Macro viruses are one of the oldest types of viruses to hit personal computers. They are designed to look like or take the place of automated scripts known as macros that run in some of the most widely-used software. Because they are written in the same language as macros, they can replace regular commands and run in any program when the command is selected. That’s how they may infect your Mac. Here, we’ll tell you how to deal with a macro virus.
What is a macro virus?
Before we define the term “macro virus,” let’s first clarify what a macro is.
A macro is an automation inside a program designed to automatically carry out predetermined tasks. Some examples of common macros are found in Microsoft Office programs, such as Word and Excel, but they can be found in many other programs as well.
The creator of these macros can be the software developer (such as Microsoft) or the user. But third parties can also develop macros, and this is where a macro virus can come into the picture.
A macro virus is malware code that is placed inside a macro to perform a specific task once it’s released onto a target computer. This task may be something like deleting files, corrupting files, sending spam emails, or stealing the user’s private data. Macros don’t discriminate between different operating systems. They affect Windows and macOS alike, making them a threat to everyone.
What makes a macro virus so effective is that it can be embedded in a document, and when that document is opened, the macro runs automatically. They can also be stored on the target computer, where they would have access to other document files.
Another reason why they’re so effective is because the creator can disguise the malware as a useful, seemingly harmless function. This can lure potential victims into a false sense of security, leading them to download it without realizing its true nature.

Why are macro viruses hard to detect?
There are several reasons why macro viruses are so difficult to find and destroy.
Usually, malware is a very active entity. Once on a computer, it gets busy, connects to an external server, and consumes large amounts of CPU and memory. This often makes it clear to the user that something is wrong.
A macro virus, on the other hand, will remain dormant until the macro is run. There’s no outward sign of it being there, so the user won’t know to scan for it. Plus, if the malware code is not active, an antivirus program could very well miss it completely.
Another difficulty in detecting macro viruses is that there are many legitimate macros made by honest and ethical developers. Their code is obviously harmless, but distinguishing between a legitimate macro and a malicious one can be difficult for some antivirus software.
Finally, like any other types of malware, macro viruses are always changing and evolving. Antivirus software may be looking for one version even as a new, unknown “zero-day” version is present instead.
This means antivirus apps have to keep up to date with all new known threats, and their databases must be continually updated. If developers are a bit slow with this, macro viruses may initially go undetected.
Which programs are most vulnerable to macro viruses?
So, which programs are most susceptible to macro viruses? The main category is office software programs, but macro viruses can also appear elsewhere.
If you use any of the following, take extra special care — especially if you’re installing macros yourself.
Microsoft Office (Word, Excel, PowerPoint): Macros are used quite frequently in Office documents to automate routine tasks such as formatting, spreadsheet calculations, and adding standard elements to documents before generating them.
This is a fertile ground for macro viruses, which can be embedded inside a document to run when the document is opened.
Open Office and LibreOffice: These are the free, open-source alternatives to Microsoft Office, and macros work in these programs in much the same way. Since these two programs are free, their user base is increasing, thereby making them increasingly attractive targets for hackers and malware writers.
AutoCAD: This is another example of a non-Office app that can run macros (and, therefore, is prone to macro viruses).
CAD stands for Computer-Aided Design, and the purpose of the program is to make 2D drawings and 3D models, such as blueprints and schematics. A macro can aid the user by automating repetitive tasks.
Gaming: You may not realize that games also have macros to help the player quickly perform actions with their game character. This risk factor is somewhat lessened these days by the fact that more and more games are launched online through platforms like Steam.
Specialized industrial software: One form of software that relies on macros and would be the prime target for macro viruses is specialized software used by certain industries, such as the manufacturing industry.
This type of software works in tandem with assembly lines and robots to assist in routine tasks. A macro virus could throw the entire industrial process into chaos.
How macro viruses work and spread
So, how do macro viruses work, and how do they spread?
- The malware is embedded inside the document by the malware maker. It can either be completely hidden or made to look like a harmless, legitimate function.
- Documents embedded with macro viruses can also be mass-emailed to users. Some of them will open it if the email is convincing enough.
- Other delivery methods can include removable drives such as USB sticks and infected document templates.
- Once the document is open, the malware can be triggered to automatically run in the background without the user realizing it. Or it can wait until the user runs it themselves.
- Once run, the macro gets to work and starts stealing data, corrupting files, and generally causing havoc.
How do I know if my Mac has a macro virus?
There are several possible symptoms:
- Unexplained behavior, such as a document asking for a password when it wouldn’t normally do so.
- Unusual dialog box messages.
- Changes to documents that don’t make sense.
- Menu items missing from the host program.

How to avoid getting a macro virus
- Don’t open email attachments
If you see Word, Excel, or PowerPoint documents attached to an email you received, don’t open them unless you are certain about what they are and where they came from.
