What’s helpful and convenient for us is also handy for those who would do us harm. One such thing is remote access — while we use to be more productive, hackers and cyber criminals rely on it for stealing our private data. But worry not, this article, we’ll explain how to tell if your Mac has been remotely accessed and what you can do to prevent it.
What does it mean if Mac is remotely accessed?
If a Mac is remotely accessed, it means that you or someone else can control it even if not in physical contact. There are lots of reasons why you may want to legitimately access your Mac remotely. Some people, for example, use a Mac mini as a ‘headless’ server and remotely access it to control it. System administrators may remotely access your MacBook to set it up or troubleshoot issues.
But the reasons are not always legitimate since remote access can be a part of remote hacking scams — a common cyber threat. In this case, cybercriminals want to steal your personal information, delete data from your computer, install tracking software, or even spy on you.
Can my Mac be remotely accessed?
All Macs have the potential to be remotely accessed. And that’s a good thing. The real question is, ‘Can my Mac be remotely accessed without my permission?’ The answer to that is more complicated and is certainly not a simple ‘No.’
How to tell if your Mac has been remotely accessed
There’s no simple way to tell if your Mac has been remotely accessed. On some occasions, the signs may be obvious:
- The mouse pointer moves without you touching the mouse or trackpad.
- You see intrusive pop-up windows that look suspicious.
- You may see a message from a hacker demanding some kind of ransom.
- You may be locked out of your Mac altogether.
But, in most cases, there only a few telltale signs you can look out for and a few things you can check.
1. Check notifications
Have you had any unusual notifications recently? macOS will tell you if another computer accesses yours using screen sharing or file sharing. So, if you see a message like that, don’t ignore it. Other software, like TeamViewer, for example, will also tell you if another computer is accessing your Mac. So, don’t ignore those notifications.
2. Scan your Mac for malware
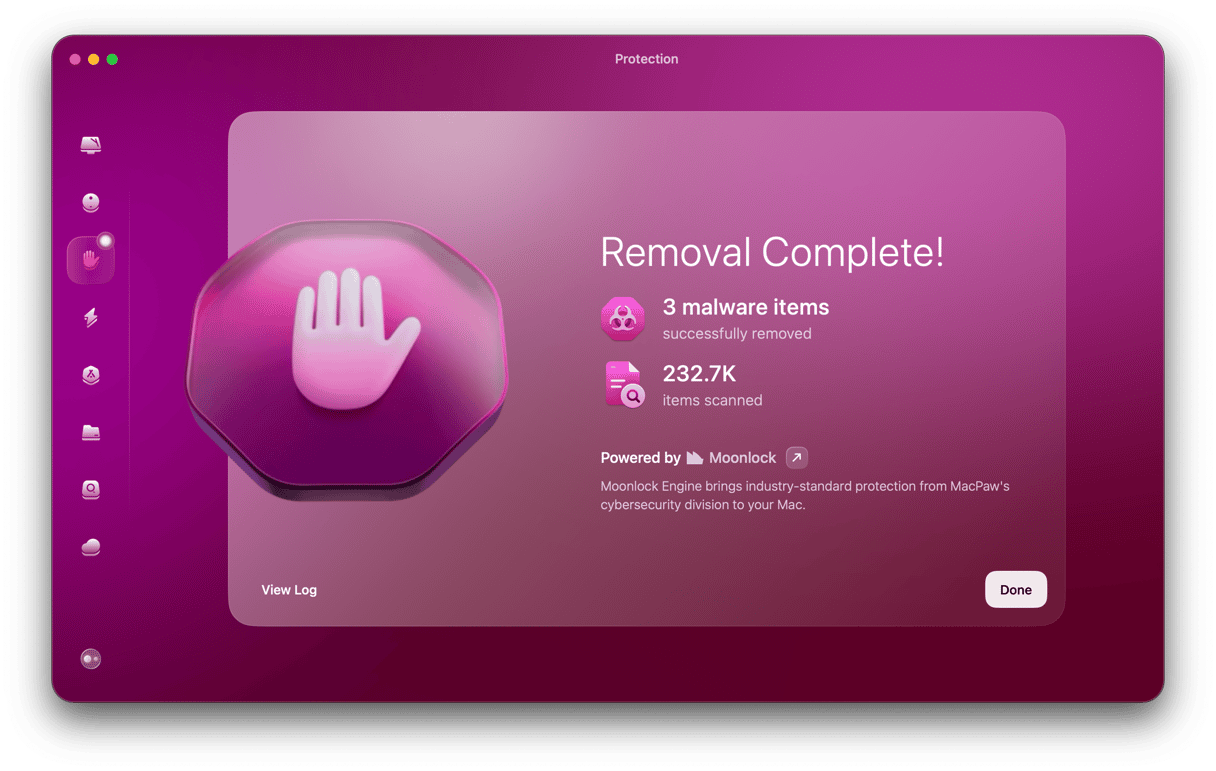
The only way to know for sure that an intruder hasn’t installed anything nasty is to scan your Mac for malware using a specialist tool. We recommend CleanMyMac’s Malware Removal tool (found within the Protection feature).
