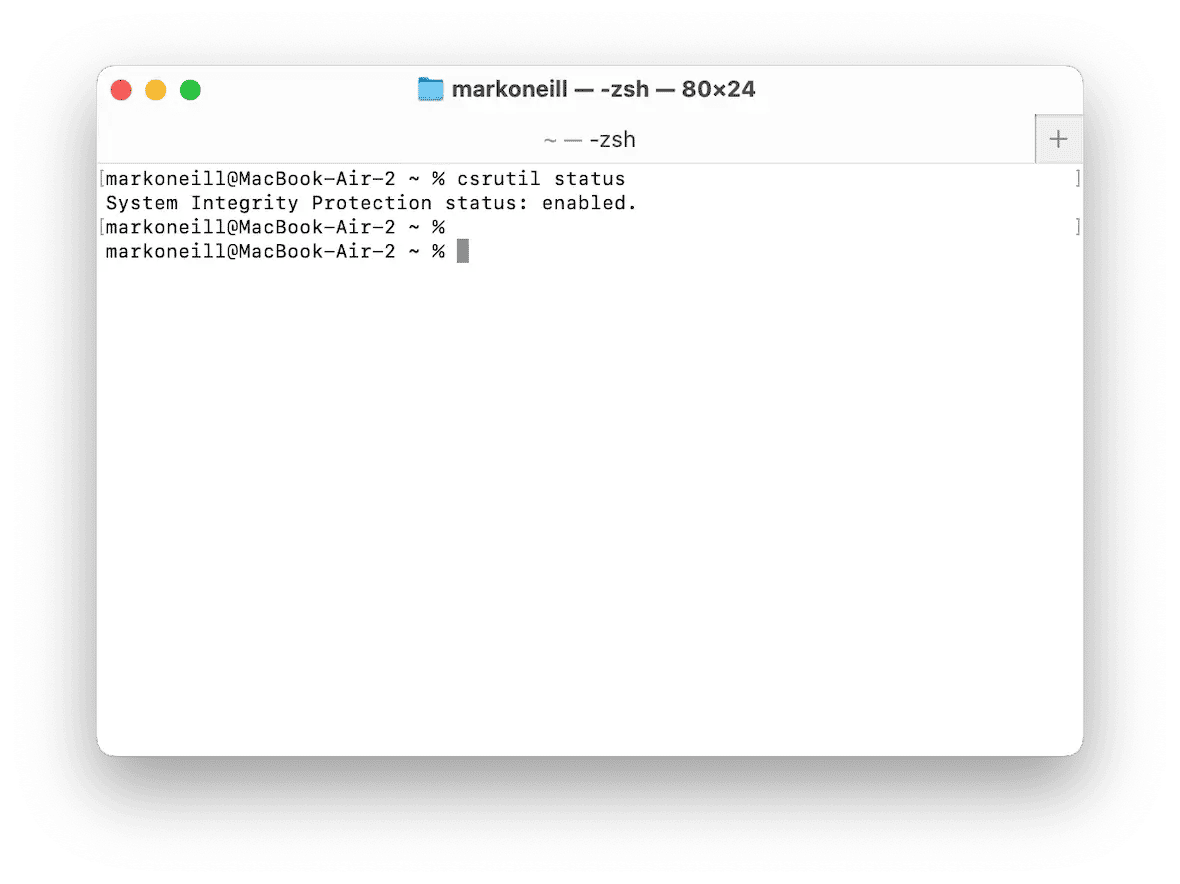
System Integrity Protection (SIP) stops any core system files from being altered. In some cases, malware can disable this feature. Your next step is to open Terminal and type the following:
csrutil status
This will tell you if SIP has been disabled. If it has, you can turn it back on by typing the following into Terminal (note: this must be done in macOS Recovery Mode), then restarting your Mac:
csrutil enable
Check for suspicious kernels
Since a rootkit is able to get down to the kernel level, it’s now time to check for any suspicious kernel extensions (KEXTs). In Terminal, type the following:
kextstat | grep -v com.apple
This is where you need some advanced knowledge to recognize a suspicious kernel when you look at it. On newer macOS versions (Big Sur and later), this command may return no results even if third-party system extensions are present, because traditional KEXTs have been largely replaced by System Extensions and DriverKit.
If you are convinced that a kernel has been compromised, you can remove it by typing the following into Terminal.
sudo kextunload /Library/Extensions/BadExtension.kext
sudo rm -rf /Library/Extensions/BadExtension.kext
Now, reboot your Mac.
Important: These commands will only work if System Integrity Protection is disabled or partially disabled. Additionally, make sure you are removing the correct extension — deleting critical files can destabilize your system.