- Avoid downloading suspicious files
Don’t download files from the internet unless you are certain they are safe. Also, make sure you download certified software for your Mac.
- Make a habit of scanning your Mac regularly
There are many anti-malware tools that can help you check your Mac for macro viruses and remove them. The app we mentioned before, CleanMyMac, does a great job scanning macOS and revealing malware and viruses that may have infected your machine.
- Treat files that are given to you on removable media with care
If possible, scan them for malware before you open them and, especially, copy them to your Mac.
- Pay attention to warnings
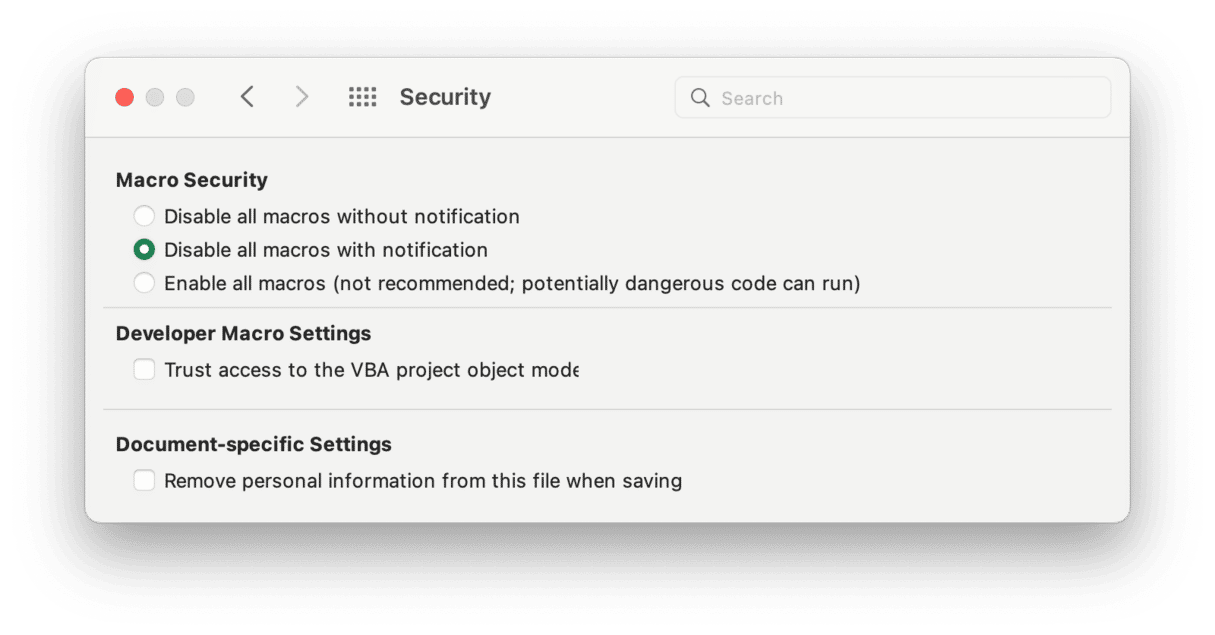
Word and Excel will warn you if a document you open contains a macro. Don’t ignore the warning. If you weren’t expecting the document to have a macro, or you don’t need to use it, choose the option to disable macros. To enable warnings, go to Preferences > Security.
How can I get rid of a macro virus?
Macro viruses can be difficult to detect, so prevention is much better than cure. That’s why it’s important to follow the steps above to avoid getting one in the first place.
If you do find that you have a macro virus, it’s important that you deal with it straight away. Don’t send any files to anyone if the app they run supports macros. And don’t copy them to external media or upload them to the internet; otherwise, you risk spreading the virus.
The only effective method to remove the macro virus from your Mac is to use anti-malware tools that work for you. But, be cautious here: don’t download the software unless you’re sure it’s safe. For example, CleanMyMac is notarized by Apple, which proves it is an app you can trust.
Here’s how to use it:
- Start your free CleanMyMac trial.