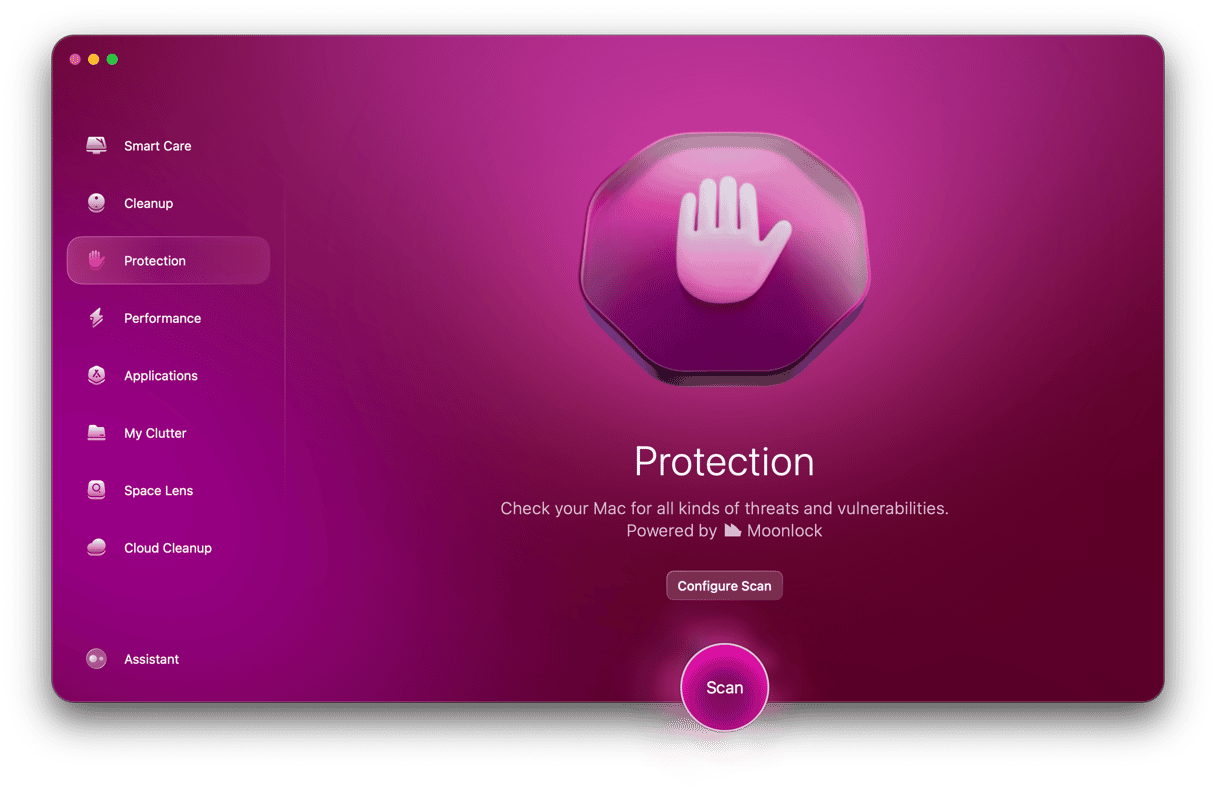
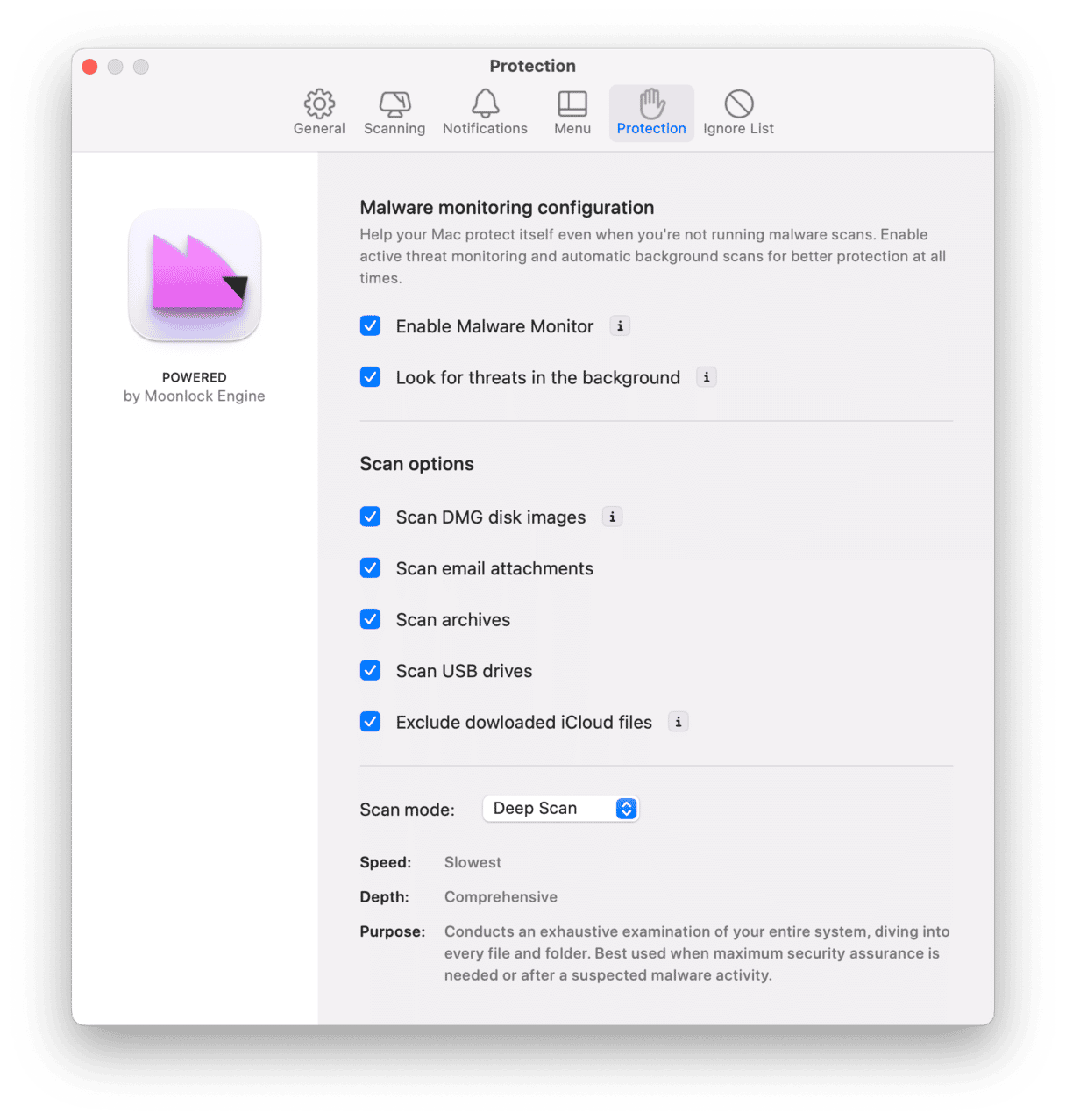
It scans your Mac, looking for adware, ransomware, cryptocurrency miners, and other malware. You can choose whether you want it to run a deep scan, a more balanced scan, or a light scan by clicking Configure Scan. The deep scan is more comprehensive but also takes longer. However, if you suspect your Mac has been accessed remotely, it makes sense to run this one.