How to avoid rootkits and other hidden malware
Just like other malware, rootkits sneak onto your Mac through cracked software, scam messages with malicious links, or bad actors purposefully installing it while you were not looking. These simple steps can help you avoid situations where you’ll need a rootkit remover:
Don’t install cracked software
Cracked apps might seem to work fine, but they often come bundled with hidden malware. It disguises itself among files of the software you wanted and may not show signs right away. If you think you’ll spot it and delete it in time, better reconsider. Most attacks stay invisible until it’s too late.
Keep your security settings tight
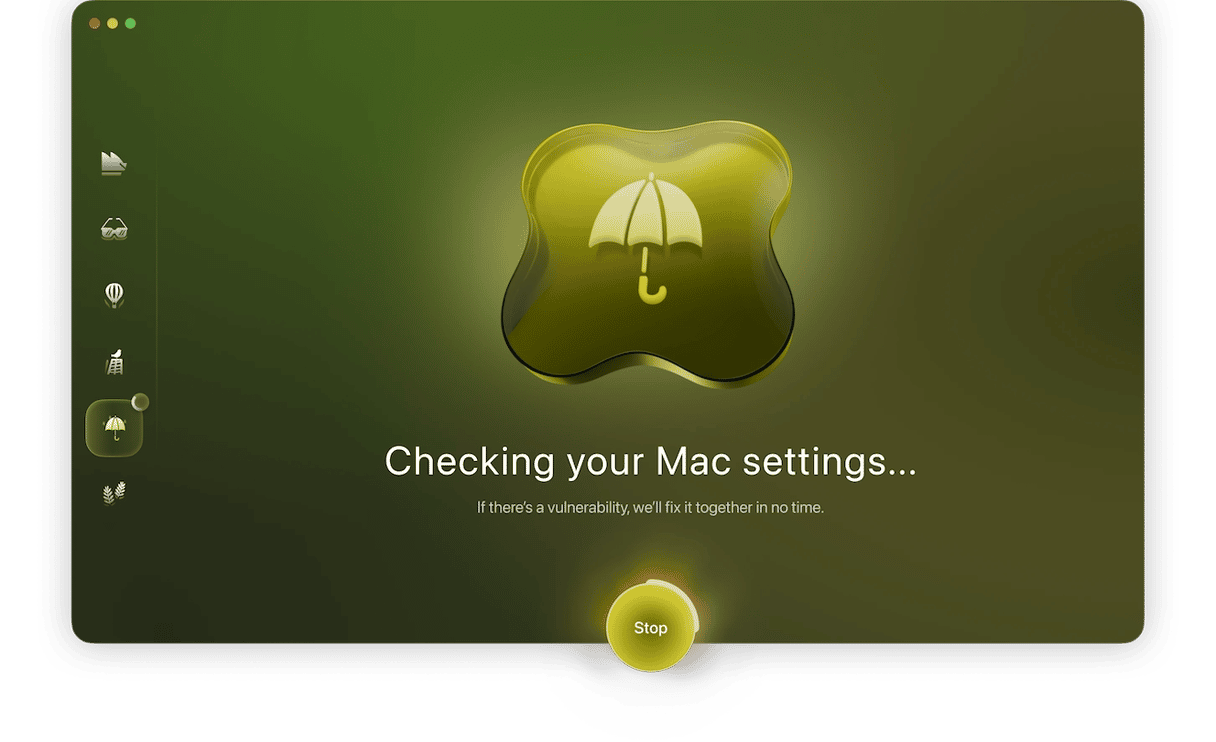
Rootkits take advantage of gaps in your security settings, so make sure every one of them is airtight on your Mac. You can research Mac security tools yourself, or try Moonlock’s System Protection. Here’s how it works:
- Open Moonlock
- Select System Protection in the sidebar.
- Click Run to let Moonlock check all macOS settings affecting your online security.
- Moonlock will prepare a list of settings that need attention, each with step-by-step instructions tailored to your macOS version.
- At the end of each instruction, click Send for Check. This will queue the setting for the next security review.
- Hit Check, and Moonlock will verify your new configurations. If everything looks good, you’ll see the settings you just worked on are marked as Done.
Think before you click
Malware often starts with a single click. Hackers hide infected links in emails, texts, or social posts that look familiar or urgent. If something feels off — pause. A few extra seconds of doubt can save your Mac from a world of trouble.
Use anti-malware app with instant detection
Apps like Moonlock have real-time protection that can prevent rootkits from installing. No matter how it’s delivered, once a rootkit reaches your Mac, Moonlock sends it to Quarantine and stops malware in its tracks.
Rootkit malware is so-called because it attacks the root of a computer system. That could be the BIOS, the bootloader, or even the RAM. The macOS rootkit Thunderstrike exploited a vulnerability in Thunderbolt firmware to install itself. Once installed, rootlets can do all sorts of damage.
Remember, scanning your Mac regularly for malware and using privacy cleaning tools minimizes the chances of being caught in a rootkit malware attack.