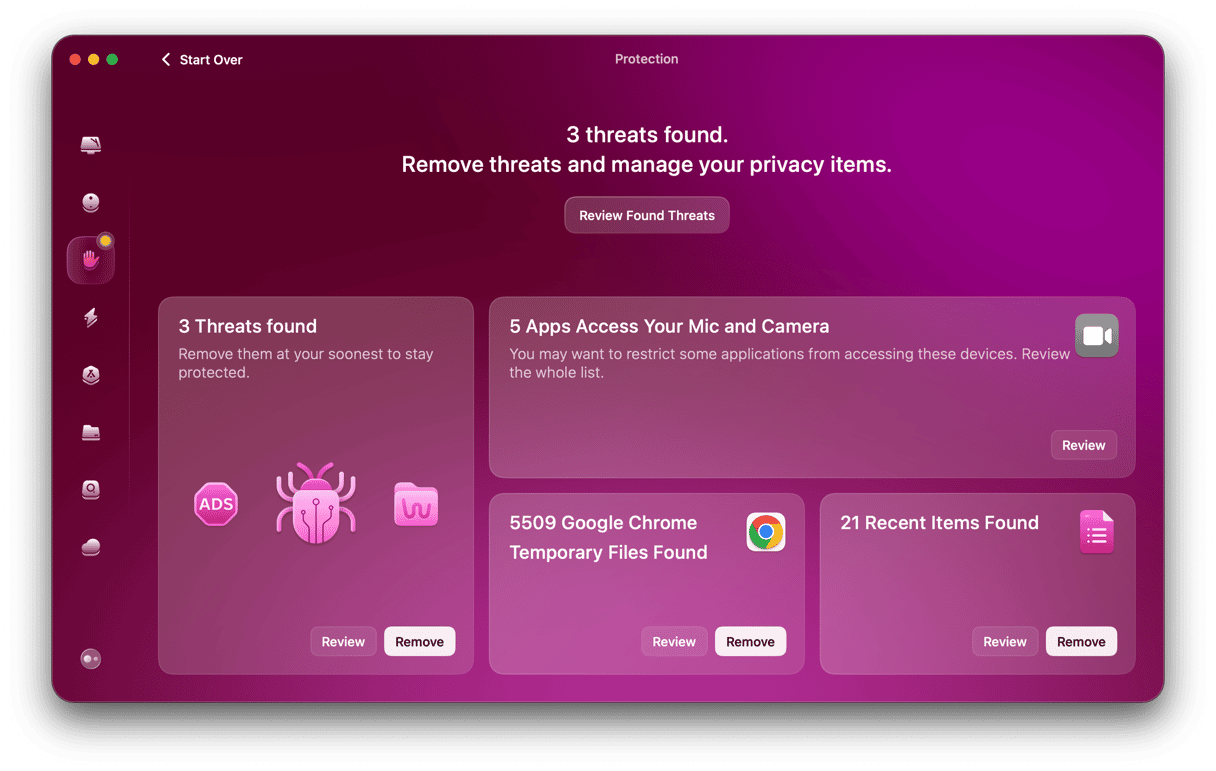
- Select Protection and hit the Scan button.
- CleanMyMac will start checking your Mac for malware. If anything is found, click Remove to get rid of it.
- Now, you can turn on a real-time malware monitor. Click on the Configure Scan.
- Find the Malware monitoring configuration and check both boxes to turn on real-time protection.
What else should I do?
Trying to remove suspicious apps manually can be time-consuming and ineffective, as some files may be hidden deep within your system. CleanMyMac can help with this task too! Here’s how to do it:
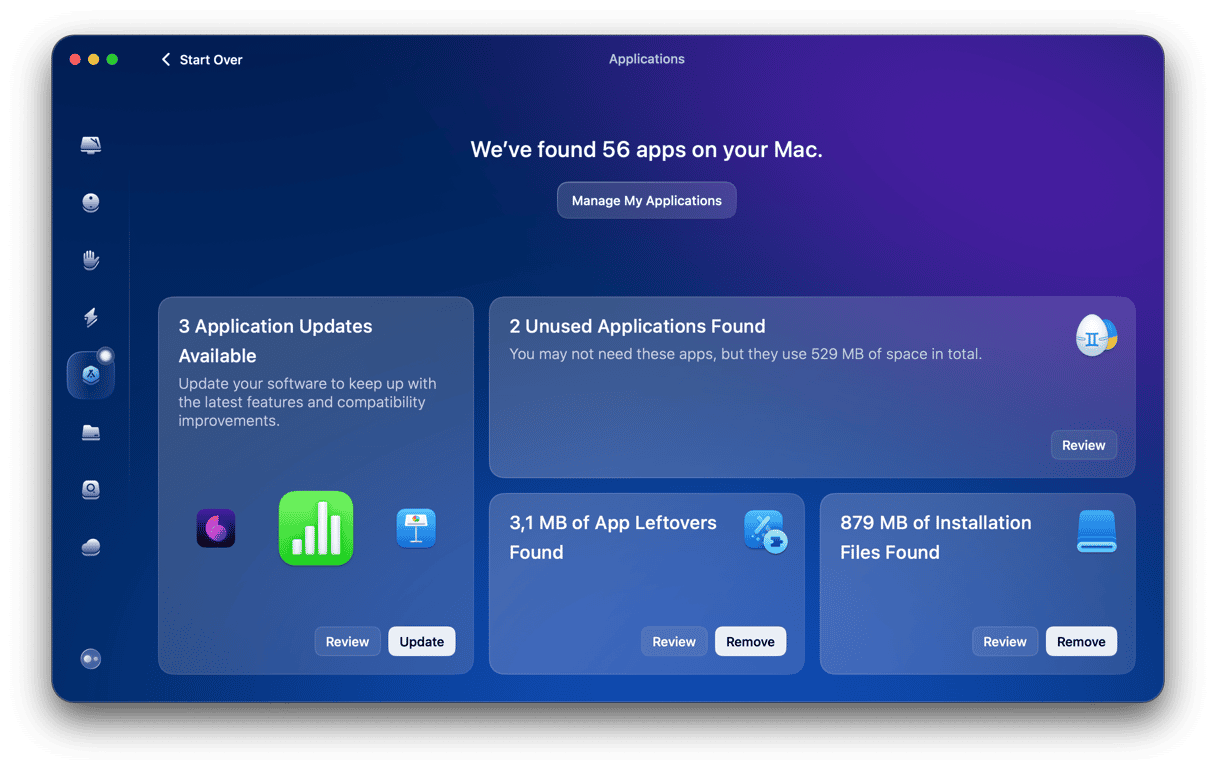
- Open CleanMyMac and go to Applications > Manage My Applications in the sidebar.