Once CleanMyMac has finished scanning, it will tell you if it has found anything suspicious and allow you to remove it with a click. Get started with a free CleanMyMac trial. Once you’ve done that, follow the steps below.
- Open CleanMyMac and choose Protection in the sidebar.
- Click Scan.
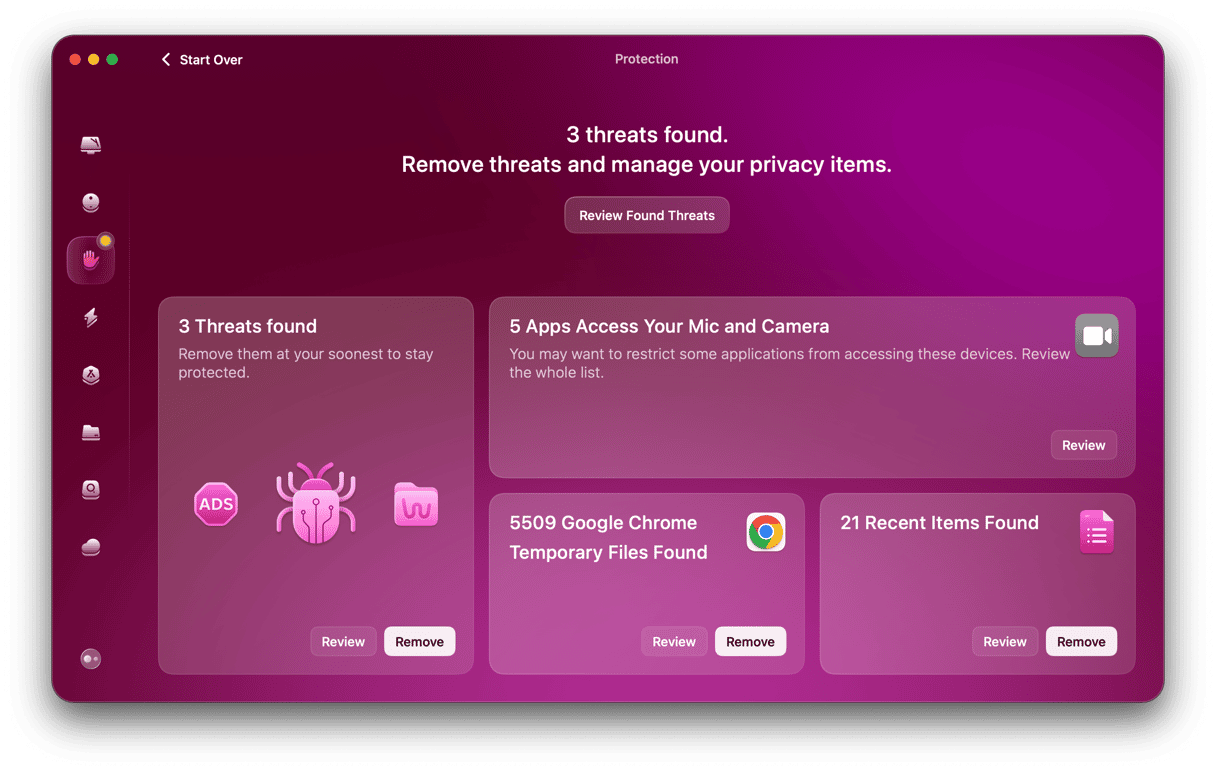
- If the scan finds any malware, follow the instructions on the screen to remove it.
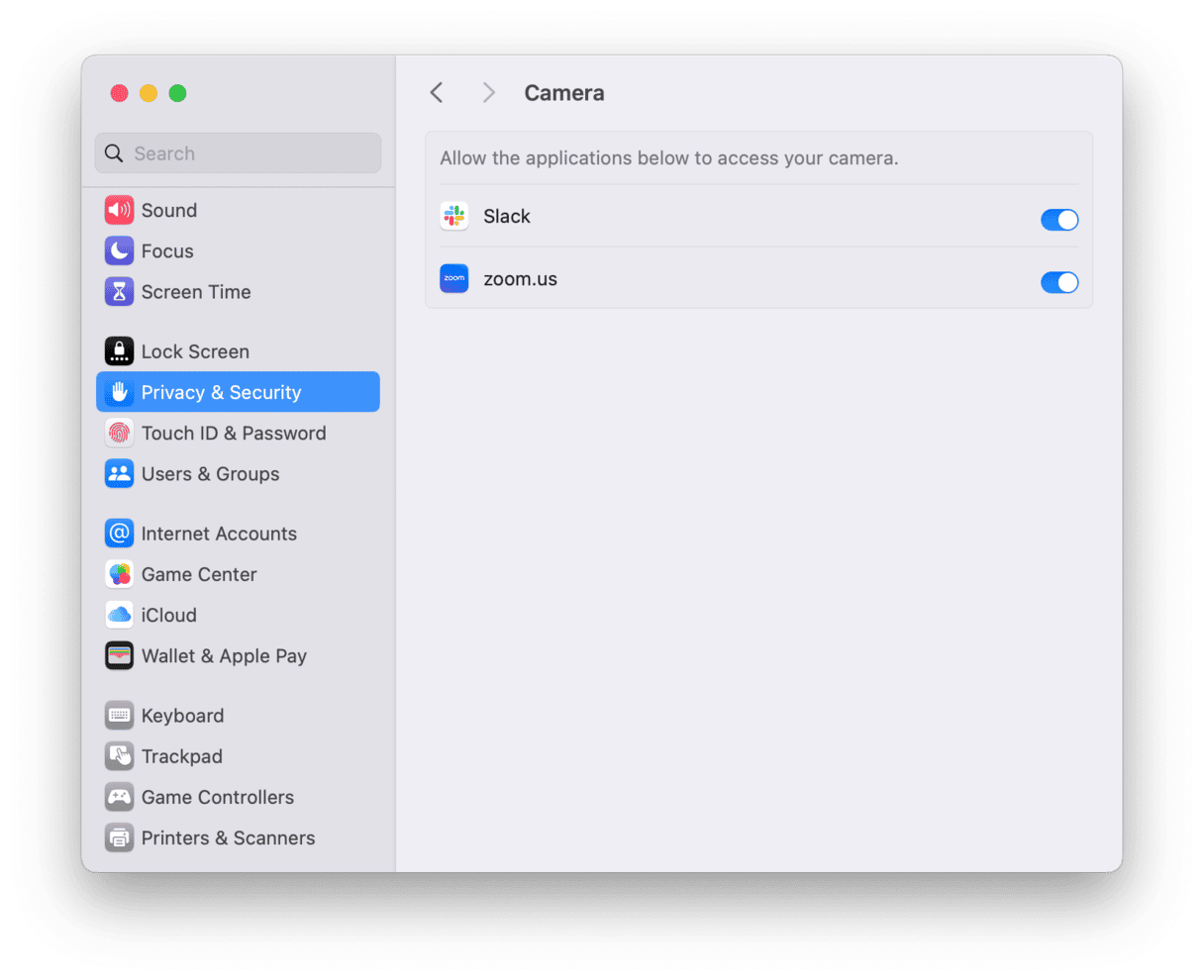
3. Look for camera light
Does your camera light come on when you’re not using it? That could be a sign someone has accessed it remotely. If you suspect anything, go to System Settings > Privacy & Security and check which applications have permission to access your camera. If there are any listed that you don’t recognize, revoke their permission. If you don’t use the app or didn’t install it, remove it completely from your Mac.
4. Check your Mac's performance
Is your Mac running more slowly than normal? If so, that could be a sign that there are processes running in the background that you’re not aware of, possibly controlled by someone who has accessed your Mac remotely.
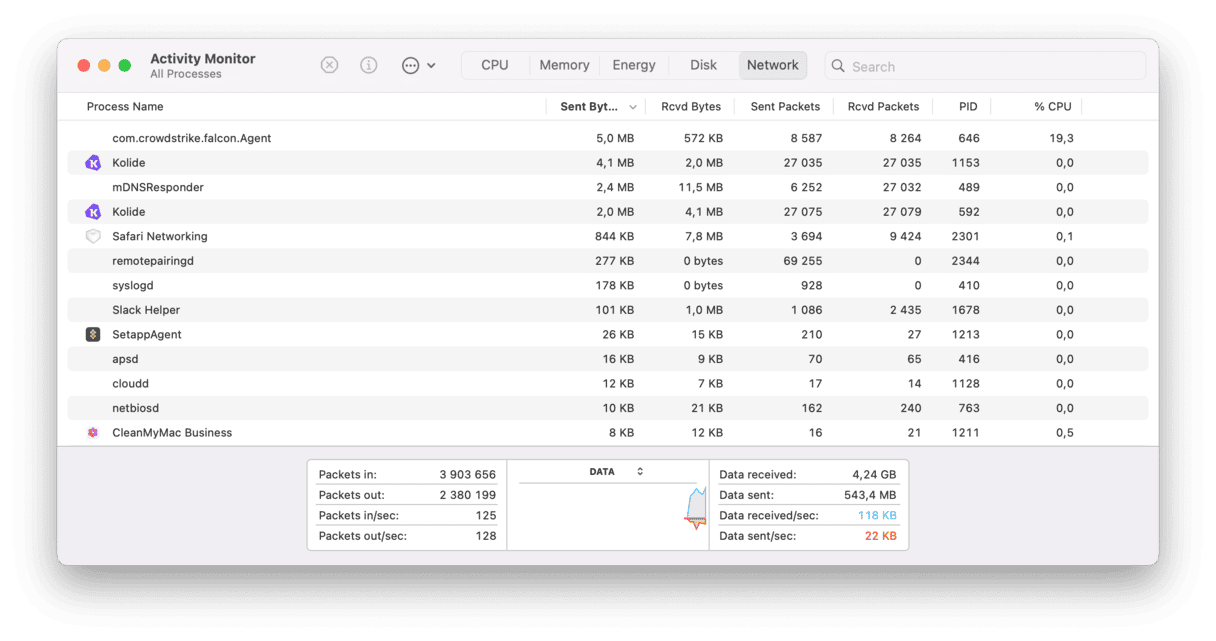
5. Check running processes
You can use Activity Monitor to do it. It lists every process currently running on your Mac, including those triggered by malware or used to access your Mac remotely. Most of them have names that make it difficult to know what they do or which application is running them. But checking Activity Monitor can be useful because it will make it clear if there are any processes hogging resources. And malware is often guilty of doing just that.
- Open Activity Monitor.
- Click the Network column header to see what processes are currently using network bandwidth and order them according to the bandwidth they are occupying.