- Browse through your installed apps. If you’re unsure about a program, check the Suspicious tab
- Select the app you want to remove and click Uninstall to delete it with all associated files.
Common examples of macro viruses
It’s easy for us to quote theoretical scenarios, but it’s more effective if we use actual real-world events. We’ll end by profiling 3 examples of past macro viruses to illustrate their impact when they came out.
Melissa (1999)
We’ve already mentioned Melissa in this article. This was arguably more damaging and traumatic than other macro viruses because back in 1999, computer users didn’t have as much experience with malware. Melissa was a rude awakening. At a time when a lot of people used desktop email providers such as Outlook, the spreading of the macro via email contact books was particularly brutal.
ILOVEYOU (2000)
No sooner did Melissa provide users with a rude awakening to macro viruses than the next example made its appearance. The ILOVEYOU macro virus, like Melissa, was a document (made to look like a love letter) that, once it was opened, caused malware to jump into the victim’s contact book and travel on.
Nimda (2001)
The next year saw the next macro virus. Just as people were starting to get wary about opening email attachments, Nimda started spreading through email attachments and networks. Its prime mode of transport was Microsoft Office, taking advantage of various security vulnerabilities.
What are the risks of a macro virus?
When a macro virus gets out into the wild, it can cause immeasurable damage. It can cause damage to files, computer networks, business processes, a person or company’s reputation, company revenue (which could lead to job losses), and so much more.
The following lists the kind of damage a macro virus can cause.
Data theft
The main reason malware exists is to get into networks and start scooping up as much valuable data as possible. The theft of this data can be devastating if it’s proprietary and a company depends on it for its livelihood.
File corruption and deletion
This could be an intentional action conducted by the malware or an accidental side effect. If intentional, it could be seen as a direct attack on a person or company (such as corporate espionage). Or, in the process of stealing files, other files may get damaged along the way.
Performance issues
All malware takes up system resources. Once it springs into action, the process of collecting data, burrowing deep into a device, and exfiltrating that data will consume large amounts of CPU and memory. This means the legitimate processes on the machine will take a huge hit in performance and speed.
Interfering with software updates
If a macro virus is slowing your computer down, then normal processes like software updates may be affected. This is ironic because if the macro depends on a software vulnerability, not being able to add an update patch to that software — because of a macro virus — actually helps the malware!
Unstoppable virus spreading
As seen in the Melissa macro virus in 1999, once a macro virus gets going, it can be extremely difficult to stop. It can jump from network to network, machine to machine, and keep going by emailing itself to its victims’ contacts. In this way, a macro virus can last for years and cause untold damage.
Damage to the victim
There are sometimes real-world consequences, especially if the victim is a company. For example:
- Networks may need to be shut down.
- Files with important information could be corrupted and made unrecoverable.
- Expensive machines could be damaged beyond repair and need to be replaced.
- Emails and their attachments could become unable to be opened. This can lead to invoices not being paid, customer queries going unanswered, and more.
- Robots on production lines and other automated process, which depend on software to run them and provide instructions, can stop working, causing production to grind to a halt.
- Reputational damage can occur due to a company or individual not delivering on a product or promise or by forwarding the malware. This can lead to revenue loss and job losses. A company could completely go under.
Macro viruses are spread in documents that run in applications that support macros, such as Microsoft Word and Excel. The virus is embedded in the document itself and usually spreads via email attachment or over a network. When the document is opened, the macro runs automatically, infecting the host computer. So, it’s important you only open attachments from trusted sources and only enable macros on documents you’re sure are safe. Don’t forget to run regular malware scans to remove malware if you think you’ve been infected.