- Do you see anything suspicious? If there are lots of processes listed, it might be a good idea to quit any running web browsers so that you can focus on network activity that may be unauthorized. If you see any processes that look suspicious, Google their name to find out more about them. If your suspicions are confirmed, select the process and click the ‘x’ in the toolbar to quit it. You should then remove the application that was running the process. Repeat the same for the CPU and Memory tabs.
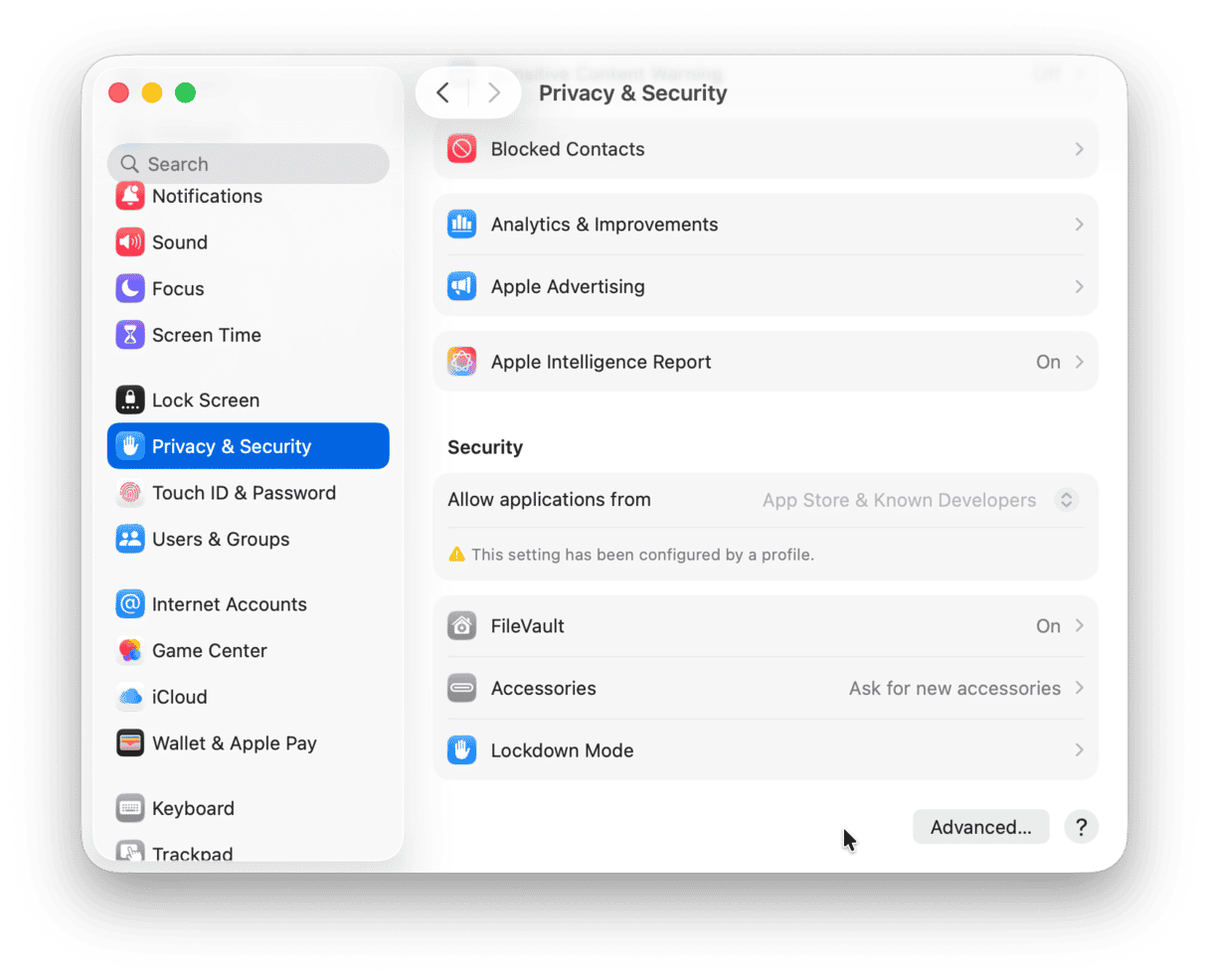
6. Look for settings that have been changed
One way that an intruder may have invaded your privacy when they accessed your Mac remotely is to change your Privacy & Security settings. For example, they may have given permission to apps to access your Mac’s camera or microphone or to record its screen. You should open System Settings and go to Privacy & Security settings.
Go through each section one at a time and review permissions and settings, making sure they are as you want them to be. As well as camera and microphone, pay particular attention to Full Disk Access, Files and Folders, App Management, Automation and Passkeys Access for Web browsers.
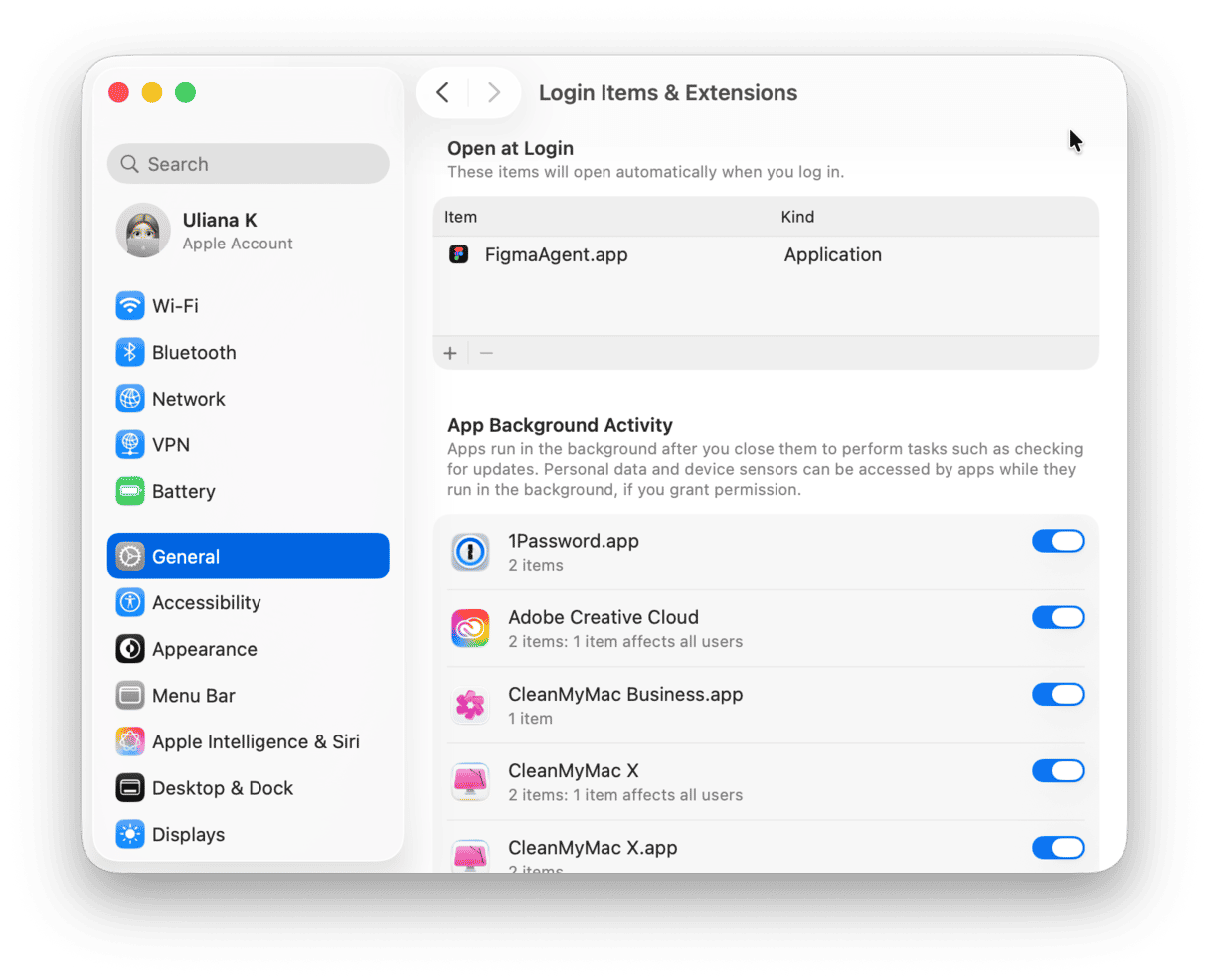
7. Check login items and extensions
Another area where an intruder may have changed things is in System Settings > General > Login Items & Extensions. By installing an extension and enabling it to run in the background, they may have attempted to install malware in the future or steal more data.
Check what login items and background extensions are enabled and make sure you know what they are and what they do. If there are any that seem suspicious, disable them.
How to prevent your Mac being remotely accessed
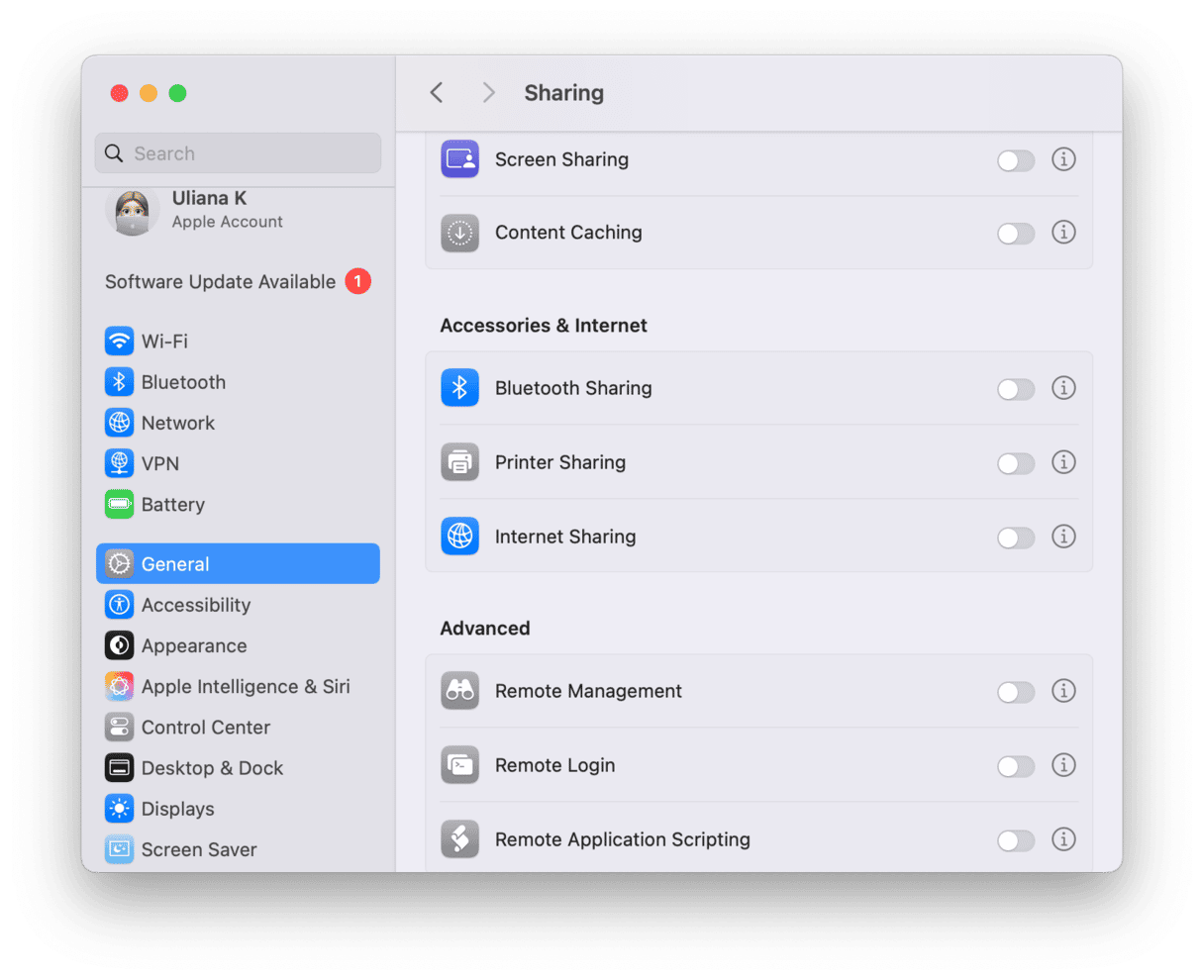
1. Turn off Remote Login and Remote Management
It’s very useful to be able to log in to manage your Mac remotely. However, if you don’t need to use those features, you should keep them switched off. Go to System Settings > General > Sharing. Switch Remote Login and Remote Management off if they are on. If you need to use them and want to keep them switched on, click the ‘i’ and set security so that only users you specify can request access or log in remotely.
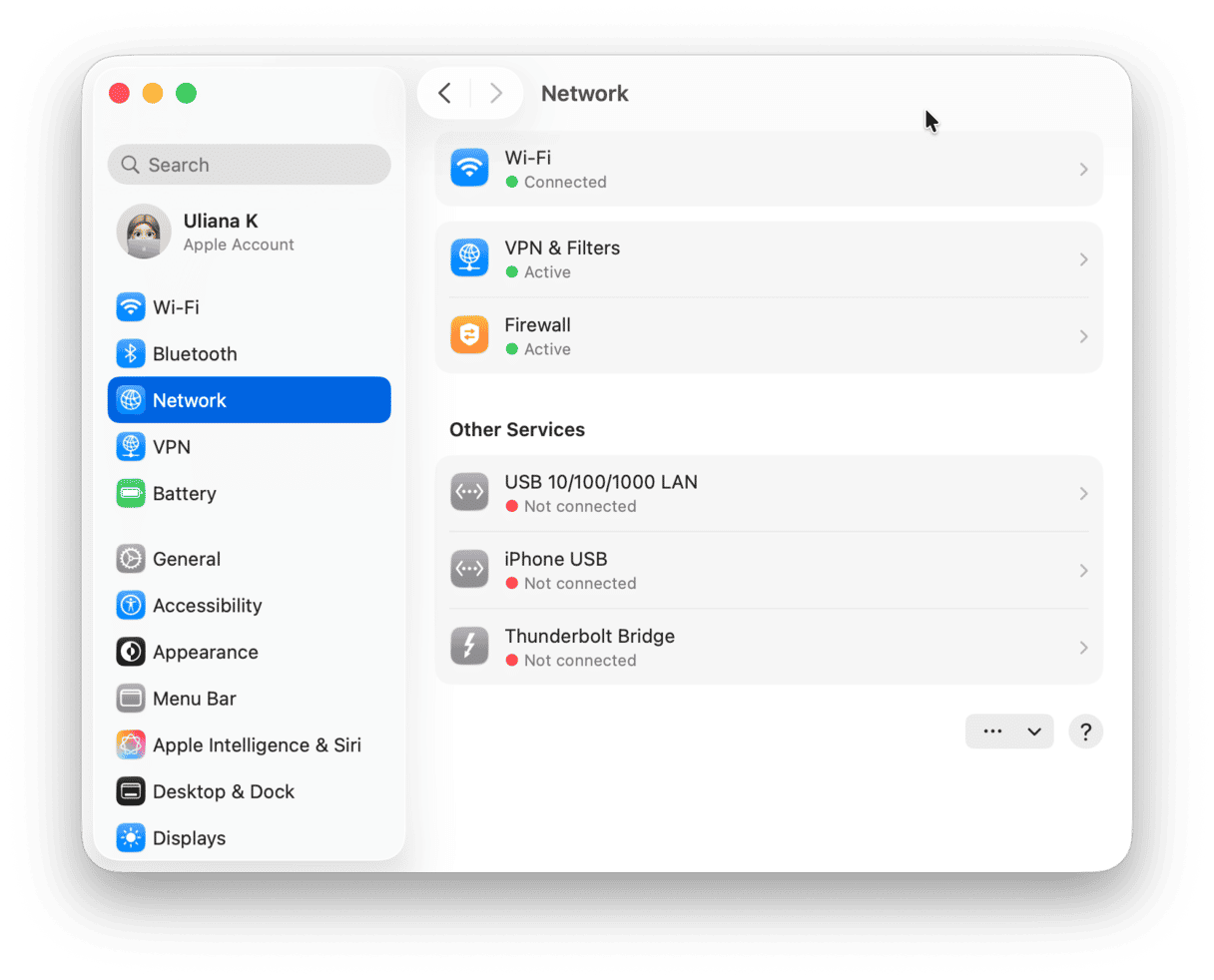
2. Check the firewall settings on your Mac and router
The Mac’s firewall settings are in System Settings > Network. Make sure Firewall is set to on. Then click Options to configure access for incoming connections. If you’re worried about someone accessing your Mac remotely, you can block all incoming connections. Your router’s firewall settings will be on its admin page. The IP address for that will be in its manual or on a sticker on the back or bottom. There should also be a default login name and password. Once you’ve logged in, look for the firewall settings.
3. Don’t connect to unsecure public Wi-Fi networks
Your Mac should warn you if the network you’re attempting to connect to isn’t secure. Don’t ignore the warning. Connect to a different network or use your phone as a hotspot.
4. Scan regularly for malware
One way that intruders may remotely access your Mac is by tricking you into downloading malware, which then changes settings to allow them access. To avoid this, you should always be very careful about clicking links in emails, messages, or on websites. And never download anything unless you are certain what it is.
However, that alone may not be enough. So, it’s a good idea to use software to monitor the files you download and install and check them for malware. We recommend CleanMyMac’s malware monitor. As well as scanning your Mac when you trigger a scan manually, you can configure it to monitor files on an ongoing basis. If it finds anything suspicious, it will alert you and allow you to remove it easily.
- Get your free CleanMyMac trial.
- Open CleanMyMac, choose Protection, and click Configure Scan.
- Select Enable Malware monitor and Look for threats in the background.
- Make sure all the options under Scan options are checked. Close the window.
- CleanMyMac will now monitor your Mac in the background and look for threats. If it finds anything suspicious, it will alert you and allow you to remove it. You can check if you’re protected by clicking a little iMac icon in the menu bar.
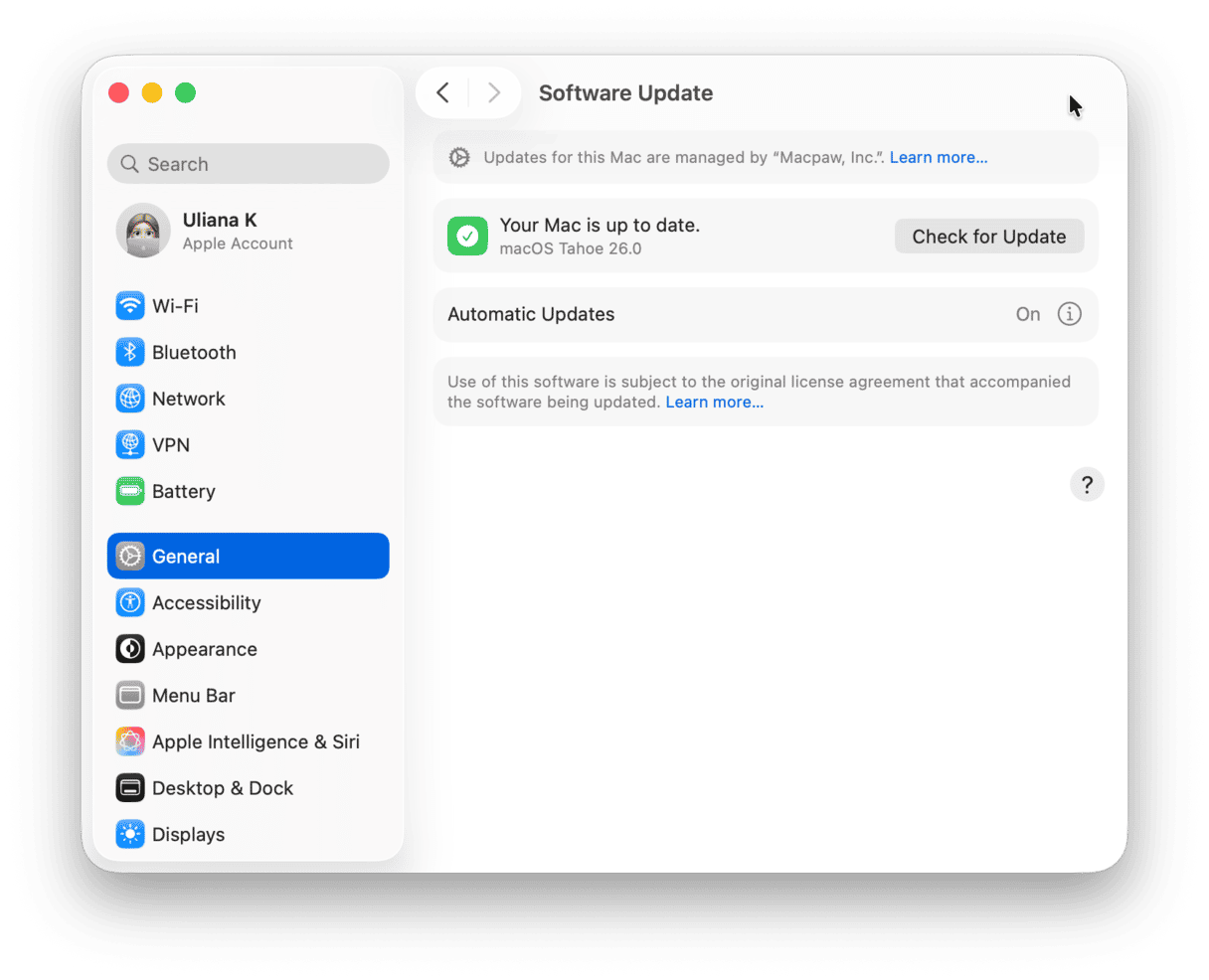
5. Keep macOS up to date
It’s possible that your Mac has been remotely accessed because of a flaw in macOS, and that flaw has been fixed in a recent update. By keeping macOS up to date, you can make sure that you will be protected as soon as the fix is available:
- Go to System Settings > General > Software Update and wait for it to check.
- If there is an update available, follow the instructions on the screen to install it.
- Click the ‘i’ next to Automatic Updates and make sure everything is set to on.
Macs are safer and more secure than they have ever been, thanks to recent improvements in macOS and hardware additions to Macs with Apple silicon. However, they are not impenetrable, and there have been flaws reported in Apple technologies in the recent past. If you are concerned that your Mac has been remotely accessed, there are several things you can do to check it. Follow the steps above to find out for sure and to repair any damage they may have caused. Then, follow the steps to prevent your Mac from being remotely accessed in the future.